- Security
- A
AWS Cloud Configuration Security Overview using Nuclei Templates
In the new version v9.8.5, Nuclei Templates have added templates for checking AWS Cloud configuration. In this post, we will discuss automating the verification of incorrect configurations in the cloud, creating custom AWS checks, and sharing results on the PDCP Cloud platform for further analysis.
Review of AWS Cloud configuration security, also known as AWS Cloud Config Review or AWS Cloud Audit in pentester circles, is an important procedure for assessing the security level of Amazon Web Services (AWS). This implies a thorough examination of AWS configurations to check their optimality in protecting data and services. Such a comprehensive analysis covers various aspects of AWS infrastructure, including storage, databases, and applications, to ensure compliance with established security protocols. By identifying potential vulnerabilities and areas for improvement, this review helps strengthen protection, reducing the risk of unauthorized access and data leaks.
Key actions related to the AWS Cloud security configuration review
Access and Identity Management (IAM) Check: Assessment of who has access to which resources in AWS. This ensures that only the necessary individuals have access to confidential information or critical systems.
Service Configuration Check: Analysis of AWS service settings, such as checking the privacy of S3 storage and the inaccessibility of databases over the internet if not required.
Monitoring and Logging: Ensuring that systems track activity in the AWS environment. In the event of a security issue, logs will allow the sequence of events to be reconstructed.
Network Configuration Audit: Analysis of network settings within AWS, such as security groups and access control lists, to ensure they are protected from unauthorized access.
Compliance Check: Verification that AWS configurations comply with specific rules, data protection laws, or industry standards.
Vulnerability Assessment: Scanning the AWS environment for weak points through which attackers can gain access. This helps to eliminate vulnerabilities before they are exploited.
Best Practices Assessment: Analysis of configurations for compliance with recommended security practices for optimal protection of AWS resources.
Troubleshooting and Reporting: The review provides practical recommendations for addressing identified vulnerabilities or compliance violations. Detailed reports are generated that highlight security gaps, non-compliance, and provide recommendations for addressing them. This helps make informed decisions to improve security levels.
We believe that the process of reviewing AWS cloud configuration is overly complicated and in practice causes many problems. Therefore, we decided to simplify it by creating a security check for AWS Cloud using a simple YAML format applied in Nuclei. These templates are designed to perform all the main checks (configuration, logging, compliance, and best practices). Using these templates, we can easily create a detailed report on our cloud platform with measures to address vulnerabilities. This simplified approach makes the review process more convenient for companies as well as for penetration testers.
What are Code Protocol templates?
Nuclei allows users to execute external code in the host operating system, providing security researchers, pentesters, and developers with the ability to extend their capabilities beyond standard protocol-based testing. This feature allows interaction with the underlying operating system, facilitating the execution of custom scripts or commands to solve a wide range of tasks, including system configuration, file handling, and network interaction. Such control and adaptability allow users to customize security testing workflows to meet specific needs.
Since code templates can execute commands on hosts, users first need to sign the template with their keys, and such templates are not included in standard scanning methods. To use these templates, you need to sign them with the -sign flag. After signing, you can run the templates using the -code flag.
In the following example, we show how we can easily execute an aws-cli command directly in the template. However, unlike other templates that run on target hosts, this one will execute the command on our own host.
id: aws-config-review
info:
name: AWS Cloud Config Review Example
author: princechaddha
severity: info
description: |
Checks if AWS CLI is set up on the environment.
reference:
- https://aws.amazon.com/cli/
tags: cloud,devops,aws,amazone,aws-cloud-config
self-contained: true
code:
- engine:
- sh
- bash
source: |
aws sts get-caller-identity --output json
matchers:
- type: word
words:
- '"UserId"'
extractors:
- type: json
name: account
internal: true
json:
- '.Account'Example #1:
In this example, we will create a template that detects publicly accessible S3 buckets, which is a common cause of data leaks.
We set the parameter self-contained: true, because, unlike regular Nuclei templates that require a target host, code templates work independently of any host.
The code block starts with specifying the engine we want to use to execute the command, and then the command itself goes in the source section.
After the info block, we added a flow block that controls the sequence of template execution. Initially, the
code(1)block is executed, which includes an extractor that extracts the names of all available S3 buckets and saves them in the buckets array. Then the for loop iterates over all the buckets and executes the second code block, substituting the bucket variable into the second command.The second code block executes the AWS CLI command aws s3api get-bucket-acl --bucket $bucket —query 'Grants[?(Grantee.URI==http://acs.amazonaws.com/groups/global/AllUsers)]', replacing the bucket name with the $bucket variable obtained in the first command.
The matcher checks if the bucket has read (READ) permission.
Finally, the last extractor outputs a list of buckets with public access.
id: s3-public-read
info:
name: S3 Bucket with Public READ Access
author: princechaddha
severity: critical
description: |
Verifies that Amazon S3 buckets do not permit public 'READ' (LIST) access to anonymous users, protecting against unauthorized data exposure
reference:
- https://docs.aws.amazon.com/cli/latest/reference/s3api/get-bucket-acl.html
tags: cloud,devops,aws,amazon,s3,aws-cloud-config
flow: |
code(1)
for(let bucketName of iterate(template.buckets)){
set("bucket", bucketName)
code(2)
}
self-contained: true
code:
- engine:
- sh
- bash
source: |
aws s3api list-buckets --query 'Buckets[*].Name'
extractors:
- type: json # type of the extractor
internal: true
name: buckets
json:
- '.[]
- engine:
- sh
- bash
source: |
aws s3api get-bucket-acl --bucket $bucket --query 'Grants[?(Grantee.URI==`http://acs.amazonaws.com/groups/global/AllUsers`)]'
matchers:
- type: word
words:
- '"Permission": "READ"'
extractors:
- type: dsl
dsl:
- '"The S3 bucket " + bucket +" have public READ access"'Example #2:
Similarly, in the following template, we check for publicly accessible RDS snapshots.
id: rds-public-snapshot
info:
name: RDS Public Snapshot Exposure
author: princechaddha
severity: high
description: |
Checks if AWS RDS database snapshots are publicly accessible, risking exposure of sensitive data.
impact: |
Public snapshots can expose sensitive data to unauthorized users, leading to potential data breaches.
remediation: |
Modify the snapshot's visibility settings to ensure it is not public, only shared with specific AWS accounts.
reference:
- https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/USER_ShareSnapshot.html
tags: cloud,devops,aws,amazon,rds,aws-cloud-config
variables:
region: "ap-northeast-1"
flow: |
code(1)
for(let RDPsnaps of iterate(template.snapshots)){
set("snapshot", RDPsnaps)
code(2)
}
self-contained: true
code:
- engine:
- sh
- bash
source: |
aws rds describe-db-snapshots --region $region --snapshot-type manual --output json --query 'DBSnapshots[*].DBSnapshotIdentifier'
extractors:
- type: json
name: snapshots
internal: true
json:
- '.[]
- engine:
- sh
- bash
source: |
aws rds describe-db-snapshot-attributes --region $region --db-snapshot-identifier $snapshot --query 'DBSnapshotAttributesResult.DBSnapshotAttributes'
matchers:
- type: word
words:
- '"all"'
extractors:
- type: dsl
dsl:
- '"RDS snapshot " + snapshot + " is public"'Creating custom templates for specific tasks
Similar to the examples above, users can create their own templates to check AWS cloud services in their environments.
Examples of using Nuclei templates for AWS:
Optimization of cloud resources: Nuclei templates can help check the optimal use of AWS resources. For example, a template can check if caching is enabled in CloudFront or if DNS records are correctly configured in Route 53.
Deployment verification: Templates can check the success of the deployment and the compliance of the deployed version with the expected one. This can be done, for example, using a pipeline in CodePipeline.
Disaster recovery: Templates can check the correctness of resource settings for disaster recovery. For example, you can check if RDS instances are configured to use Multi-AZ deployment.
Security compliance: Templates can help ensure security compliance. For example, a template can check if all S3 buckets are encrypted.
Cost optimization: Templates can check for underutilized EC2 instances that can be terminated or downgraded to a smaller instance type to reduce costs.
Running AWS cloud configuration check templates
To use templates to check cloud configuration, you first need to set up the environment. This setup is similar to using aws-cli, where you either add aws_access_key_id and aws_secret_access_key to the ~/.aws/credentials file or export them as environment variables.
In Nuclei-Templates, we introduced the concept of profiles that allow users to run a specific set of templates designed for a particular use case. To run AWS templates, we have a profile called aws-cloud-config.
After properly setting up the environment, users can run the following template to ensure everything is set up correctly before running the profile.
nuclei -t /path/to/aws-template.yamlIf the template matches, it means that all necessary tools are installed in the environment and the command-line interface is configured. Then users can run the following command to launch all AWS configuration templates.
Currently, in the templates for regional services, the region is hardcoded as us-east-1 in the templates for regional services. Users can pass a different region variable through the command line interface when running the template or update the region directly in the profile file.
Uploading results to the ProjectDiscovery cloud platform
Now we will run a scan using our AWS config scanning profile. Before we start, it will be very useful for pentesters or companies to save the scan results for reporting or making fixes. To simplify this, you can use the -cloud-upload flag to upload the results to PDCP.
To upload the results to the cloud, you need to obtain an authentication token. Here are the steps you need to follow:
Go to the PDCP Cloud page and log in to your account.
Click on your profile picture in the top right corner and select API key.
Copy your API key and enter it in your terminal nuclei -auth
.
Now everything is ready to run the templates!
nuclei -config ~/nuclei-templates/profiles/aws-cloud-config.yml -cloud-uploadNow that we have a lot of results, it would be very convenient to view them in the cloud. Just log in to PDCP Cloud, and you will see the scan created with the results.
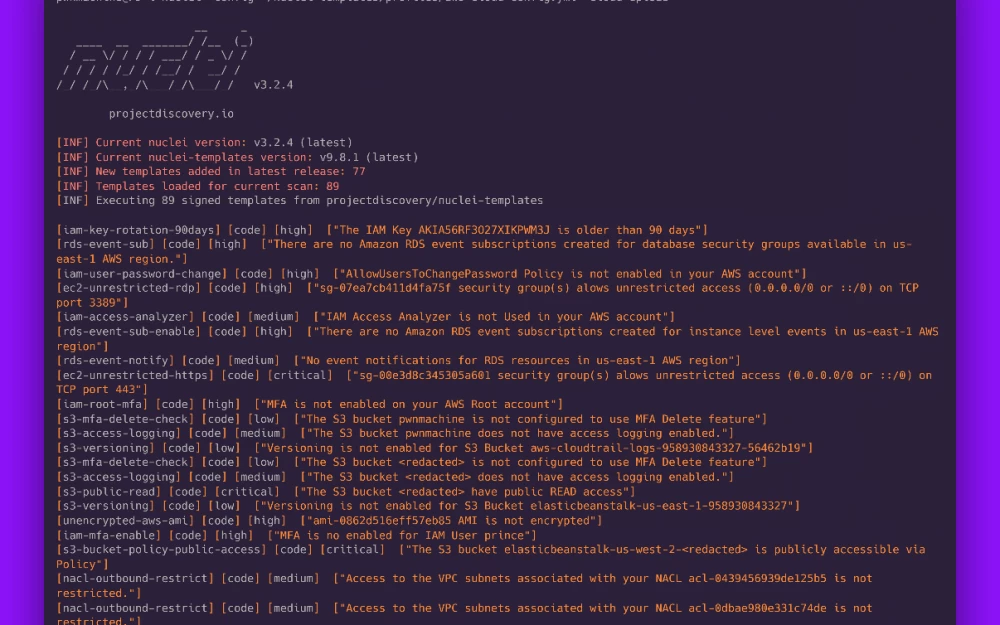
We have added more than 95 templates for services such as ACM, CloudTrail, EC2, RDS, VPC, CloudWatch, IAM, and S3, and we invite the community to share their feedback. We expect this number to grow as the security community continues to contribute and collaborate.
Conclusion
Reviewing cloud configuration with Nuclei is a powerful way to automate security and configuration checks in AWS environments. With the ability to create and execute templates to run commands through the AWS CLI, you can tailor checks based on your organization's specific requirements.
Templates can be used to check various aspects of cloud configuration, including security, cost optimization, and compliance.










Write comment