- Security
- A
How to safely share information in the digital world without revealing yourself?
For example, an open-source project contributor wants to share plans while remaining anonymous.
Situations
Or another example: some tech company is involved in shady dealings and some honest employee wants to stop it. He doesn't know how many like-minded people there are, but he knows for sure that if only one or two people confirm these shady dealings, they will be quickly fired and nothing will change. He writes a message on an anonymous forum and gets support from other users who claim to be his colleagues, but you can't trust this because it could just be a troll.
Or just some topic is forbidden to discuss which you really want to discuss.
What to do? Use ring signatures!
Ring Signature
In a ring signature, unlike a regular one, many public keys are used. Such a set of public keys is called a ring, and to create a valid signature, it is enough to know only one private key from this ring. Thus, the author of the signature hides among other possible authors.
If you take your public key (for which the private key is known) and the public keys of other people, you can make a signature from which it will be unclear who exactly signed it, but it will be known for sure that it was someone from the ring. Both anonymity and authenticity are preserved.
Signature Example
First, let's create a pair of keys. In this example, I will use the OpenSSH format for ED25519 keys
ssh-keygen -t ed25519 -N "" -f demoWe get two files: demo and demo.pub. The contents of the public key file:
> cat demo.pub ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMm1mCqNBuabE7TJtUUVvQUYQEa3TFuOShS9ytPahlx3 vasilii@carbonand the private one (this is a demo, so it's safe to publish):
> cat demo -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW QyNTUxOQAAACDJtZgqjQbmmxO0ybVFFb0FGEBGt0xbjkoUvcrT2oZcdwAAAJjU2/q/1Nv6 vwAAAAtzc2gtZWQyNTUxOQAAACDJtZgqjQbmmxO0ybVFFb0FGEBGt0xbjkoUvcrT2oZcdw AAAEBtElLYWTIfj186r9w8EhF748GQuEVWtDs6jikaUcEK+cm1mCqNBuabE7TJtUUVvQUY QEa3TFuOShS9ytPahlx3AAAADnZhc2lsaWlAY2FyYm9uAQIDBAUGBw== -----END OPENSSH PRIVATE KEY----- Now let's take the public keys we want to blend in with. I took a couple of contributors to React (https://github.com/facebook/react/graphs/contributors) and their public keys from GitHub: https://api.github.com/users/zpao/ssh_signing_keys and https://api.github.com/users/acdlite/ssh_signing_keys
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIM7DuT1T4hHljylm/bTFKg8cGvfafQyI6O+aB1cHM7Yp ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIELtSHIyptiTWlcjVK5HxH+L+AvmcLM3wFNOi7Yqg7UWWe'll add my public key to them, let's say, in the last position, removing the part with the name (it acts as a comment):
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIM7DuT1T4hHljylm/bTFKg8cGvfafQyI6O+aB1cHM7Yp ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIELtSHIyptiTWlcjVK5HxH+L+AvmcLM3wFNOi7Yqg7UW ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMm1mCqNBuabE7TJtUUVvQUYQEa3TFuOShS9ytPahlx3You can create and verify a ring signature on the website https://cryptopoll.org/sign, so let's go there, import our private key (everything happens on the frontend, the key does not go anywhere over the network), write the message in the left field, and the list of public keys in the right field:
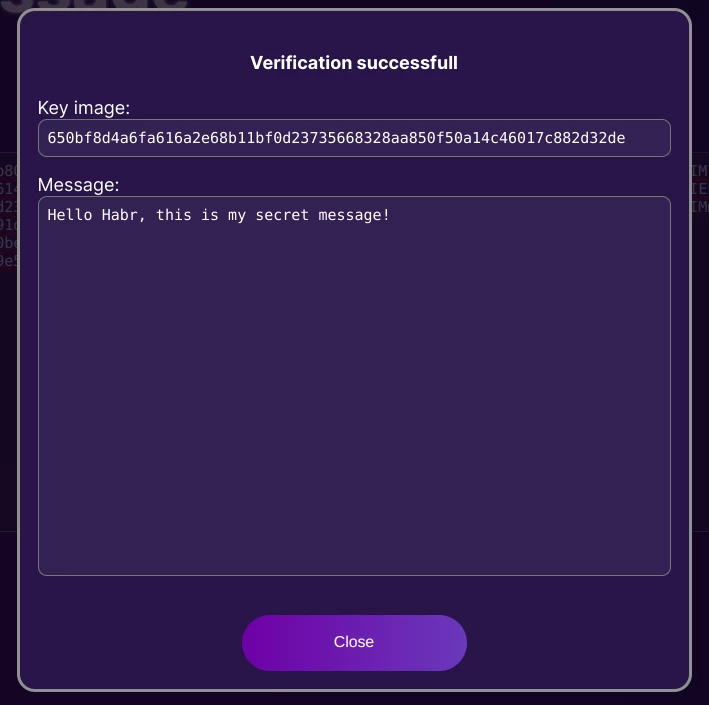
We get a signed message:
{"m":"Hello Habr, this is my secret message!", "mh":"2d84e3b802b62840ff08025d06f3fe03e0c1d67314b2af473c92108318b44452", "pkh":"b7822daca942eafac5e614063f5377ea3e2980baadfd57d02092aac799711a9f", "sig":{"II":"650bf8d4a6fa616a2e68b11bf0d23735668328aa850f50a14c46017c882d32de", "cc":"6180a0d3d2dcf5dde4892d7e4ba62e22a8217f8691d468471f6aee57aa2ded0e", "ss":["2eb3080ebab3bd418c81fd220df62b2ab2f2dc4c8848f2f5c98290be66b46e0a", "7d5b5e5218b4601ab0316869a51077dfe3f62e19956aaccfee39e26d011b5502", "093fa9e5c809120f71b95f92c3eecee42e4be5499470c238a5f8942966b8bc03" ]}}Now you can send it to someone along with the list of public keys:
Hello everyone, here is a message signed by one of us:
{"m":"Hello Habr, this is my secret message!","mh":"2d84e3b802b62840ff08025d06f3fe03e0c1d67314b2af473c92108318b44452","pkh":"b7822daca942eafac5e614063f5377ea3e2980baadfd57d02092aac799711a9f","sig":{"II":"650bf8d4a6fa616a2e68b11bf0d23735668328aa850f50a14c46017c882d32de","cc":"6180a0d3d2dcf5dde4892d7e4ba62e22a8217f8691d468471f6aee57aa2ded0e","ss":["2eb3080ebab3bd418c81fd220df62b2ab2f2dc4c8848f2f5c98290be66b46e0a","7d5b5e5218b4601ab0316869a51077dfe3f62e19956aaccfee39e26d011b5502","093fa9e5c809120f71b95f92c3eecee42e4be5499470c238a5f8942966b8bc03"]}}
The following public keys were used, and you can verify on GitHub that they belong to us: ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIM7DuT1T4hHljylm/bTFKg8cGvfafQyI6O+aB1cHM7Yp ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIELtSHIyptiTWlcjVK5HxH+L+AvmcLM3wFNOi7Yqg7UW ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMm1mCqNBuabE7TJtUUVvQUYQEa3TFuOShS9ytPahlx3Any recipient can check that the keys are indeed on GitHub and that the signature is valid by visiting https://cryptopoll.org/verify
What is this site about?
Ring signatures were invented quite a long time ago, more than 20 years ago. In the real world, these signatures are used in the Monero cryptocurrency, which provides complete anonymity. Since cryptocurrency is worth real money as well as its anonymity, such cryptocode is subject to particularly high security requirements. So far, there is no known method of hacking or deanonymizing ring signatures and their implementation in Monero. The site above is just a copy-paste of the code from the cryptocurrency into WebAssembly, one-to-one as in cryptocurrency transactions.
One message author or different ones?
How to understand that messages are from different authors or from the same one? For this, there is a key image in the ring signature, which is something like a hash of the private key. If the same private key was used to create the signature, then the key image will be the same, even if a different ring is used.
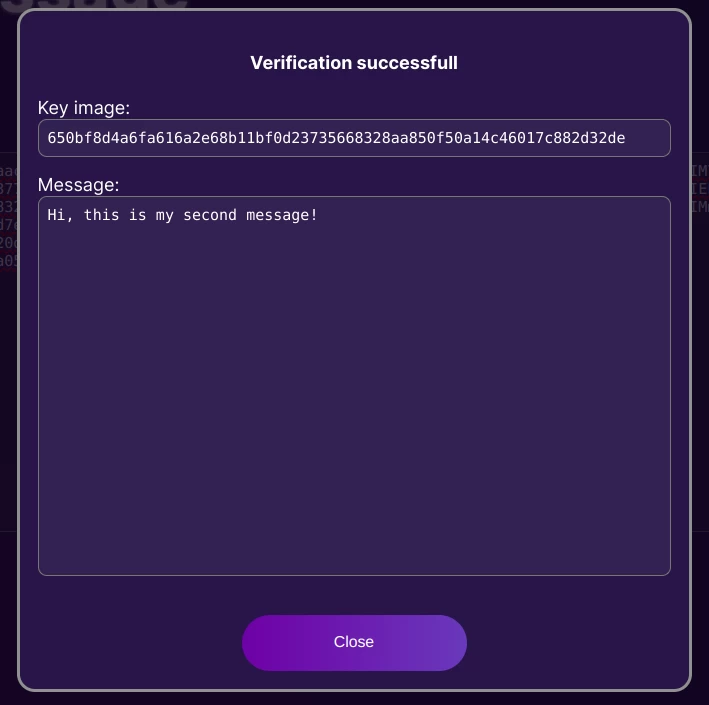
For example, here is another message (the same ring of public keys is used):
{"m":"Hi, this is my second message!",
"mh":"297c352910c386aac52c171beef2099a58432f6307cc7cf67709b48498168af8",
"pkh":"b7822daca942eafac5e614063f5377ea3e2980baadfd57d02092aac799711a9f",
"sig":{"II":"650bf8d4a6fa616a2e68b11bf0d23735668328aa850f50a14c46017c882d32de",
"cc":"190394d0406ec4b2ef04b38f8a86f93a0682cbdd39f3caa4d7e881c723a6fd07",
"ss":["20054842302128c11edc6ec9d806791017c3bbd1f45733ac6a28bb04184bf20d",
"a727e3cb30cdf8e360921ae6f5eca512e7148181322e24f1625aa0c239ac1409",
"70318a843f7e9a052e0f4bff9ccdf69d47558046a0b89d979e8dff1db900110f"
]}}When verifying the signature, we see that the key image 650bf8d4a6fa616a2e68b11bf0d23735668328aa850f50a14c46017c882d32de is exactly the same as before, so we understand that the author of these messages is the same:
Accordingly, when the key image is different, we can be sure that the authors are different.
In Monero, this key image is used to prevent double spending.
Other possible applications of ring signatures
In addition to the examples given at the very beginning, this cryptographic approach can be used for organizing elections or collecting feedback. Anonymity is ensured by the ring, and the presence of a key image ensures protection against double voting.
The initial phase of collecting public keys can be challenging, but since developers quite often add their public keys to GitHub, this platform can be used as a public key registry.
Right now, I can already take the keys of my colleagues from GitHub, take my GitHub key, make a message like "My boss is good," and spread this message on forums or sites like Glassdoor. In this case, accusations of manipulation will be unfounded because it is indeed a message from some employee. Also, if the review is negative, the company will not be able to dismiss it as the machinations of competitors!
Conclusion
Ring signatures are a powerful cryptographic tool that is not yet fully utilized in everyday life but has proven security through many years of use in the Monero cryptocurrency.












Write comment