According to the tag fun, the following results have been found:
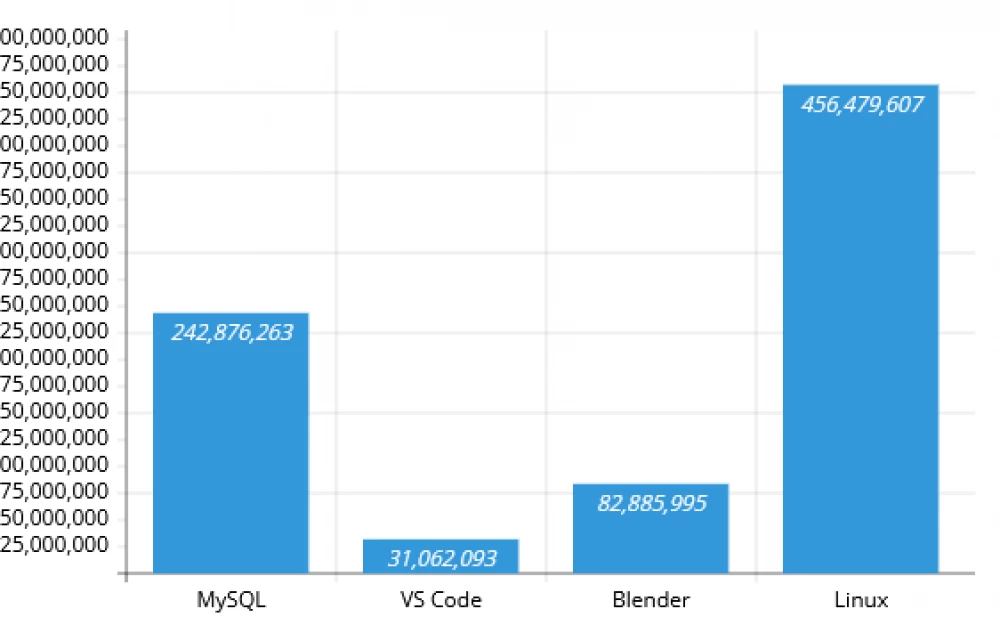
This article about the new extension of the transformer architecture – Titan from Google – that allows expanding the limits of LLM to 2 million tokens, prompted me to inquire how many tokens suitable for LLM are contained in the sources of colossal software.
Hello everyone! Sergey Sobolev is here, a specialist in distributed systems security at Positive Technologies, our team is engaged in auditing smart contracts. Today I will tell you about the results of our team's research and conclusions regarding the security audit of smart contracts in the FunC and Tact languages of the TON platform.
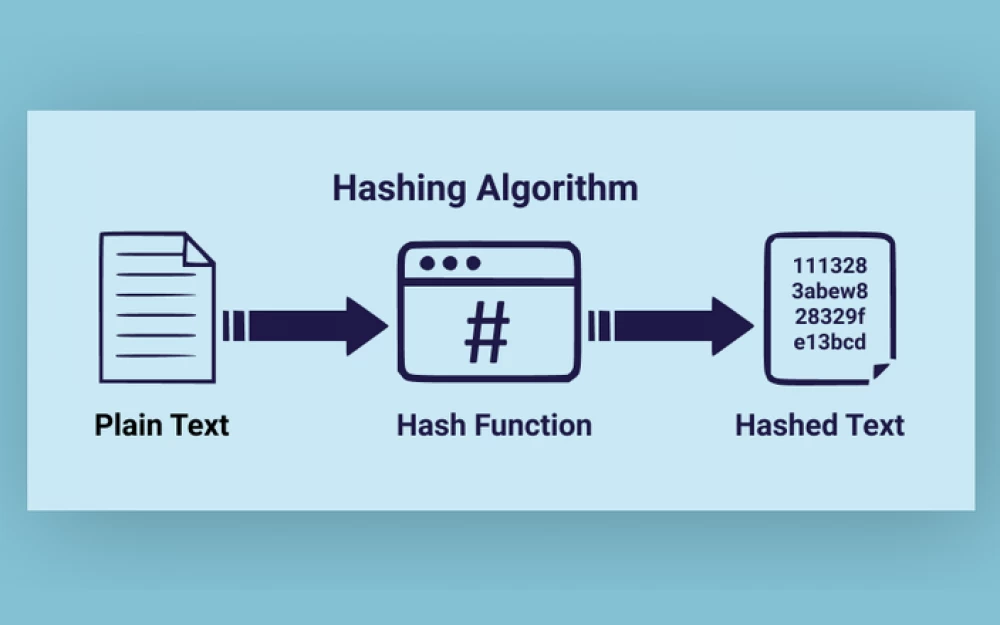
Hash functions are incredibly beautiful mathematical objects. They can map arbitrary data to a small range of fixed-size output data in such a way that the mapping is deterministic, yet appears random. This "deterministic randomness" is incredibly useful for a wide range of applications, such as hash tables, checksums, Monte Carlo algorithms, distributed algorithms without communication, and so on.
Modern gadgets are unimaginable without AI functions. But they come at a cost that the end consumer has to "pay", including faster battery drain and device overheating. As a result, electronics manufacturers face a dilemma: features are needed, many of them, but without significant damage to the battery.
Disclaimer: the words used like "port", "hack" and "reverse" do not mean that the article is intended exclusively for geeks! I try to write so that it is understandable and interesting to absolutely everyone!
tekkix, hello! I am Alexander Leonov, leading expert of the PT Expert Security Center laboratory. Every month, my team of analysts at Positive Technologies researches information about vulnerabilities from vendor security databases and bulletins, social networks, blogs, telegram channels, exploit databases, and public code repositories, identifying trending vulnerabilities in all this diversity. These are the vulnerabilities that are either already being exploited or may be exploited in the near future.