- Security
- A
Do we allow our applications too much?
Many people have photos of their passport, driver's license, and child's birth certificate on their phone. But not everyone realizes how easy it is to access them. One permission granted to an application can lead to data disclosure. We studied the 50 most popular Android applications and found that most of them want to get an unreasonably large number of permissions. Let's figure it out.
The Cybernews research group found that for many popular Android apps, which on average require 11 potentially dangerous permissions, it is not enough to just have access to the user's location, files, or camera.
And although developers make every effort to protect users from threats, just one data leak can lead to the disclosure of personal data of millions of people.
Methodology
The Cybernews research group selected the 50 most popular apps in the Google Play store and analyzed their Manifests to determine what dangerous permissions these apps request.
Every Android app has a Manifest file, which is a set of rules that tells the device what the app can access. There can be a total of 41 "dangerous" permissions that can affect the user's privacy or the core functions of the phone.
Dangerous permissions provide the application with additional access to certain data or actions that significantly affect the system and the user's confidential data. Not all of them are widely used, and some overlap. For example, if an application tracks "precise location," it may not need the "approximate location" permission. Some niche functions, such as adding voicemail, are not requested by top applications.
Common development rules require developers to request the minimum number of permissions — that is, only those that the application needs to perform a specific action.
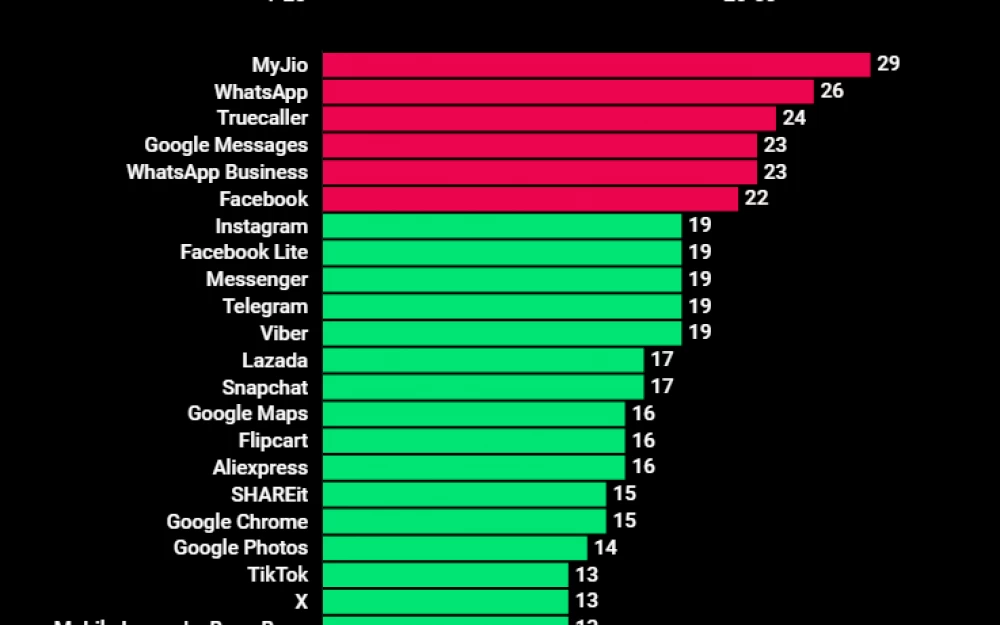
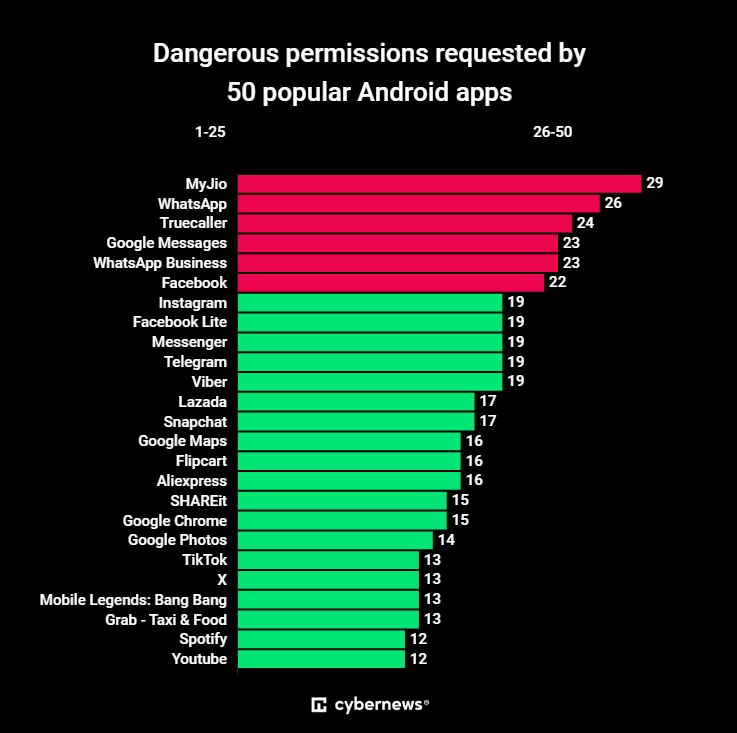
Which applications request the most dangerous permissions?
The MyJio: For Everything Jio application is developed by a popular telecommunications and digital services provider in India. It offers various services such as payments, cloud storage, streaming services, and more.
The application requests almost all possible permissions: location, activity recognition, radio, camera, microphone, calendar, file access, etc. In total, the application requests 29 permissions, which puts it at the top of our list.
WhatsApp, a popular messaging and video calling application, ranks second and requires 26 permissions.
Many Android phones have Truecaller: Caller ID & Block — an application for checking caller ID and blocking spam calls. It requests a total of 24 dangerous permissions.
Next are Google Messages and WhatsApp Business, each requesting 23 dangerous permissions, followed by the social networks FaceBook (22) and InstaGram (19).
At the other end of the list is Among Us, a multiplayer game that did not require any dangerous permissions. Candy Crush Saga, 8 Ball Pool, and some other popular games also often required only 1 or 2 dangerous permissions, mainly for sending push notifications. However, fewer required permissions do not necessarily mean that the app is safer.
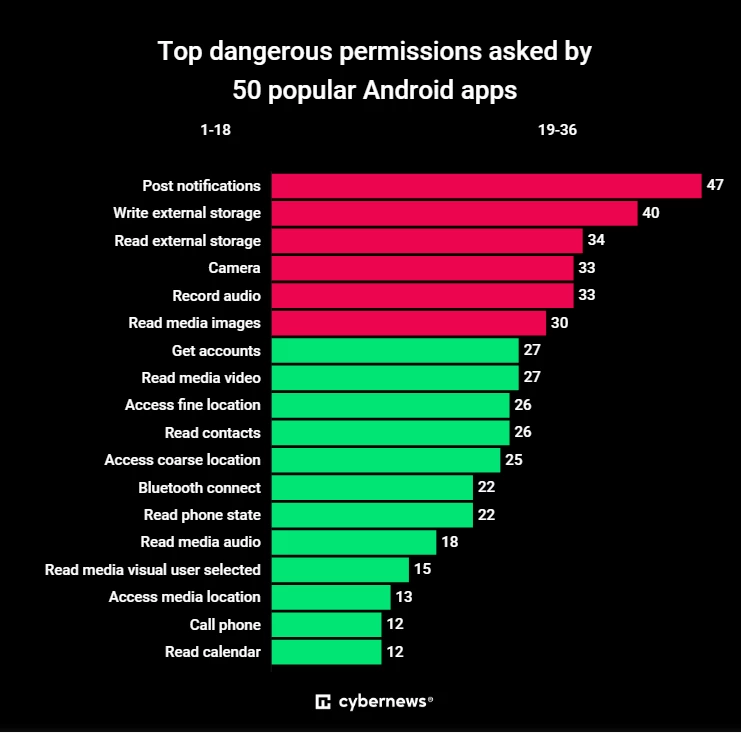
Most frequently requested permissions
Almost all analyzed apps (47) request permission from users to send notifications. While this permission may seem harmless at first glance, it can be exploited in several ways.
"The simplest way to use notifications, which is often abused by malicious apps, is to bombard users with unwanted ads, phishing links, or even misinformation. Notifications were previously used by commercial spyware providers to track users," says security researcher Mantas Kasiliauskis.
In 2023, U.S. Senator Ron Wyden warned in his letter that notifications help government surveillance because they do not go directly from the app to your smartphone and may contain sensitive data. Notifications pass through an intermediary—a kind of "digital post office." For Android phones, this is Google’s Firebase Cloud Messaging.
The second most frequently requested permission is access to storage outside the app's directory. A total of 40 apps request permission to write, and 34 apps request permission to read files from external storage. This means they can access photos of your documents stored on your device.
These permissions are necessary when you upload media content to your profile, share photos and videos on social networks, save pictures and videos. Without them, the social network app will not be able to access your photos, your messenger will not be able to save documents, and your photo editing app will not be able to save the changes you make. However, these permissions are also considered high-risk permissions. The app should clearly explain why it needs access to user data.
Malicious actors can use storage access to extract or compromise files such as photos, videos, documents, and other sensitive information.
Access to the camera and sound recording are the next most frequently requested permissions, required by 33 apps. Camera access is an integral part of the functionality of some apps and allows them to take pictures and then share them. Sound recording is necessary for recording voice messages and other functions. But they can also be abused by malicious actors, spies, and even advertising companies trying to better target their ads.
The "Account Management" permission, requested by 27 applications, allows for easier login with Google and account synchronization. However, in the past, attackers have abused social media login features to hijack accounts.
More than half (26) of the applications also want to track the exact location (accurate to within a few meters). The same number of applications want access to the contact list.
Tracking your location is very sensitive information. While it is necessary for location-based services such as Google Maps, many other applications and games request precise location simply because this data is valuable to advertisers and allows them to show personalized ads.
The same can be said for reading contacts, as they often contain sensitive personal information, including phone numbers, email addresses, and names.
Of the 50 applications analyzed, 22 want "Bluetooth Access," meaning the application can connect to other devices and potentially exchange data with them. This is necessary for interacting with headphones, fitness trackers, or smart home devices.
Twenty-two applications request access to your phone's status. This is a particularly sensitive permission, as it provides access to critical information about the phone's status and its interactions with networks, such as phone number, current cellular network information, current calls, and unique device identifier.
None of the analyzed applications request permission to access body sensors or add voicemail.
Messengers and social networks require the most permissions
Of the 50 analyzed applications, nine belong to the "communication" category, and five to social networks. These categories turned out to be the most data-hungry. Communication applications requested an average of about 19 permissions, while social networks requested an average of 17 dangerous permissions.
All communication applications gain access to cameras and files — most of them record sound, track location data, read contacts and phone status, and also gain access to account management.
Permissions can be justified when they relate to core functions such as messaging, voice messages, and video calls. The lines begin to blur when an application requests access to call management, phone status, and precise location without explicit reasons. For example, if you use a standard phone call application, you might reconsider granting such permissions to WhatsApp or Messenger.
Kasiliauskis recommends avoiding granting permissions to read call logs and contact lists even to trusted applications if it is not necessary.
Applications for communication and social networks have the most features, but they also request a large number of dangerous permissions. Remember, you can always grant permissions later if you need a specific feature. Most users tend to automatically grant all permissions, but it is safer to start with automatic denial and adjust as needed.
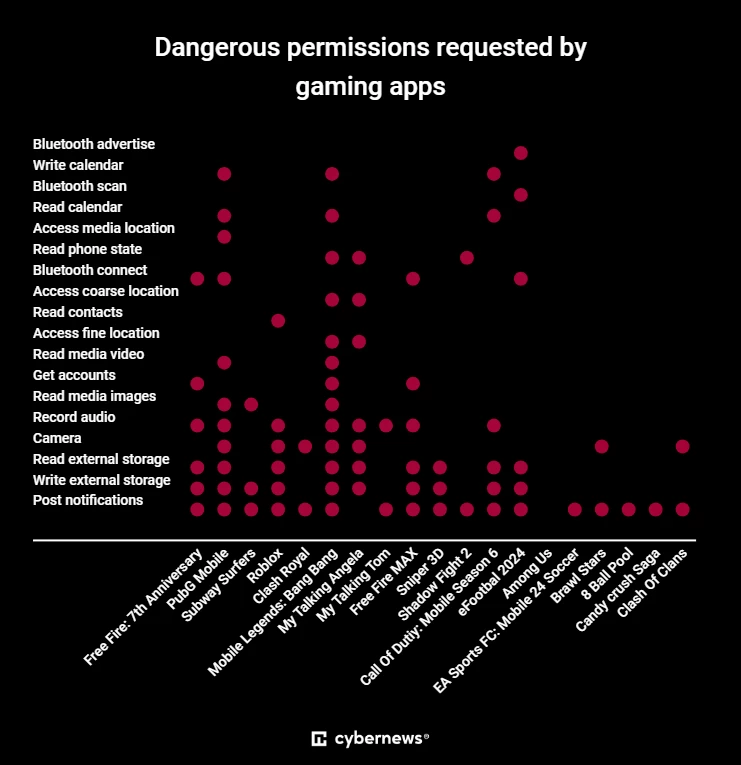
Games request fewer permissions, but are they all necessary?
The analyzed list includes 19 gaming applications, which on average have only four dangerous permissions. However, the discrepancies between them are significant: some require a dozen permissions, and some require none.
Most games (16) want to send notifications. Ten games request permission to write data to external storage, and nine want access to read data.
Eight games request permission to record audio, and seven try to access the camera. Some games even request permission to make calendar entries (3), view phone status (3), and access precise location data.
Among the analyzed games, the most data is requested by: Mobile Legends: Bang Bang (12 permissions), PubG Mobile (11), and My Talking Angela (7).
It is unclear why the game needs access to someone's calendar. Surely the developers have an explanation for this, but it looks strange. It can also be argued that the game has location-based features, uses the camera to create avatars, and records sound for communication. However, it is better to sacrifice some user convenience in the name of privacy and security.
How many permissions do stores require?
Shopping apps request an average of 13.4 dangerous permissions. Lazada and AliExpress require 16-17 permissions, while Wish needs only seven. All apps request access to the camera and precise location, sending notifications, and reading and writing to storage. However, only some of them ask for access to Bluetooth, audio recording, reading phone status, calendars, and contacts.
So how many permissions does the average shopping app need? Extra permissions, such as access to phone status, audio, or contacts, are not necessary for shopping but pose significant privacy risks if misused.
Among other apps, some required the fewest permissions. The Netflix app only requests sending notifications, access to storage, audio recording, and Bluetooth connection. Zedge, an app for wallpapers and ringtones, wants only four dangerous permissions. However, among them is precise location.
Even without dangerous permissions, the app can still be dangerous
Cybernews researchers assure that there is no safe amount of permissions that an app can have. And the app gets a lot more permissions that are considered non-dangerous just by being installed on the device.
Such apps can still start when the phone is turned on, run in the background, have full network access, access confidential information and much more.
Therefore, it is extremely important to regularly delete unnecessary apps, revoke excessive permissions that violate privacy in the device settings, and consider accessing the same services from the browser.
Too many apps with too many dangerous permissions increase the perimeter for potential privacy risks, data disclosure, and even pose financial threats.
Having a large number of apps drains the battery faster and can negatively affect the performance of your device, even if there are no immediate problems.
To keep your phone running, it is better to use only apps from reliable sources, update software, and back up important data.
You can check which dangerous permissions a particular app requires using this tool.
Thank you for your attention!











Write comment