- Security
- A
Bypassing Github access restriction to the Trivy vulnerability database. Quick fix to help you
Recently, developers using the Trivy image scanner encountered the TOOMANYREQUESTS error. It occurred due to the maximum number of tool users and the download rate limit from the Container Registry ghcr.io.
Recently, developers using the Trivy image scanner encountered the TOOMANYREQUESTS error. It occurred due to reaching the maximum number of tool users and the download rate limit from the Container Registry (CR) ghcr.io.
My name is Alisa Kirichenko, and I am developing the container platform "Shturval". We use Trivy extensively, but we do not want to depend on the availability of third-party services. Otherwise, customers will not understand. Therefore, we have our own databases, and they are updated every night.
If you are too lazy to read further, here you go:
Trivy DB:
public.shturval.tech/trivy-dbTrivy Java DB:
public.shturval.tech/trivy-java-dbDetails are below.
Now a few introductions
The Trivy scanner does not contain the vulnerability database (VDB) inside the executable file; it is downloaded from the CR when scanning is started. If the CR is not specified, ghcr.io is used, which has limitations affecting users.
As a workaround, it is suggested to:
use third-party CRs, which may not be suitable for companies overly concerned about the security of their IT products;
create "mirrors" of repositories, which in turn poses a risk of violating the rules of the service provided by GitHub, and also requires constant monitoring of their proper functioning.
What we do
When developing the container image scanning functionality in our platform, we wanted the VDB to be up-to-date, provide the ability to form from multiple sources, and be provided both from our public registry and from local "mirrors" of our customers.
The vulnerability database is a set of records that contains:
vulnerability identifier (CVE ID);
vulnerability description;
components affected by the vulnerability;
severity level;
discovery date;
patch release date;
exploits and attack methods;
remediation recommendations;
links and resources.
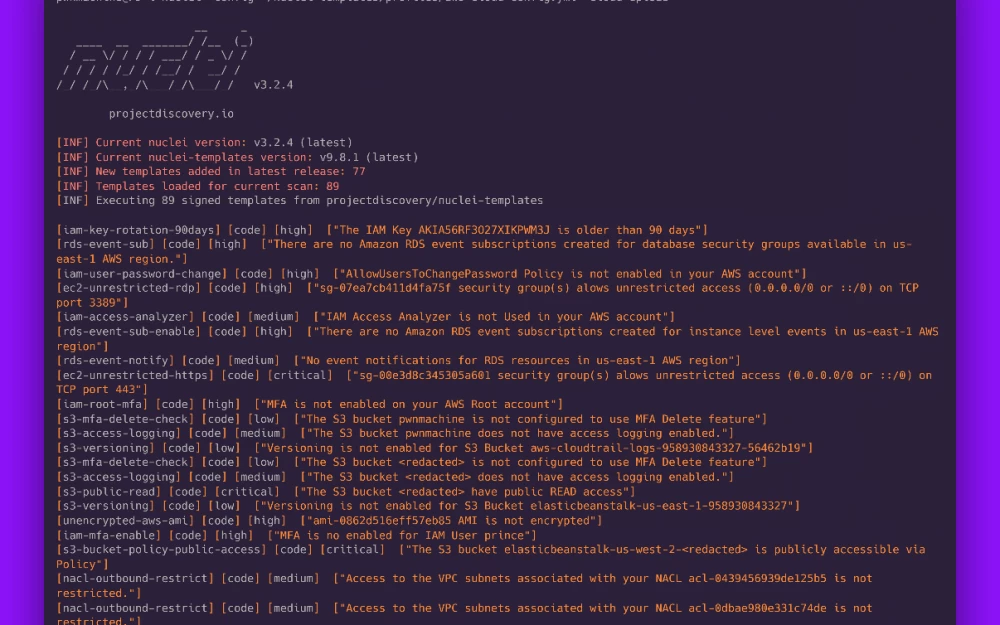
The database is primarily assembled from the FSTEC BDU (yes, most of our CVEs have descriptions in Russian) and NIST, and then enriched with information from vendor feeds. All this happens automatically in our CI, after which it is published on public.shturval.tech. Support for images based on domestic operating systems is also available, but that's a topic for a separate post.
How to solve the problem?
Here's how to get the database in Trivy locally or in the pipeline:
trivy image --download-db-only --db-repository
public.shturval.tech/trivy-dbTo use it in Trivy Operator, you need to add parameters to the Helm chart:
trivy:
dbRegistry: public.shturval.tech
dbRepository: trivy-db
javaDbRegistry: "public.shturval.tech"
javaDbRepository: "trivy-java-db"




Write comment