- Security
- A
Reconnaissance for bug bounty: 8 tools necessary for effective information gathering
Contents
It is well known that reconnaissance is the most important stage in bug bounty and web application penetration testing. Vulnerability hunters who conduct quality reconnaissance receive well-deserved rewards, as they are more likely to discover hidden features and resources. This gives them an advantage and significantly increases the likelihood of finding vulnerabilities.
However, not every vulnerability hunter can afford to spend time and effort on thorough reconnaissance to map all the elements within the scope of the program.
This article is intended to help you better understand what it takes for effective reconnaissance and finding more vulnerabilities in your favorite bug bounty program.
The Importance of Reconnaissance
Reconnaissance plays a key role in bug bounty, being the first stage of any security test or penetration test. Skipping this stage can result in some applications or features within the scope of the program being left unchecked, reducing the likelihood of finding vulnerabilities.
However, reconnaissance is a repetitive and tedious task that needs to be performed every time a new bug bounty program is launched. Fortunately, there are many open-source automated tools that can ease this process. Let's look at the 8 most commonly used tools that vulnerability hunters use to automate reconnaissance.
Automated Tools
In this article, we will discuss 8 main tools that will help you perform a comprehensive scan to gather information about the target. Each of these tools has its own unique advantages, but you can also use alternative means if they suit you better.
Let's start with the first step - asset enumeration using Amass.
Amass
Amass is an open-source tool for in-depth attack surface management developed by OWASP. It is designed to gather information about assets using both passive and active enumeration methods. Amass integrates various data sources and enumeration techniques to help identify all hosts in your target list.
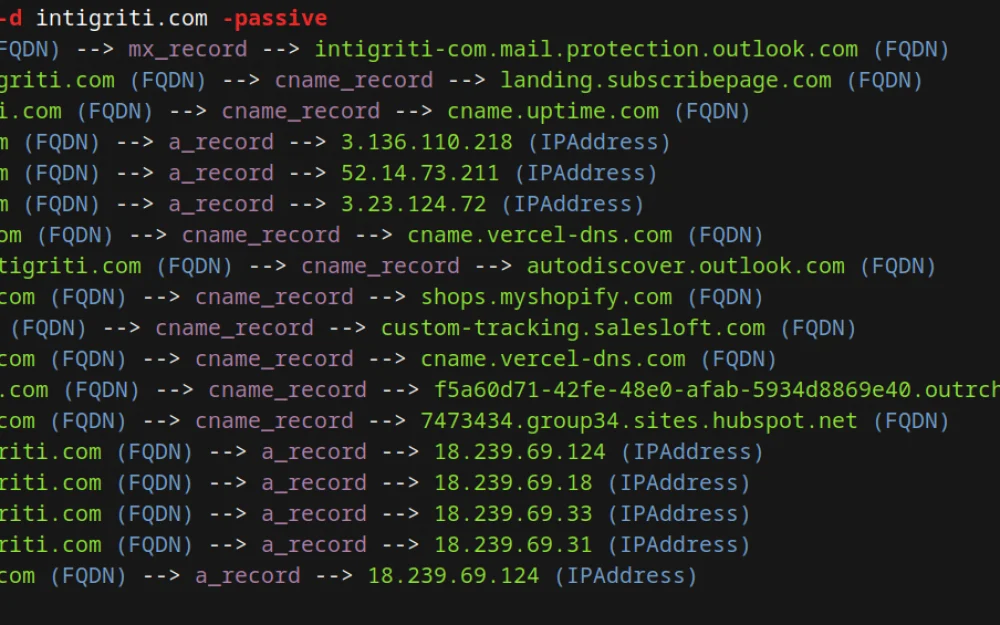
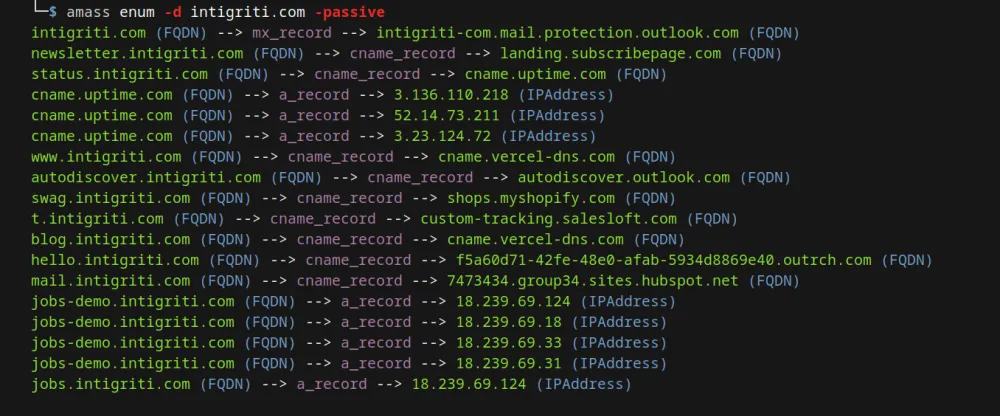
To quickly check subdomains of a root domain (using only passive sources), you can use the following command:
amass enum -d example.com -passiveIf you want to explore the capabilities of Amass further, we have created a detailed guide for you, available on the blog: Link to the article: Hunting for Subdomains.
This tool is also easy to install and configure; it is available on GitHub: Link to the repository: OWASP Amass.
Tip! Configure API keys in the configuration file so that Amass can use more sources and provide more accurate results. Some external sources provide free API keys with limited usage.
Google/Bing/GitHub Dorking
Another way to find related assets or domains of your target is to use search engines.
Search engines allow you to find more information about the target, from indexed files, login panels, and administrative portals to new subdomains. As a vulnerability hunter, you should always use Google, Bing, and GitHub to search for additional information.
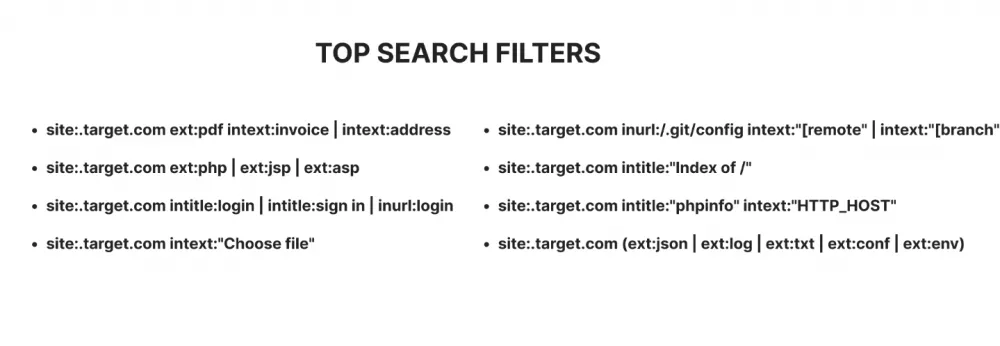
Most commonly used search filters
Below is a list of the most popular search filters that can be used to find interesting indexed files, often containing sensitive data:
GitHub Analysis
Another widely used service is GitHub. Companies often use GitHub to deploy and store code, as well as to organize collaboration.
GitHub reconnaissance is extremely valuable as some companies accidentally upload confidential data to public repositories. This can open access to administrative portals with elevated privileges for unauthorized users. In other cases, you can find links to hidden assets, files, or parameters.
However, analyzing GitHub can be a challenging task, especially when working with a large target, where it is unclear where to start and what to look for. Fortunately, there are tools that make this process easier, such as Trufflehog and Gitleaks.
Trufflehog — a tool for searching secrets and confidential data in code
Gitleaks — a tool for searching for information leaks and confidential data in Git repositories
After you have compiled a list of target systems, hosts, and subdomains, you need to filter out non-working hosts. Eyewitness is a powerful tool that helps not only with checking active hosts and their screenshots but also with performing basic technology analysis. This allows you to quickly browse the list of targets and evaluate each host individually. This approach helps to easily identify login pages (and admin panels) as well as other interesting or suspicious HTTP responses.
Wappalyzer
Technology analysis is a great way to find out what technologies or services your target is running on. However, Eyewitness can only perform basic analysis of active hosts.
To go further, you can use Wappalyzer (a browser extension) or HTTPX (a tool based on Wappalyzer) to analyze the list of targets. Understanding the technologies and services that the target system is running on is the next step in reconnaissance and will greatly help in further vulnerability searching.
GAU (GetAllUrls)
Content discovery plays an important role in reconnaissance, as we discussed in one of our recent articles. Vulnerability hunters who engage in content discovery usually receive good rewards, as they often find unused and untested features, functionalities, and endpoints. This can significantly increase your chances of finding new vulnerabilities.
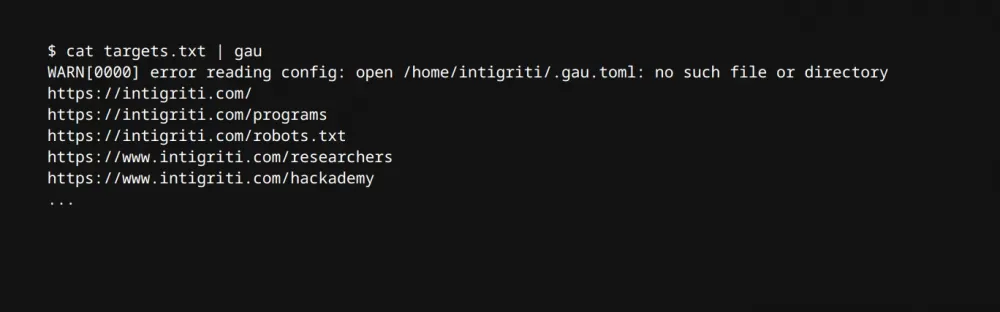
GAU (short for GetAllUrls) is an open-source tool that helps you quickly extract URLs, links, and other indexed files from the Wayback Machine (Internet Archive) and other archiving and indexing systems!
This tool is also easy to use. To return links from a list of target addresses, you can use the following command:
cat targets.txt | gauFfuf
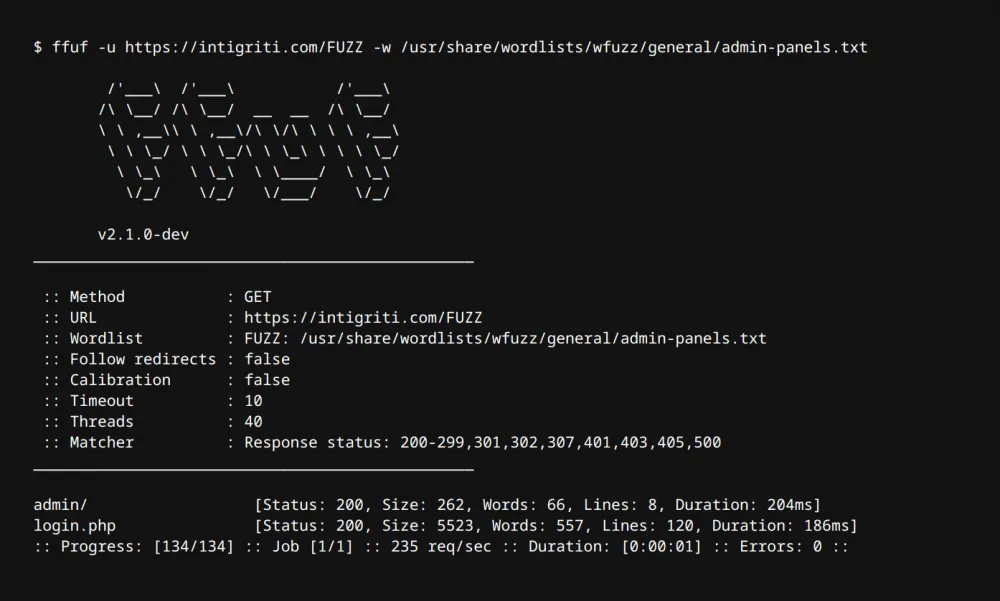
Brute force is another method for identifying hidden API endpoints, admin panels, or other files that were not previously mentioned.
Ffuf is a powerful tool capable of brute-forcing almost anything over the HTTP protocol, from simple content discovery (such as links and files) to virtual hosts and parameters at very high speed!
Here is the command to perform brute-forcing on your target:
ffuf -u https://example.com -w /path/to/wordlist.txtAn article that discusses its capabilities in detail.
Arjun
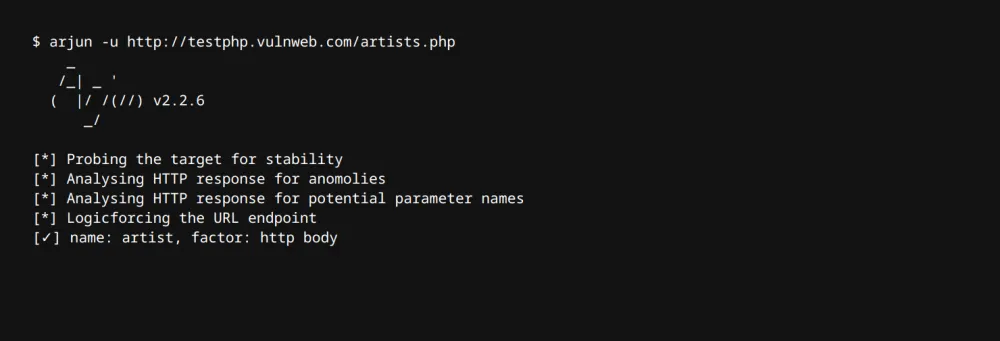
Query parameters and request bodies are places where most user inputs are accepted and where most vulnerabilities occur. Parameter brute-forcing is a reliable way to discover accepted input parameters and trigger unintended actions that often lead to security vulnerabilities.
Arjun is a powerful tool that supports parameter brute-forcing in several different HTTP request bodies and content types:
arjun -u https://example.com/example.phpTip! If you want to brute force parameters using Burp Suite, check out the ParamMiner extension! It can find hidden parameters and is often used to identify vulnerabilities related to web cache poisoning!
LinkFinder
JavaScript files are a treasure trove of information for vulnerability hunters, as they often contain many links and endpoints that could not be found using other content discovery methods.
LinkFinder is a simple tool that does a great job of finding new links, URLs, and other mentioned files and endpoints in JavaScript code.
LinkFinder is also easy to use, here's how to quickly analyze a JavaScript file:
python3 linkfinder.py -i https://example.com/app.jsConclusion
We all know that reconnaissance is an important phase in vulnerability hunting. This article covered the 8 most essential tools that we believe can help you conduct better reconnaissance and increase your chances of finding vulnerabilities in the security system.
Now it's time to test your skills (and new toolkit) in practice!








Write comment