- Security
- A
Dorks in a new way – looking for what is open
When conducting any pentest of a corporate network, one of the actions of white hackers is to search for information that is practically in the public domain: on file shares, in repositories, in shared folders on user machines. In short, everything that lies in the corporate network and is available to every domain user. If some of the resources are not available to a regular user, after obtaining privileged rights, we can retry to access these folders or files.
Anyway, in file dumps and repositories, you can find a lot of interesting and useful things from the point of view of penetration testing. For example, accounts may remain in the source code. Yes, our valiant developers commented out the corresponding lines in the code and this loophole did not get into the artifact, but the comment still remained in the source code. Various scripts, playbooks, instructions are also of interest, as they may also contain credentials. Backup copies may contain private key files and other useful confidential information.
It would seem that everything is simple, it is necessary to check the available file resources for... Here a separate question arises, what exactly to look for? What should the desired login/password pair look like? Here, good old dorks come to our aid.
Recall that Google Dorking is a technique of specific search queries that facilitate the process of finding information in open sources. In fact, dorks can be used not only in the Google search engine, but they became known precisely thanks to this search engine.
Here are examples of some of these search queries:
inurl:/view.shtml
intitle:”Live View / – AXIS” | inurl:view/view.shtml^
inurl:ViewerFrame?Mode=
inurl:ViewerFrame?Mode=Refresh
inurl:axis-cgi/jpgAbout ten years ago, with the help of such queries, it was possible to find webcams broadcasting video on the Internet. And now these dorks only return articles about how you can "spy on someone else's life".
Visiting the repository
However, the idea of dorks is quite viable. Only we will search through repositories. If we are talking about searching in the source code available in public repositories, then here we can use special services, for example, https://sourcegraph.com/. In the free version, we can use ready-made expressions, and if you really want to complicate the queries, for example, using regular expressions, then a paid subscription will be required.
In the example below, the query was set to the string db_password and among the many repositories found on Github, a source with hard-coded credentials was discovered.
In general, there are quite a lot of dorks, that is, search queries that can be searched for.
Here are just a few of the most common examples:
"api_key"
"api_secret"
"auth"
"auth_token"
"authorizationToken"
"db_password"
"db_username"
"dbpasswd"
"dbpassword"
"ssh"
"ssh2_auth_password"However, a pentester should still have an idea of what the credentials they are interested in look like. For example, knowing the language used in the backend code and the DBMS, one can see what the connection string looks like and search for it first, and then see what code is nearby.
Also, with this search service, you can see what code changes have been made since a certain point in time. For example, you can find out in which repositories commits were made in the last hour.
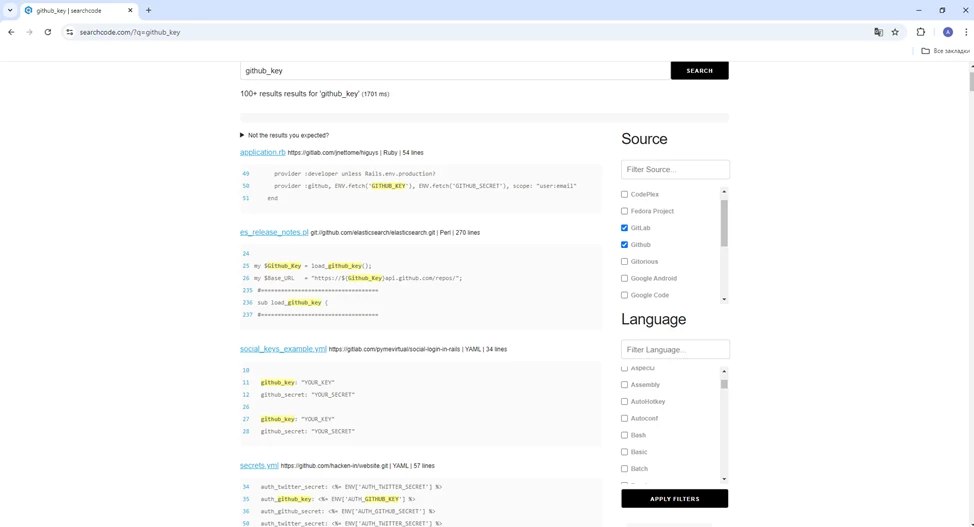
Another search engine that works on a similar principle is SearchCode (https://searchcode.com/).
It also searches for the specified value in various repositories, and if necessary, you can configure filtering to search only in certain repositories or certain programming languages.
For best results, you can use both search services in case one of them doesn't find something.
What has already leaked
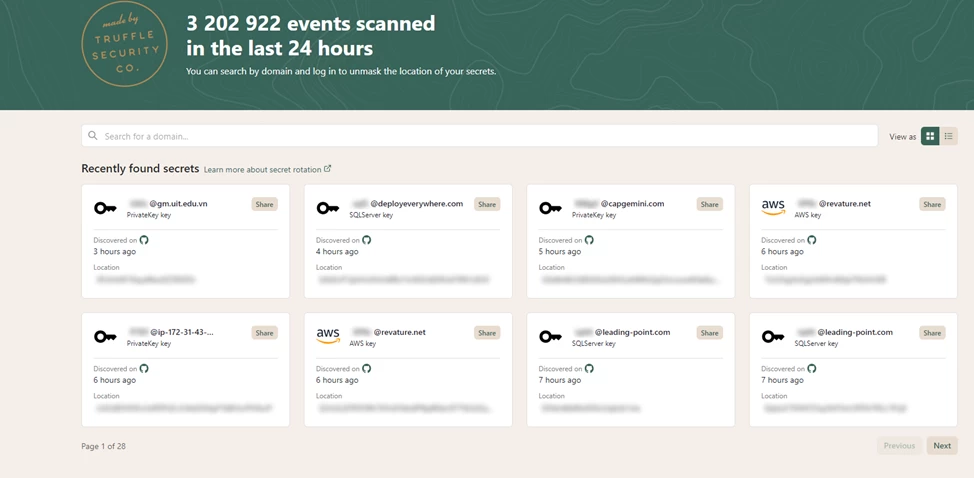
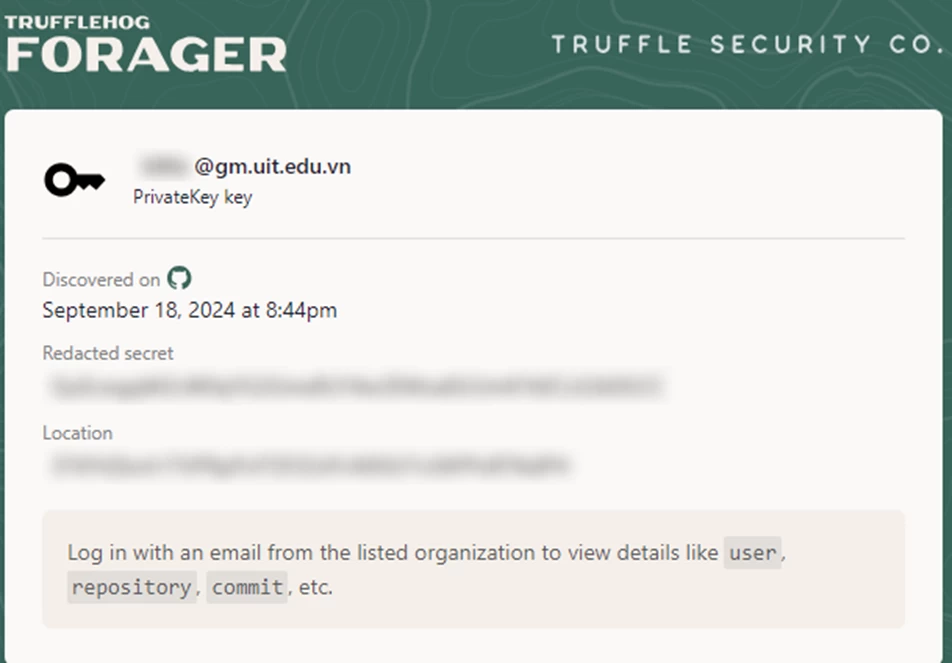
Here we will talk not so much about dorks and search queries, but about services that find confidential data leaked to the network. The next service, according to the authors, should help security specialists to timely detect leaks of confidential data. The Forager project (https://forager.trufflesecurity.com/) is designed to search for leaked confidential data on the network, such as passwords, private keys, etc. Anyone can specify the domain of interest of the organization and the search engine will show if it has any information. But, of course, any user will not be able to see what exactly was found.
Only the one whose account on this service is linked to the domain of the compromised organization can view the details of the leak.
Actually, Forager is not the only service developed by Truffle. They also have TruffleHog, which allows you to find various secrets leaked to the network. To test it, you just need to run the container, specifying the test repository as parameters.
docker run --rm -it -v "$PWD:/pwd" trufflesecurity/trufflehog:latest github --repo https://github.com/trufflesecurity/test_keys
Another similar tool is Gitleaks. This is a SAST tool for detecting and preventing hard-coded secrets in the code, such as passwords, api keys, and tokens in git repositories.
You can also run this tool using Docker by specifying the folder with the scanned source code:
docker run -v ${path_to_host_folder_to_scan}:/path zricethezav/gitleaks:latest [COMMAND] [OPTIONS] [SOURCE_PATH]
Conclusion
In this article, we talked a little about how to detect confidential data stored in repositories using various services that allow you to automate this search. It is worth noting that the described tools can help not only pentesters but also specialists who ensure information security.
You can learn more about tools and best practices for ensuring information security in online courses from industry experts.
- Release of Fedora Linux 41: new features after six months of development
- Evolution of NGFW in Russia on the example of UserGate. Interview with UserGate NGFW Development Manager Kirill Pryamov
- A hole in Cloudflare’s shield: how the attack on Jabber.ru exposed a problem no one has talked about since 2023








Write comment