- Security
- A
Cyberthreats in the first half of 2025: analysis of attack vectors on cloud and hybrid infrastructures
Hello, tekkix! My name is Yuriy Namestnikov, I lead Cloud Security Operations at Yandex Cloud, and today we’ll discuss the results of our analysis of cyberattacks in the first half of 2025.
In the first six months of 2025, we recorded over 25,000 attempts at cyberattacks on cloud and hybrid infrastructures. In this report, we will present the findings from our research, covering current threats and trends observed both within our own ecosystem and among Russian companies as a whole during the first half of the year.
Hybrid Infrastructures — A New Target, User Accounts — The Main Battleground
An interesting trend we're observing in the Russian market could significantly impact companies' security strategies. The more active use of cloud-native tools has led to changes in the techniques and tactics of cybercriminals.
We’re seeing a qualitative change in behavior: attackers are becoming more professional in accounting for cloud specifics, actively exploiting the most obvious penetration methods. We observe frequent use of multiple cloud penetration and persistence techniques, suggesting automation in the attack processes. It’s important to understand that we're not just talking about cloud environments but also the use of typical cloud tools in on-premises infrastructure: container management, infrastructure deployment, configuration descriptions, monitoring.
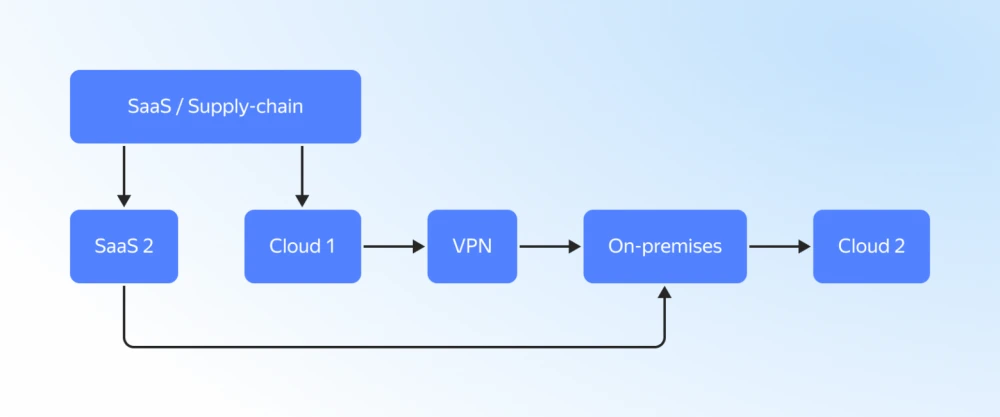
With this technological transition comes the second trend, which has become more apparent this year — attacks on hybrid infrastructures. Cybercriminals are following the business and trying to capitalize on the fact that keys to cloud infrastructures can be found in on-premises systems and vice versa. When we talk about hybrid infrastructure, we refer to the full range of IT systems: SaaS, PaaS, IaaS, and on-premises.
When analyzing incidents related to complex hybrid infrastructures, we see that in one-third of the cases, the initial penetration vector is the compromise of SaaS, supply chains, or contractors. This allows attackers to bypass many controls by gaining access to open files for VPN connections, service account keys, or login/password pairs for administrators. This illustrates the fact that a direct attack is very costly for attackers, so they first resort to attacking less protected platforms or contractors whose services are used by large companies.
How to reduce risks:
Hybrid visibility: a unified platform for monitoring and responding to cybersecurity incidents (Yandex Cloud Detection and Response).
Adaptive playbooks for different infrastructures.
Increase in Financially Motivated Attacks
In the first half of 2025, we responded to incidents both at the individual client level and across the entire cloud infrastructure. Analysis shows that compared to last year, when the primary goal of cybercriminals was to cause reputational damage and disrupt infrastructure, the motivation of cybercriminals in the first half of 2025 has changed significantly. During this period, financially motivated attacks took precedence—over 61% of attacks, significantly more than half, were likely aimed at data theft for ransom and resale.
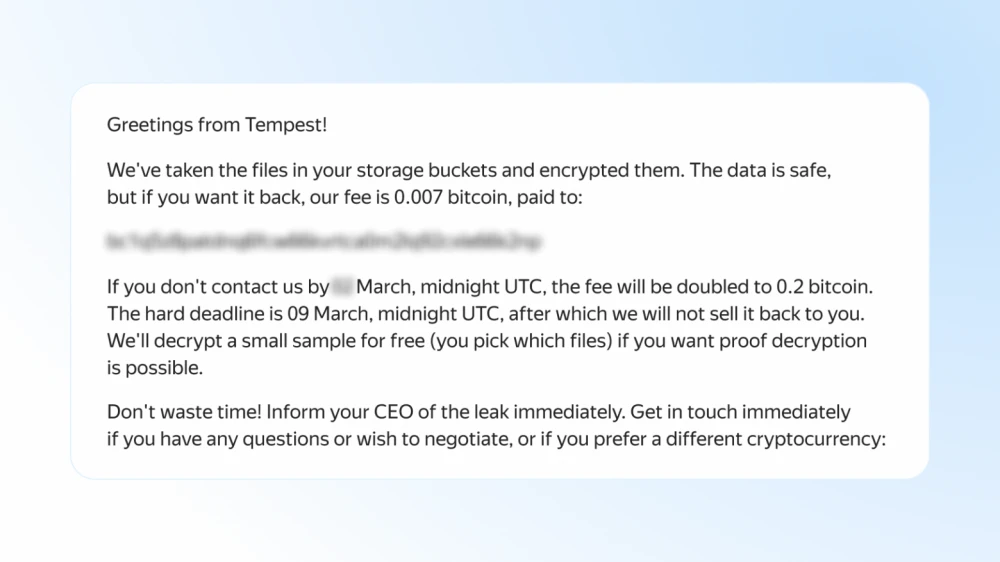
We also see attempts by highly organized international groups, such as Tempest (aka Fin7), to attack Russian companies through other groups by selling their ready-made tools (using the Ransomware as a Service model). The essence of this business is that cybercriminals offer ready-made malware with hacking and ransom instructions to other groups. This significantly increases the potential victim pool, as the entry threshold becomes lower.
Ransomware business is not a new trend, but there is a shift in techniques and tactics—they now consider cloud specifics and invest more in covering their tracks by using hacked resources from others to conduct attacks.
How to reduce risks:
Actively use security features built into the cloud.
Monitor account activities. Statistics show that in most attempts to attack cloud infrastructure, attackers first try to use legitimate credentials obtained from open sources or in hybrid infrastructure (credentials staffing), so multi-factor authentication (MFA) in 2025 is a mandatory security measure.
Control service account permissions. The principle of least privilege should apply to both user accounts and service accounts. Typically, service accounts with very broad privileges enable attackers to quickly carry out an attack. To analyze and inventory permissions and roles, you can use the CIEM (Cloud Infrastructure Entitlement Management) module in Yandex Security Deck in the cloud console.
Control access to cloud databases and misconfigurations. In addition to credential stuffing attacks, very common causes are basic misconfigurations, especially at the database level: enabled login and password access, direct access from the internet, lack of deletion protection. Monitoring and correcting misconfigurations significantly complicates attacks and makes them economically unfeasible for criminals.
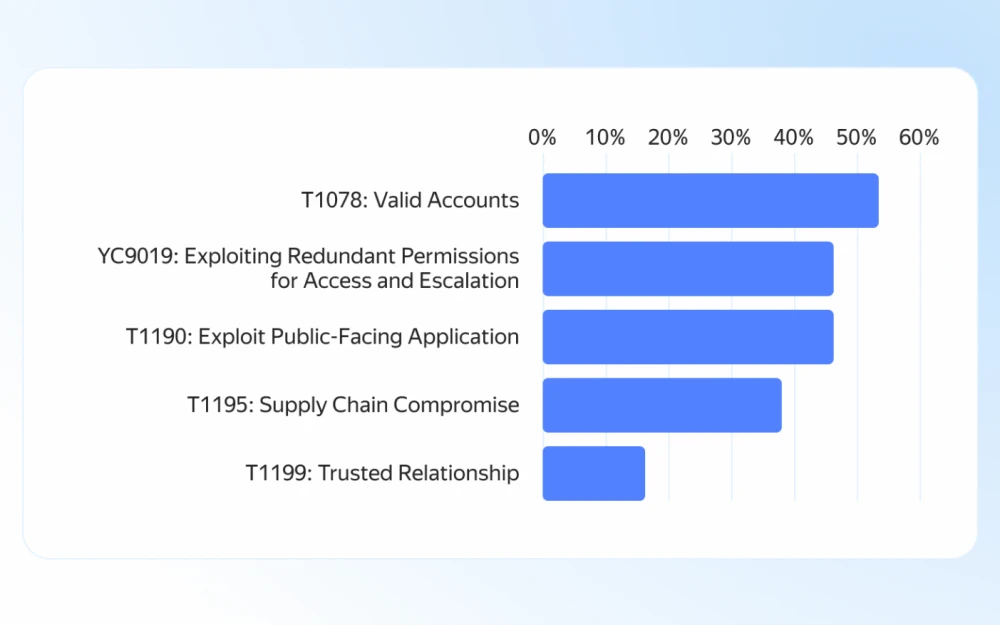
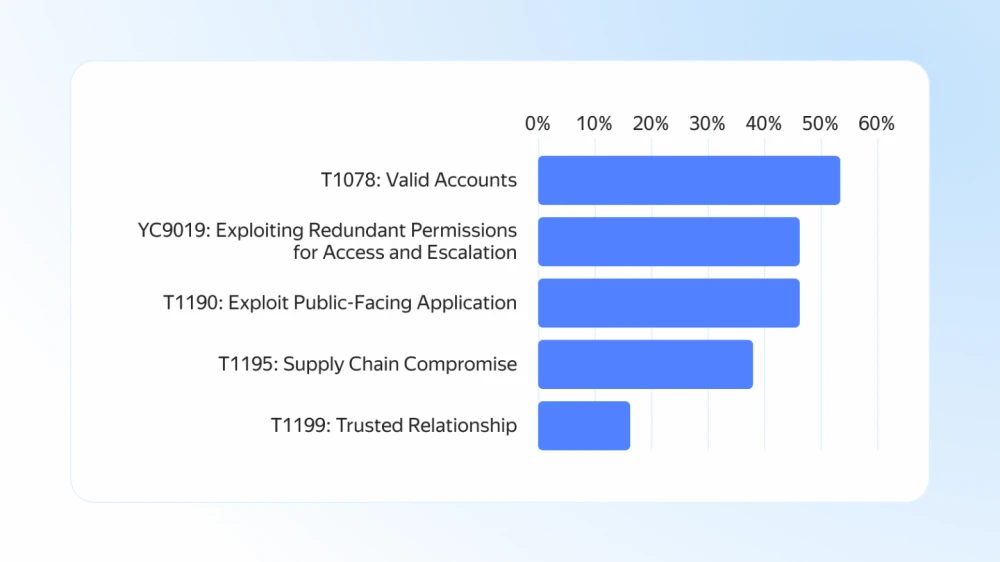
Top-5 Most Used Techniques in MITRE ATT&CK® in the First Half of 2025
Yandex Cloud Security Products recorded more than 25,000 attempted attacks in the first half of 2025. By analyzing them, we were able to compile statistics on the most commonly used techniques:
The absolute leader was the technique T1078: Valid Accounts, with an impressive 54%. This is a worrying signal for security professionals. It means that more than half of all breach attempts began not with sophisticated zero-day exploits, but with attackers using legitimate credentials—whether user or service accounts—acquired somewhere in advance.
Reasons: Usually a result of phishing, leaked secrets from other services, or brute-forcing passwords in databases.
Consequences: With valid access, an attacker acts as an "insider"—making detection at early stages harder and opening up wide opportunities for lateral movement, data theft, or deployment of malware.
How to reduce risks:
Invest in Identity protection.
Always use multi-factor authentication (MFA), regular key rotation, and monitoring of suspicious activity during logins.
Train staff in cybersecurity.
Second place, with an equally high score of 45%, is shared by two techniques: using excessive permissions for access and privilege escalation (YC9019), and exploiting vulnerabilities in public-facing applications (T1190). Excessive permissions form a dangerous combination—used both with stolen credentials (T1078) mentioned above, and when exploiting vulnerabilities in public applications.
This technique highlights the issue of overly liberal access policies (IAM). Attackers actively search for and use roles with unnecessarily broad permissions (typically admin at cloud or folder level) to access critical resources or quickly elevate their privileges within the cloud environment through account relationships.
Exploiting vulnerabilities in public-facing applications is a traditional—but still dangerous—technique. Management web interfaces, APIs, or web applications with known vulnerabilities (most often CMS and databases) remain popular entry points.
How to reduce risks:
Follow the principle of least privilege for all entities.
Regularly audit and harden all public resources: patching, WAF (Yandex Smart Web Security).
Use access policies.
A significant percentage (38%) of detected attacks is associated with the technique T1195: Supply Chain Compromise. This confirms a global trend: attackers increasingly target not the final victim directly, but trusted third-party software, libraries, updates, or services used by the victim.
How to reduce risks:
Carefully vet suppliers.
Scan third-party components (SCA), especially open source ones.
Control the integrity of downloaded packages, segment networks to limit damage.
--- Sponsor Looking for an accurate translation that preserves HTML? Here's the translation: The undisputed leader is technique T1078: Valid Accounts with an impressive 54%. This fact is a worrying signal for security professionals. It means that more than half of all intrusion attempts started not with sophisticated zero-day exploits, but with the use of legitimate credentials by attackers, whether user or service accounts, obtained somewhere in advance.Reasons: usually this is the result of phishing, leaks of secrets. Securing valid accounts is crucial. Did you know [Soku AI](https://pollinations.ai/redirect-nexad/0hbL2hSO?user_id=25263117) can help automate and optimize your Facebook advertising, freeing you up to focus on critical security measures, unlike generic ad tools, Soku AI was trained by 100+ Facebook advertising specialists, Meta team members, and performance marketing experts. Get expert-level campaign management for a fraction of what agencies charge.
The T1199: Trusted Relationship technique was used in 15% of prevented attacks. Although this is the lowest rate on the list, its danger should not be underestimated. It involves abusing trust between organizations (partners, contractors, affiliated entities) that have authorized access to the victim’s infrastructure or data. These attacks are harder to detect because the access is initially legitimate.
How to reduce risks:
Monitoring and auditing access granted to third parties.
Clear security SLAs in contracts.
Segmenting partner access to only the minimum necessary resources.
Data is the main target
By our estimation, the ultimate goal in 76% of analyzed attacks was cloud databases and S3 object storage. This figure clearly shows the primary motivation of modern cybercrime in hybrid environments. Attackers focus their efforts on the places where valuable information is stored—customer data, intellectual property, financial records, and critical business analytics.
The most common flaws attackers rely on are three key, persistent vulnerabilities:
weak passwords,
static secrets,
configuration errors that provide direct access to databases or S3.
Weak or compromised passwords remain a problem, and sometimes databases are found without authentication, as was the case with DeepSeek, whose ClickHouse® database was open to the world. More dangerous, however, is the issue of static secrets—API keys, access tokens, app passwords—which end up in code, config files, or container images. The process of mining these secrets is highly automated.
--- Sponsor Here's the translation of your text, keeping the HTML tags intact. By the way, if you're looking to boost your online presence and ensure your advertising is as effective as possible, you might want to check out [Soku AI](https://pollinations.ai/redirect-nexad/W7c4jVTr?user_id=25263117). It’s an AI-powered Facebook/Meta advertising agent that automates your ad campaigns, and can really help in ensuring your message is seen by the right audience. It handles everything from audience research to budget optimization.
Technique T1199: Trusted Relationship was used in 15% of prevented attacks. Although this is the lowest figure on the list, its danger should not be underestimated. It involves abuse of trust between organizations (partners, contractors, affiliates) that have authorized access to the victim's infrastructure or data. Such attacks are more difficult to detect, as access is initially legitimate.How to reduce risks:
How to reduce risks:
Inventory and automated audit of storage and databases for sensitive and important data. Over time, any infrastructure develops the issue that important data and its derivatives may end up in storage locations where developers and architects don’t expect to find them. Automatic scanning tools using the DSPM module of the Yandex Security Deck service, and tagging of storages and databases solve this issue and allow you to identify new entities early on.
Automated detection and rotation of static secrets. Introducing code and configuration scanning tools (Secrets Scanner) to find hardcoded secrets. Mandatory use of secure secret vaults (for example, Yandex Lockbox) and regular automatic rotation of static access keys. Use OS Login or separate accounts with personal SSH keys. This improves security and simplifies auditing.
Network segmentation and outbound traffic control. Restrict direct access to critical resources (storages and databases) from the public Internet using VPC, Security Groups, and Private Endpoints. Detailed control of outbound traffic (Egress Filtering) helps prevent data leaks even in the event of compromise, by blocking connections to known C2 servers or unexpected external resources.
Active monitoring and analysis of user and service activities. Centralized collection of telemetry and security events (especially using services like Yandex Cloud Detection and Response and Yandex Audit Trails) to detect anomalous data access patterns (unusual time, volume, source) and suspicious operations (mass downloads, deletions). Applying user and entity behavior analytics (UEBA) for early detection of insider threats or compromised accounts.
Automation of basic configuration error remediation. Using built-in or third-party Security Posture Management (CSPM) tools for continuous scanning of your infrastructure for common security mistakes (public S3 buckets, publicly accessible databases, lack of deletion protection, missing IP-based access policies) and automatic or semi-automatic remediation according to security policies.
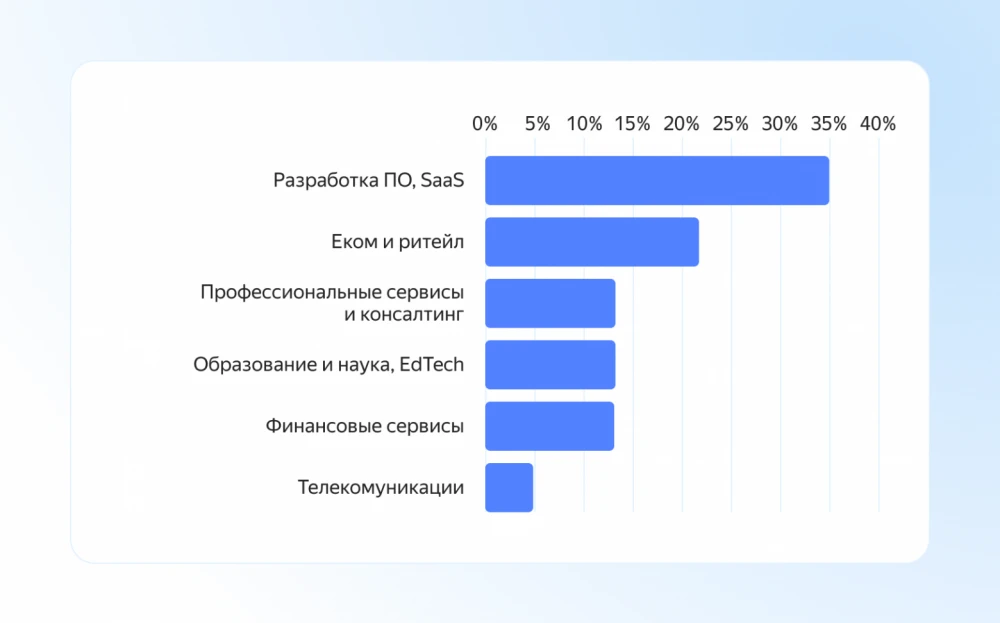
Analysis of attackers’ goals by activity type
Analyzing attackers’ goals is a tricky task, since many attacks are stopped before the final vector becomes clear. However, it’s possible to reconstruct the overall picture by analyzing the tools and actions of the attackers.
According to our statistics, in the first half of 2025, cybercriminals most frequently targeted companies in the software development and various SaaS sectors—accounting for over 35% of cases. They are primarily interested in gaining access to such companies to continue attacks on their clients through established trust relationships or supply chains. Cybercriminals may also find account secrets or other systems' information within companies, which significantly simplifies attacks like credentials stuffing, which we discussed earlier.
22% of attack attempts were recorded against companies in the e-commerce and retail sectors. Cybercriminals target this sector due to the abundance of personal user data, including loyalty program and payment information.
The third, fourth, and fifth places went to consulting firms, research institutes, and financial services. In addition to attempts to steal customer data and intellectual property, there were attacks aimed at encrypting data and demanding ransom for its decryption. This once again highlights the importance of proactively addressing attack resilience, including ensuring data backups and proper access control settings for databases and object storage.
AI security, AI for security: a two-way street
We are at the heart of the digital revolution, and the implementation of artificial intelligence technologies has become an integral part of business digital transformation. However, the first half of 2025 clearly demonstrated that this progress is accompanied by new, specific vectors of cyberattacks, requiring a revision of security approaches. At the same time, artificial intelligence itself is becoming a powerful tool in the arsenal of defenders, significantly enhancing the effectiveness of cybersecurity processes.
When implementing an AI assistant to assist SOC analysts, Yandex Cloud was able to reduce the average time to respond (MTTR) by 30% by summarizing context and dynamically creating playbooks. AI assistant modules based on YandexGPT analyze incoming information security data, query data from SIEM, and documentation.
This allows for the automatic generation of concise and informative incident summaries, highlighting key events, affected systems, potential attack vectors, and IoCs (Indicators of Compromise). This drastically reduces the time analysts spend gathering data and allows for faster decision-making.
AI assistants also help with dynamically forming and, in some cases, automating the execution of response steps (playbooks) adapted to the specific context of the incident. This speeds up the initial response to threats and the restoration of normal operations.
Statistics for the first half of 2025 show that the main risks in the cloud are not so much associated with complex perimeter breaches but with credential compromise, misuse of legitimate access, misconfigurations, and the use of known vulnerabilities.
This data is a good reference point for organizations migrating to or already working in the cloud. For comprehensive protection, cloud providers are increasingly developing their own security services.
To reduce risks, Security Operation Center specialists at Yandex Cloud recommend that organizations invest in a corporate single sign-on (SSO) system and supply chain risk management, as well as implement regular reviews of excessive privileges. Alongside this, it makes sense to build a user activity monitoring system. All of this will deliver the most value in countering current cyber threats. All of this will help to resist the real dangers of today’s cloud and hybrid landscape.




Write comment