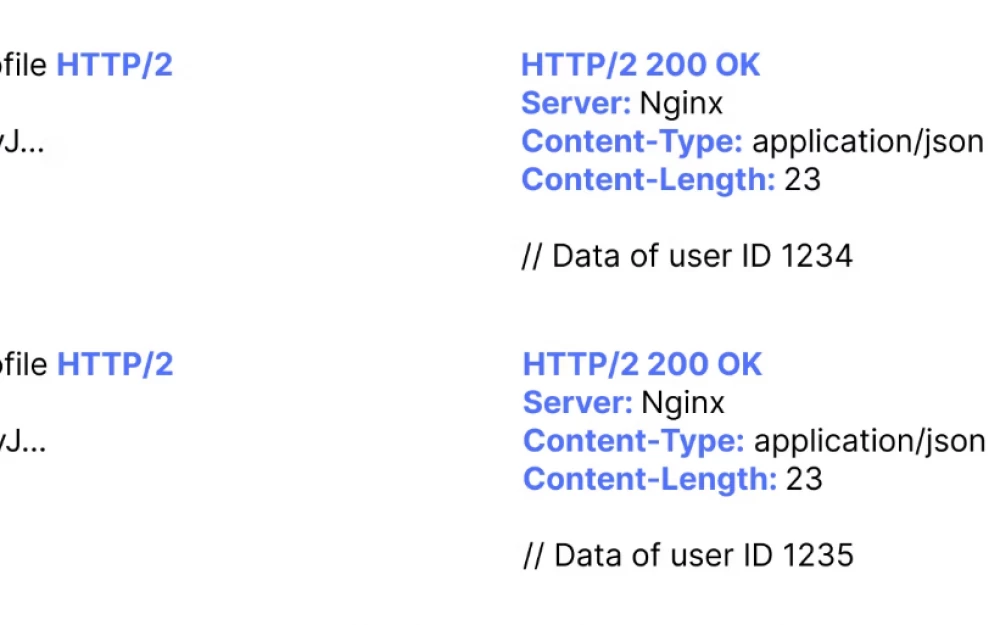
According to the tag exploit, the following results have been found:
IDOR vulnerabilities are among the most common security vulnerabilities in modern web applications and APIs. It is not surprising that they are often recommended to novice vulnerability hunters, as they are easy to find and exploit, and by their nature, they are high-severity vulnerabilities.
tekkix, hello! I am Alexander Leonov, leading expert of the PT Expert Security Center laboratory. Every month, my team of analysts at Positive Technologies researches information about vulnerabilities from vendor security databases and bulletins, social networks, blogs, telegram channels, exploit databases, and public code repositories, identifying trending vulnerabilities in all this diversity. These are the vulnerabilities that are either already being exploited or may be exploited in the near future.