- Network
- A
Identifying DHCP attacks using Wireshark
In network traffic, you can find a lot of interesting things, the main thing is to know what to look for. With the Wireshark analyzer, you can find all sorts of anomalies in traffic, retransmissions, incorrect packets, malicious activity, you can even attach it to the Virustotal API for file analysis for viruses.
In this article, we will talk about how to use Wireshark to detect attacks on DHCP: Starvation and Rogue DHCP. The skill of analyzing such traffic will allow you to more effectively configure rules on intrusion detection systems, and can also help in incident investigations and the work of Red Team teams.
But first, let's look at how DHCP works from the perspective of network traffic. This will come in handy when conducting the analysis.
DHCP through the prism of Wireshark
The process of obtaining an IP address consists of four steps (DORA): Discover, Offer, Request, Ack.
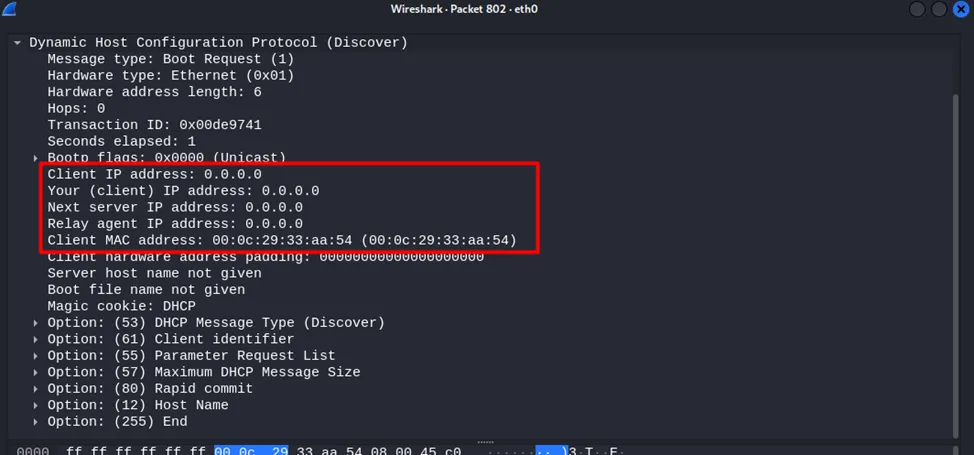
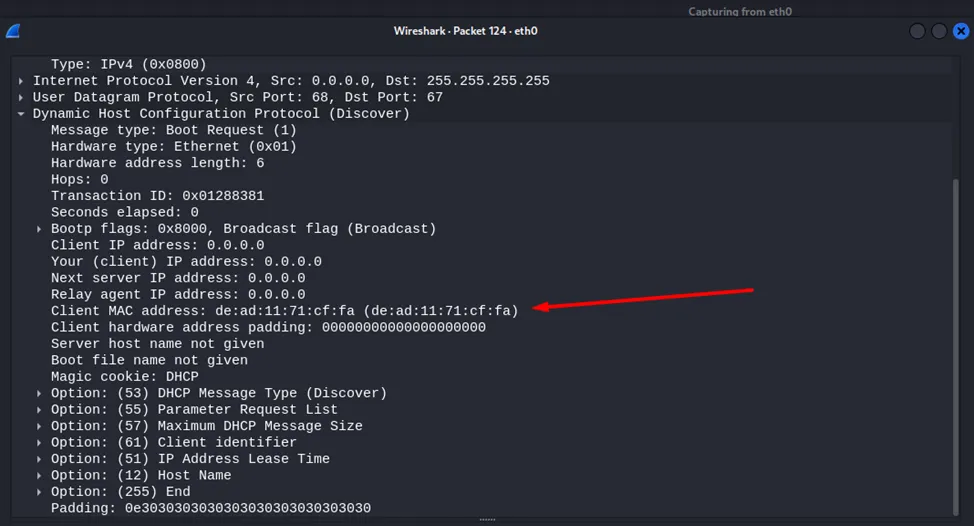
Let's see what each of these steps looks like in a traffic dump. In the first step, the client does not have an IP address, so the source address is 0.0.0.0, and the recipient address is all nodes on the network — 255.255.255.255. At the data link layer, the client has its MAC address, and the sender address is ff:ff:ff:ff:ff:ff.
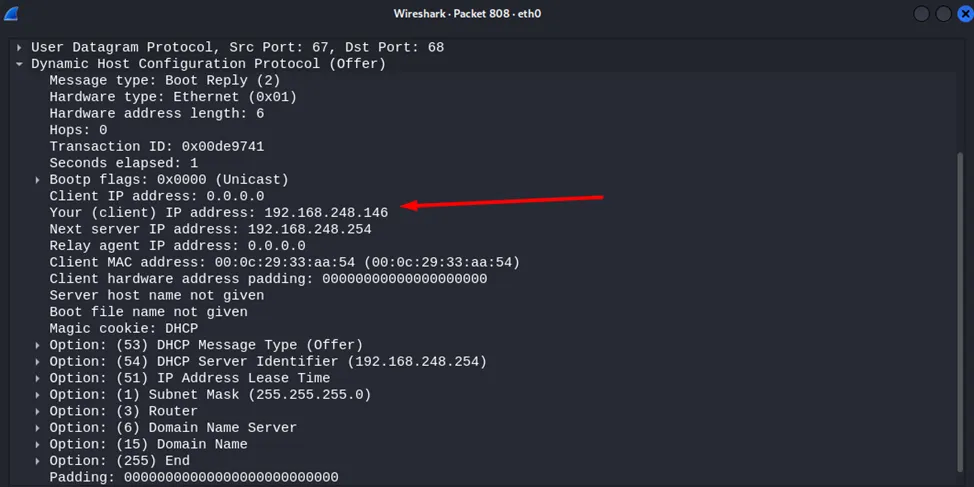
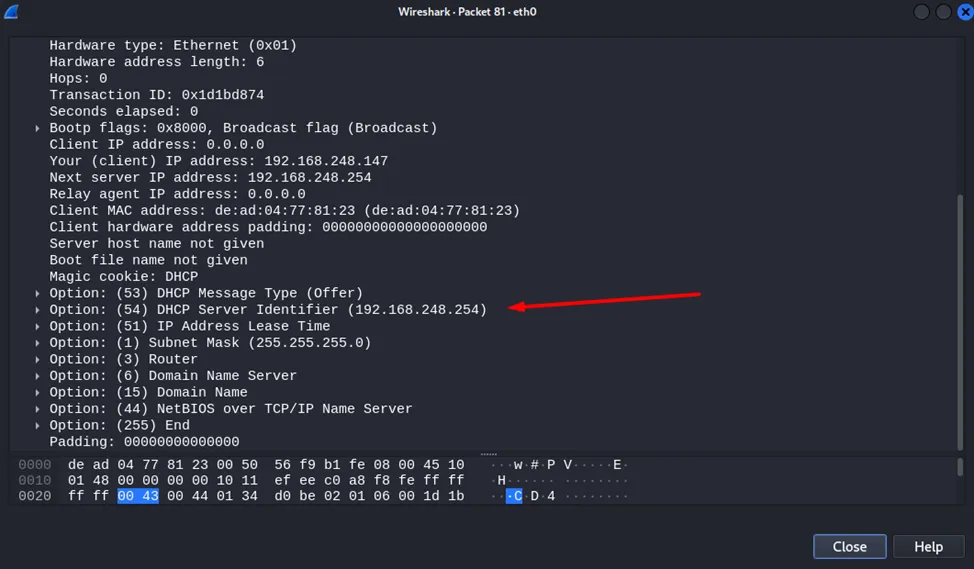
In the second step, DHCP servers respond. Here we already have the IP address offered by the server and options, in particular the subnet mask.
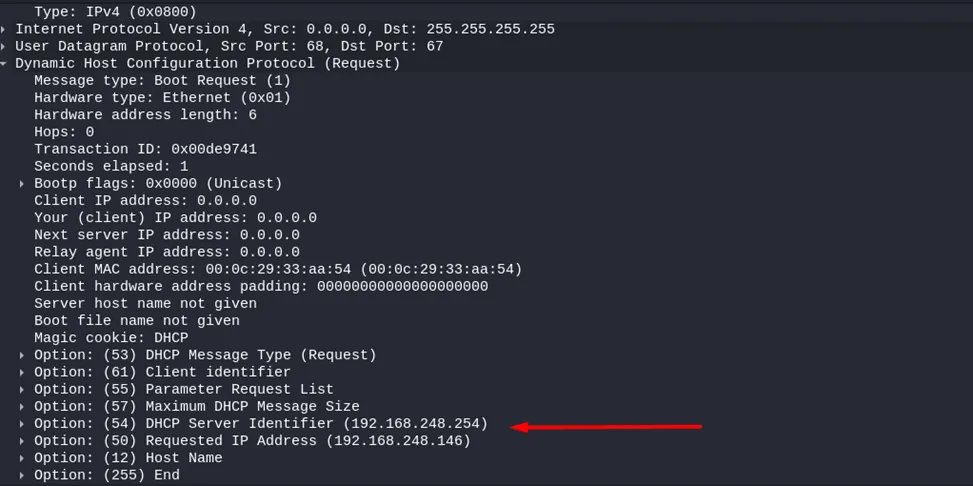
In the third step, the client requests a specific address from a specific DHCP server. We see the corresponding addresses in the Options.
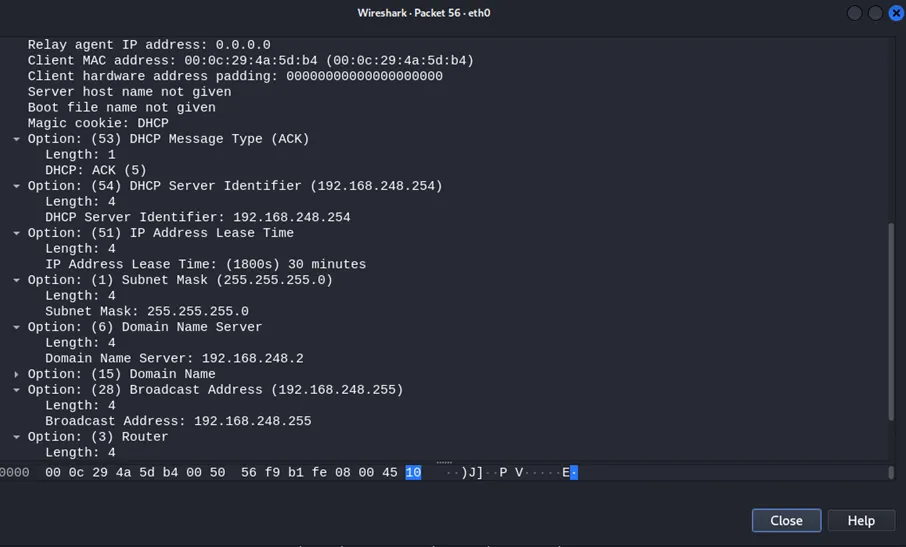
And in the final, fourth step, we, so to speak, "fix the agreements": DHCP confirms the lease of the IP address.
We have figured out what the process of issuing an IP address looks like in Wireshark, and now it's time to see what DHCP attacks look like in the analyzer.
Two in one
The attacker's goal in implementing DHCP attacks is to implement Man in the Middle. That is, the attacker wants to redirect all the victims' traffic through a node that he controls. To do this, he needs to change the network settings on the clients, in particular, specifying his default gateway. The attacker can also pass his DNS server addresses in the network settings, as a result of which the victims will be redirected to phishing resources by entering the domain names of legitimate sites.
DHCP can also be used to implement MitM. To do this, the attacker needs to implement two attacks: DHCP starvation and rogue DHCP. The first is designed to disable the legitimate DHCP server. And the second is simply a DHCP server deployed by the attacker, issuing the IP addresses and network settings needed by the hacker.
Studying DHCP starvation
A distinctive feature of the DHCP starvation attack is a large number of Discover packets sent from different MAC addresses in a very short period of time. It is possible to exhaust several hundred free IP addresses in literally a couple of dozen seconds.
At the same time, the MAC addresses of the clients will be randomly generated, which is also characteristic of DHCP Starvation, since it is unlikely that several hundred nodes will connect in a very short period of time. Thus, to identify this attack, we look at the contents of the Client MAC address field in the DHCP Discover packet. The presence of a large number of packets with different MAC address values over a short period of time is a sure sign of an attack.
Rogue DHCP
The DHCP server deployed by the attacker is essentially the same DHCP, it also distributes addresses and network settings, but different ones. Therefore, from the point of view of network traffic, the process of obtaining an IP address from a rogue DHCP will be exactly the same as from a real one. The same DORA process. And to detect such a server, it is necessary to correctly analyze the contents of the packet.
To do this, you need to know the IP addresses of our legitimate servers that issue IP addresses. Accordingly, the appearance of Offer, Request, and Ack packets containing in the Option 54 DHCP Server Identifier field IP addresses different from our legitimate servers is a sure sign of an attack.
In the Ack packet, we can also find interesting information in the Option 3 Router and Option 6 Domain Name Server fields.
How to better protect yourself
While preparing this article, I came across a forum post from 2006 where a visitor asked how to find a fake DHCP. One of the funniest answers was: turn on continuous ping to the IP of this server and pull out the cables from the switch one by one. On which port the ping disappears, there is the fake DHCP server.
This method will work in a network with two or three switches, but on a larger scale, it is better to use more automated solutions.
Experienced networkers, of course, know about DHCP snooping. This is a layer 2 security technology used on modern switches that discards DHCP traffic identified as unacceptable.
To operate this mechanism, you first need to determine which switch ports can have a DHCP server and which cannot. And for the second (untrusted) type of ports, configure this mechanism.
By default, the switch discards a DHCP packet that came to an untrusted port if one of the messages sent by the DHCP server (DHCPOFFER, DHCPACK, DHCPNAK, or DHCPLEASEQUERY) comes to the untrusted port, or a DHCPRELEASE or DHCPDECLINE message comes containing a MAC address from the DHCP binding database, but the interface information in the table does not match the interface on which the packet was received, or the MAC address specified in the DHCP request and the sender's MAC address do not match in the received DHCP packet.
Also, if a DHCP packet comes with option 82. This option is used to inform the DHCP server from which DHCP relay and through which port the request was received.
Thus, only Discover and Ack address requests can come from unreliable ports, which is exactly what clients need to get an address.
The main problem with using DHCP Snooping is that administrators need to know the topology of their network. After all, if we do not know who lives behind which switch port, we will not be able to effectively configure this technology.
Conclusion
Today we looked at DHCP attacks from the perspective of analyzing traffic dumps in a network analyzer. Based on the data obtained, administrators can configure IDS and other security tools to effectively detect these attacks.





Write comment