- Security
- A
Exploring the "malicious" RJ45 flash drive
Reverse engineering hardware can be very challenging — but sometimes all it takes is a cozy chair and Google Translate.
When browsing headlines related to information security, one should assume that reports of widespread sabotage disrupting supply chains are usually false. No, I’m not claiming that such an attack cannot happen; it’s just that such tricks are complex, time-consuming, and risky. You only resort to this if there are no other options left. Generally, it’s much easier to steal credentials or trick someone into downloading a malicious file.
Recently, a young entrepreneur stirred up social media by claiming that a device he purchased in China for Ethernet-to-USB connectivity was immediately loaded with malware that “slipped past virtual machines,” “captured keystrokes,” and “used characteristic Russian-language elements.”
These revelations gathered millions of views, but the details of the issue appeared quite murky. The post's author demonstrated an ambiguous antivirus scan report made in Crowdstrike Falcon, but the example seemed thoroughly fake: the binary was a self-extracting EXE file created using 7-Zip. This is a well-known free archiver developed by Igor Pavlov. The “characteristic Russian-language elements” referred to the author's nationality, while all other details mainly looked typical for self-extracting archives that install drivers. Finally, it seemed that the contents of the archive corresponded to a signed public driver 2.0.7.0 for the RJ45-to-USB chip manufactured by the Shenzhen company CoreChips. In the accompanying .inf file, it is also referred to as Corechip Semiconductor.
Signs of malware |
Counter-detection/stealth |
Creates a process in suspended mode (likely for process injection) |
Runtime awareness |
Reads a registry key specific to the virtual machine |
Reads the registry for VMWare-specific artifacts |
The input sample contains a known trick to bypass VM |
Installation/persistence |
Resets the system driver |
Writes data to a remote process |
Yes, it is assumed that this is roughly how such a virus should operate.
In the driver documentation, there is a reference to a chip called SR9900; there is virtually no information available about this chip or its manufacturer. However, I did some digging and believe that it is an exact clone of Realtek RTL8152B. The English-language product brief implies that “SR” stands for “Supereal.” This name appears in the context of counterfeit FTDI FT232RL chips, which have recently been a real curse for the entire industry.
The pedigree of this chip is important not only due to the potential deception through IP imitation but also because the original architecture of Realtek is quite old; the specification dates back to 2013. The device supports 100BASE-TX and USB 2.0, which echoes the era of Windows 7. It was a time of inconvenience—CD drives were already going out of fashion, but it was unrealistic to expect any computer to be constantly online. Therefore, on some devices marketed as external drives, it made sense to keep their own drivers. From a security standpoint, this was no better or worse than any other improvised method of file delivery.
In other words, considering the historical context, storing the driver on the device or the driver itself was not perceived as something particularly strange.
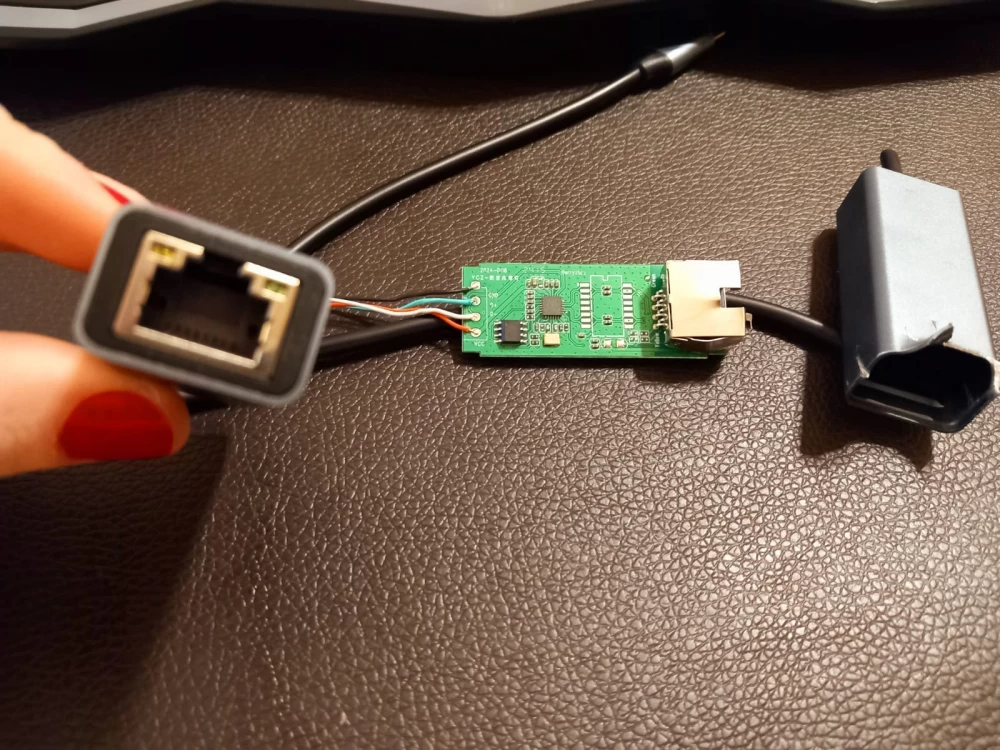
However, the author of the topic implied that this was not the end of the story. The topic included photos of the device in disassembled form, pointing to a sparsely populated prototype board with a serial integrated circuit of type 25x40, connected next to the aforementioned SR9900:
Why did this device require 512 kB of flash memory? Was it allocated for firmware, or was it where malicious actors stored stolen packets?... There's no harm in asking! Malicious hardware does exist. It is used by both intelligence agencies and private pentesters. Hmm, even I built a malicious plasma lamp for work over ten years ago. However, we are not here to discuss whether it is possible to create a malicious RJ45-to-USB adapter. We were interested in whether the author of the post was right that in this particular case "Chinese ears are sticking out again."
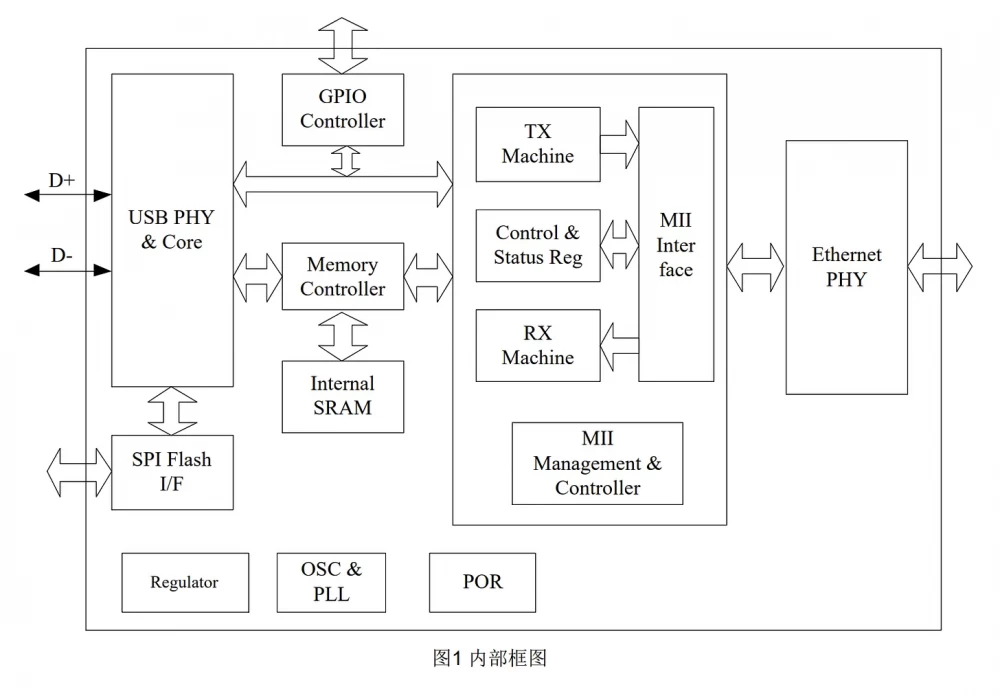
Unfortunately, both the SR9900 and RTL8152B are equally vaguely described regarding the purpose of the accompanying integrated circuit with flash memory. I dug up the following architectural overview, but it doesn't provide any special information either:
I had already set out to the dark side (amazon.com) and simply acquire such a flash drive with one goal in mind — to dump the contents of the memory chip. Working with the Serial Peripheral Interface (SPI) bus is not difficult. Essentially, you provide a clock signal at a frequency that is convenient for you. You can even press the button with your finger. On the leading edge of each clock, the peripheral reads one bit from the "serial in" line, and at the same time, the host sends one bit back through "serial out." No handshakes, no headers, no parity bits, no flow control.
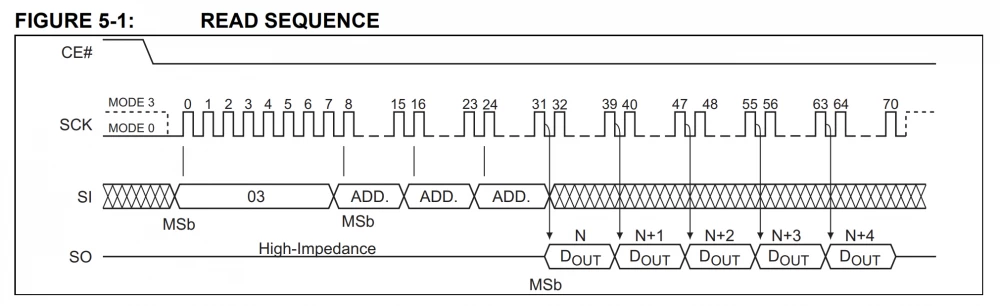
The "application" protocol of the flash chip is as simple and common as it is for almost any serial memory integrated circuit. To make it work, the host sends a 1-byte READ instruction (0x03), followed by three address bytes. The chip starts sending data immediately after receiving the four-byte sequence, and the stream of bits continues as long as the clock signal is coming from the host:
But then, when the item was in my cart, an epiphany struck me. I went to the CoreChips website and, using Google Translate, tried to find the original Chinese text that would translate to English as “SR9900 series chip Windows system mass production tool” (Windows system mass production tool with SR9900 series chip). I searched for a suitable string and came across several old Chinese-language forum threads. One of them led me to download a password-protected and paywalled file. This archive was called “SR9900(A)设计资料1018.rar.” After shelling out another $2.99, I became the proud owner of an archive that contained a very vintage-looking SR9900 production tool:
Along with it, a 168-kilobyte image of the 9660 file system was provided (!), which included a self-extracting driver for Windows. The programming tool copies the .iso file to the SPI flash memory. Aha: the chip essentially acts as a "software-defined" CD-ROM, serving as an improvised substitute for the physical media you would have had to use with such hardware in the past. You can download the disk image here; the password for the file is “rj45”.
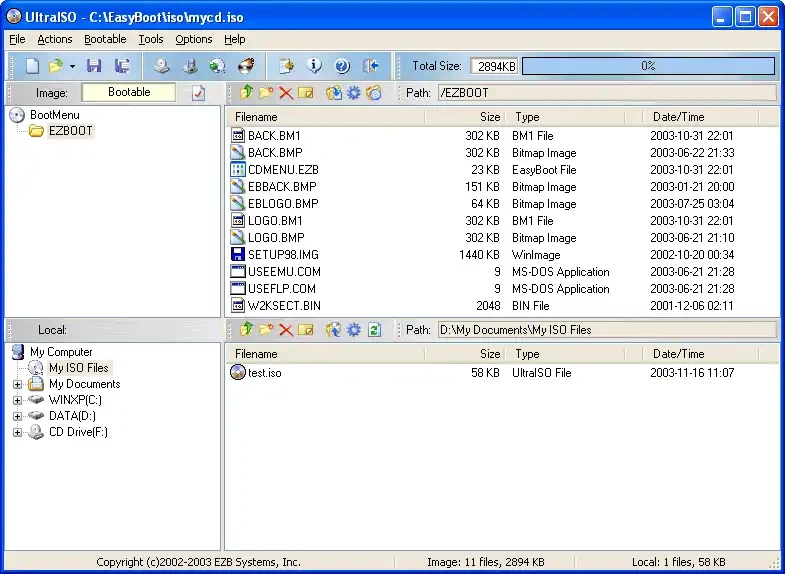
As a lyrical digression: the CD-ROM image was created using “ULTRAISO V9.3 CD & DVD CREATOR, (C) EZB SYSTEMS” — yet another blatantly vintage tool that has come down to us from the days of Windows XP:
If you want to try it, keep in mind that this tool requires an Intel Pentium processor with a frequency of 166 MHz or higher.
To confirm that I was not mistaken with the find, there was also a document in the archive titled “SR9900(A)设计前必看.docx”. It contained a passage with the following content:
“When using the SR9900 as a network USB card (consumer-grade peripheral quality), SPI can serve as a virtual optical disk when installing the system driver for Windows (SPI non-volatile memory with a pre-recorded SR9900 driver for Windows operation)”
It was also emphasized that using the chip with flash memory is not mandatory.
Here’s what we’ve come to: a predictable and somewhat dull conclusion that strange does not necessarily mean bad. We did this work without a hardware lab; all it took was a bit of patience and some inventive Googling.
Honestly, there is still one uncovered card: in the very integral scheme of the SR9900, there are two small microcontroller cores — USB and Ethernet — and each of them runs its own internal code. If we feel that the chip manufacturer is being secretive about something, then why not take a look inside them. Realtek provides a freely available Linux driver for RTL8152, capable of patching the firmware memory a bit. Personally, I don't think there is any encryption or digital signing involved.
Should we be worried that someone will send us a malicious flash drive from distant lands? If you are a scientist involved in the Iranian nuclear program, then perhaps you should! If you are on the board of directors of a critically important civil company, then a bit of caution wouldn't hurt either. Perhaps someone is engaged in industrial espionage and is keeping an Excel spreadsheet of all your suppliers — just in case.
But if I am just administering a home network, then I think nothing terrible will happen.








Write comment