- Security
- A
Nose to the wind: how our DNS sniffer helps find Blind vulnerabilities
Hello everyone! In the blog of the Solar 4RAYS Cyber Threat Research Center, we continue to share the results of incident investigations, useful tools for information security specialists, and other practical materials, some of which we also post here.
Today's article from the specialists of our Solar Vulnerability Analysis Department is dedicated to the software they developed for finding and verifying vulnerabilities.
In the vulnerability analysis department, we often have to find and exploit vulnerabilities that, at first glance, are difficult to detect. For example, almost no project goes without Blind-SSRF or Out-Of-Bound XXE, and even Blind-RCE can be found. In this material, we will talk about a tool that will help pentesters significantly simplify the detection of various types of vulnerabilities. But first things first.
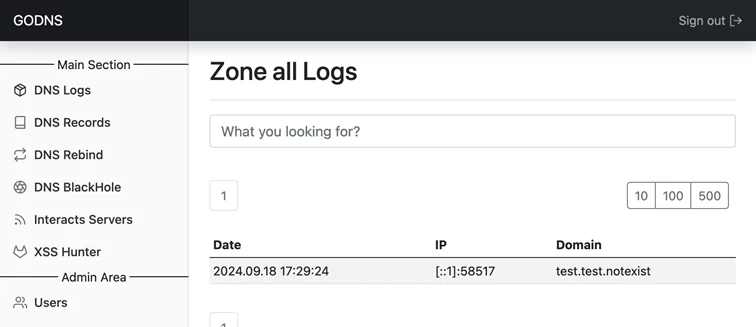
The simplest marker of the presence of a vulnerability can be receiving a DNS request from a remote server. The uniqueness of the domain name in the request guarantees its absence in the cache of public DNS servers, which, in turn, facilitates the processing and logging of this request by a specially configured and tuned DNS server. However, popular DNS servers – such as BIND, PowerDNS, and CoreDNS – do not provide sufficiently convenient mechanisms for working with their DNS server logs, which would save time searching for the necessary information in log files.
In this regard, many security analysts turn to utilities such as dnschef and Burp Collaborator. These are quite popular solutions that cover the basic needs for work, but they also have their drawbacks.
Interaction with dnschef software is carried out only through the operating system console, which makes it inconvenient for a group of specialists to work. This also applies to the software "InteractSH", which is used to search for Blind-SSRF vulnerabilities. And to use Burp Collaborator, a paid version of the software is required. In its case, another important detail plays a role: this software is a cloud solution, and for processing customer data it is not always considered acceptable, as the specialist using it cannot control how the third party processes and stores this data.
Regularly encountering all these problems in practice, we decided to develop our own DNS sniffer with a focus on convenience for team collaboration of security specialists, and today we are ready to share it with the professional community.
The main advantages of our solution are:
the presence of a web interface;
the ability to flexibly configure user access rights;
combined capabilities of several software tools in one centralized solution;
convenient display of results for further processing.
In the process of developing the solution, we identified the following list of main components that turned out to be in demand in everyday work:
DNS sniffer. This is the core module of the system that processes, logs, filters, and displays the results of DNS queries
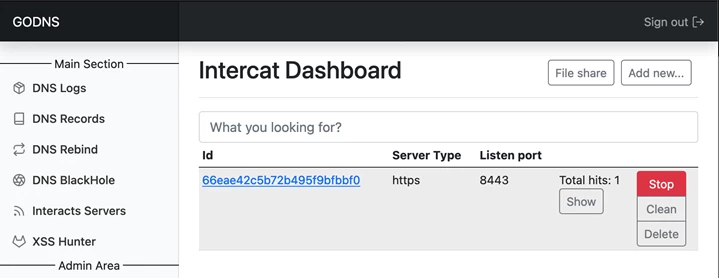
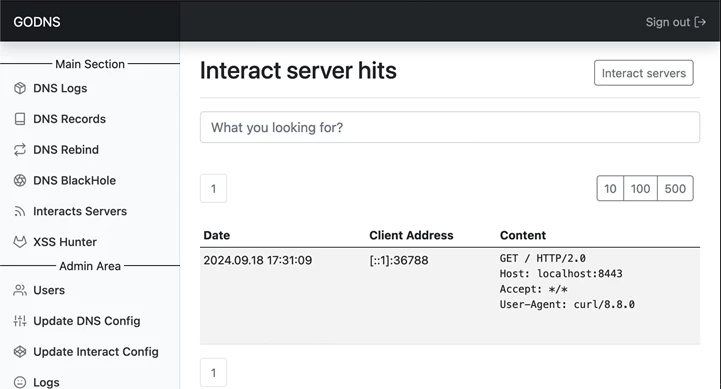
InteractSH. This is the classic and well-known InteractSH, transferred to a convenient web application format, with the ability to start and stop servers, as well as transfer files through it. At the time of publication, the system implements the following main protocols:
o HTTP/S;
o TCP;
o SMTP;
o LDAP;
o FTP.
DNSRebind. A module for rewriting DNS records to bypass server-side filtering mechanisms.
DNS Blackhole. Blacklist module. When working with DNS, specialists encounter bots that try to pick domain names or repeatedly make requests to the same domain name. To disable logging of such requests, the system has the ability to set a filter for displayed information by IP or DNS name from requests.
We have been using the DNS sniffer for five years in various projects, and it has shown ease of use and high efficiency in solving tasks of its class.
The source codes and necessary documentation are already available on Github.
Note that the source code of the project is distributed under the terms of the free MIT license. This means that the solution can be modified and shared with the professional community. It is created solely for good purposes, but we cannot control how you will use this software. We are also always looking for new ideas and are ready to listen to suggestions for improving the DNS sniffer.
We will be grateful for any feedback on our product! Leave us your suggestions and bug-reporting in the issue :)
Authors:
Andrey Basarygin, Head of the Research Group of the Security Analysis Department of Solar Group,
Maksim Teplykh, Expert of the Research Group of the Security Analysis Department of Solar Group,
Evgeny Vasilyev, Expert of the Research Group of the Security Analysis Department of Solar Group.







Write comment