- Network
- A
OSI Network Model: Simple Explanation of Layers
Currently, the main model used in most network interactions is TCP/IP. It is simpler, more compact, and widely used. But here’s the catch: in any serious certification, at every first technical interview, and just for a proper understanding of cybersecurity, you need to know OSI. It’s like the multiplication table: you can live with a calculator, but without it in your head, you’ll always be considered an amateur.
The OSI model consists of seven layers. Seven steps that data takes from one device to another. And if you don't understand them, you don't know where vulnerabilities could occur. I didn’t understand this right away. I failed the first exam. I passed the second one only because I finally stopped trying to memorize terms and started thinking in analogies. And this article is the very analogy I wish I had seen at the very beginning.
1. Physical Layer — Cables, Connectors, and All the Stuff You Can Touch
This is the base. It includes everything that transmits ones and zeros: cables, Wi-Fi, fiber optics, Bluetooth. If you have a cable coming out of the wall and plugged into the router — congratulations, you're looking directly at the physical layer.
Imagine a road. A real one, with asphalt and signs. Mail is supposed to travel on it. And if there is no road — it doesn’t matter who the courier is, what data they have, or how much they charge for delivery. They simply won’t get there.
The physical layer is about the connection itself. It's the level where you can literally touch the internet. Whether you want it or not.
2. Data Link Layer — MAC Address and the Truth About “Apartments in a Building”
Have you ever seen a MAC address in the terminal? Something like 00:1A:2B:3C:4D:5E. This is a hard device identifier. Unique and embedded in the hardware. It can be spoofed, but the real one remains.
Imagine an apartment building. IP is the street. And MAC is the specific apartment. You can write on the door that it's apartment No. 7, but if it’s really No. 25, they’ll still find you there.
This is what the data link layer does: it ensures a direct connection between two devices within a local network. Without it, data cannot even be transmitted from a laptop to a router.
3. Network Layer — IP and Routes, Routes, Routes
Now imagine that you want to send a letter to another city. It's no longer enough to know the apartment — you need to specify the city, street, and zip code. This is what IP does. It says: here I am, and here is where it needs to go.
The network layer is where IP addressing works. This is where routing decisions are made: how to go from one device to another through a bunch of intermediate points. This is also where NAT, routers, and all other entities live that determine how to get from one subnet to another.
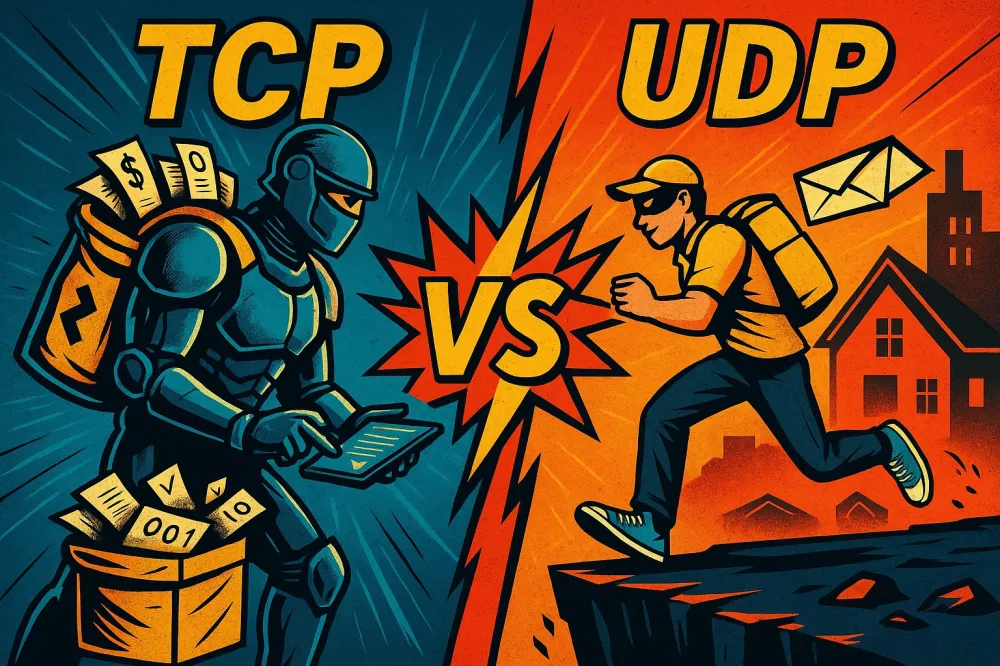
4. Transport Layer — TCP vs UDP, or Who Delivers Mail More Reliably
Now logistics is connected. There are two types of delivery. The first is reliable (TCP). It doesn't just deliver the letter, it checks that you're home, that you've signed for it, and that all the pages are in place. If something is missing, it will return for the missing part. By the way, this is the very 3-way handshake.
The second is fast but carefree (UDP). It throws the letter in the mailbox and leaves. It doesn't care whether you opened it, whether it arrived, or whether it was complete. The main thing is to deliver something quickly. It's great for video streams and online games, where speed is more important than accuracy.
5. Session layer — the call has started, the call has ended
A very simple analogy. You call someone on the phone. While you're talking, the session is active. You hang up the receiver — the session is closed. This is the session layer. It establishes and ends the connection and ensures everything happens within a specific session without confusion.
Without it, you are just shouting into the void, or worse, into several receivers at once.
6. Presentation layer — translator, compression, encryption
You received a letter. But it's written in French, and you speak Russian. Or it's in a zip archive. Or it's encrypted. What to do?
This is where the presentation layer comes in. It is responsible for converting data into a format convenient for the recipient. This could be translation from one language to another, unpacking, format conversion, or decryption. Without it, you will get a stream of bytes that you can't read or interpret.
7. Application layer — browser, Telegram, and everything the user sees
This is the top. This is what you work with every day. Browser, email client, Telegram. Programs that interact with the user work at the application layer. Here are the protocols: HTTP, FTP, DNS, SMTP.
At this layer, you finally see the result of all this ladder. And this is why most people think the internet is just "enter the address and get the page." But now you know how much happens behind this "just."
Final: how to remember all this and not mess up in the interview
Imagine a letter: at the physical level — it's paper, at the data link level — the apartment, at the network level — the city address. Transport — it's the courier. Session — it's the call "I delivered." Presentation — it's the translation of the text. Application — you read the letter.
If you remember this analogy, you won't just pass the exam. You'll understand what's really going on. And if you want to dive into cybersecurity, you'll have the foundation that the entire game is built on.






Write comment