- Security
- A
Ensuring security in software development — CI/CD pipeline issues and threat prevention methods
Security is a critical aspect in software development, the very fact of implementing which eliminates design errors, reduces costs, and focuses the team on using reliable methodologies. I will share our experience of integrating its tools into software creation and the problems that arise along the way.
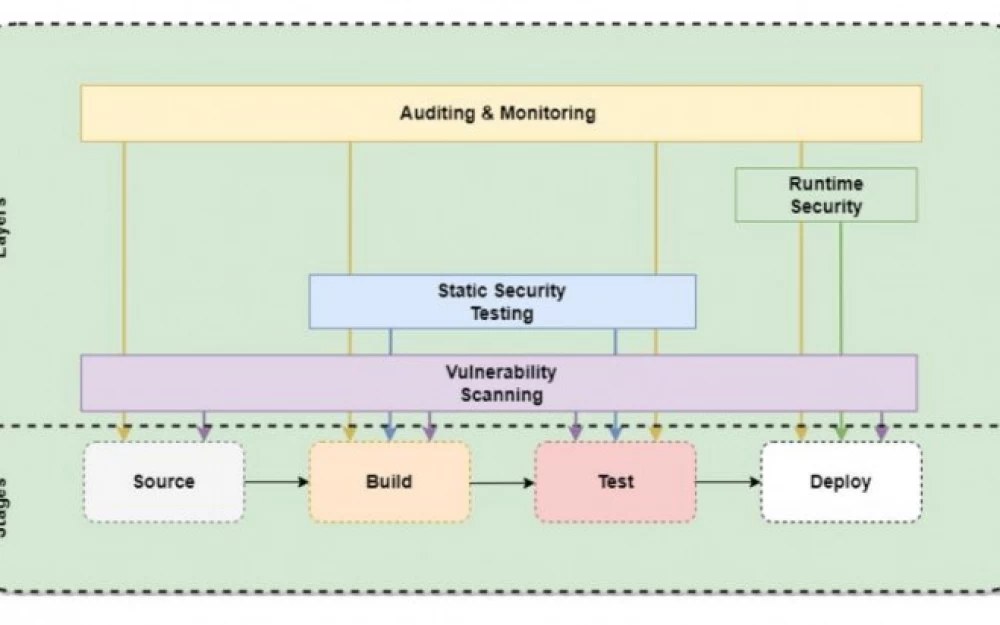
Continuous Integration and Deployment
1. Code Changes
The practice of CI/CD requires frequent code changes, and they create problems in the process of maintaining development security. As changes are made, it is important to thoroughly test and verify them before integrating them into the deployment pipeline.
“Good” changes: a) are compatible with current code and configurations; b) do not introduce any security flaws or new vulnerabilities.
2. Integration Issues
When combining software components into systems, integration issues often arise. These components often have different security requirements, which leads to new vulnerabilities. The task of the team is to ensure reliable integration of components with full compliance with security requirements.
3. Security Flaws
Vulnerabilities in the security system arise at any stage of the CI/CD pipeline. For example, when developers accidentally introduce them into the code or if the infrastructure remains unprotected. Hackers exploit weaknesses to gain access to cause damage or steal confidential information.
Continuous Security Testing
1. Speed and Accuracy
Finding the right balance between speed and accuracy is a major challenge in continuous security testing. Changes need to be checked quickly, but with accuracy and thoroughness in mind.
2. Test Automation
Test automation is another component of the CI/CD pipeline that helps balance the need for speed and accuracy in software development. However, without proper design and thoughtful protection, it also creates security issues.
Automated tests that do not include security checks often miss vulnerabilities in the application. Additionally, a poorly protected automated testing system becomes a target for attackers who can damage the pipeline.
3. Integration with Current Security Tools
Integrating security testing into current CI/CD pipelines and tools is another challenging task:
Security tools may not blend well with existing tools and development processes. This leads to pipeline disruptions and causes compatibility issues that slow down work and reduce productivity.
Security tools require customization to meet the organization's needs. Working in this direction is a labor-intensive and complex process that requires dedicated resources to manage integration and support.
Both factors make the process of integrating security testing into pipelines more difficult.
Continuous Delivery and Deployment
1. Configuration Management
An important component of CI/CD security, as misconfigured systems make the infrastructure vulnerable to attacks. Proper configuration and protection of configurations are key to reducing risks associated with security breaches.
2. Infrastructure as Code (IAC)
IAC is a method of managing IT infrastructure and its provisioning through machine-readable definition files, rather than through manual configuration of individual systems. It offers to automate the entire lifecycle of the infrastructure: from provisioning and configuration to deployment. At the same time, the methodology reduces the risk of human errors and prevents configuration inconsistencies.
3. Deployment Pipeline Security
Another important component of CI/CD security. It includes ensuring the correct configuration of deployment settings using special security measures: SSL/TLS encryption and secure communication ports.
To prevent unauthorized access, it is necessary to implement control — with user authentication and authorization, network segmentation, and firewalls. It is also important to ensure comprehensive monitoring and logging, which will allow detecting security breaches and responding to them quickly.
It is necessary to use Security Information and Event Management (SIEM) tools for monitoring during deployment and alerting security experts about threats.
Other CI/CD Security Threats
In addition, CI/CD security threats include:
Unauthorized access to code.
Unsafe code.
Improper secret management.
Lack of Shifting Left practice.
When implementing security measures in CI/CD, consider:
Scan coverage.
Cost of ownership and licensing terms.
Required maintenance and setup efforts.
Scalability.
Integration with the current development and security stack.
Each threat requires its own approach and comprehensive elaboration.
Summarize
The team wishing to realize the benefits of integrating security into the software lifecycle should:
Avoid careless coding of secrets in configuration files and CI/CD build tools.
Create a set of authentication mechanisms for version control.
Ensure access control for CI/CD build tools.
Set up a comprehensive rollback option.
Ensure configuration parity across pipeline environments.
Implement a continuous scanning and vulnerability monitoring process.
Take care of regular cleanup of unnecessary resources and utilities.
By addressing these issues, the organization reduces the risks associated with code deployment in an automated and rapidly changing CI/CD environment.






Write comment