- Security
- A
Alice, Bob, Eve, and Mallory — the incredible life of cryptographic characters
How does a VPN work? How does a service bundle work for reliable and secure data transmission between branches and remote employees? What is quantum communication?
Often, when answering these questions, experts give examples with characters Alice and Bob. In the cryptographic world, these names have long become common. The characters appear in textbooks, scientific articles, and lectures, explaining the work of various systems and protocols for data exchange.
Today we will discuss how Alice and Bob appeared and what role they play in science and popular culture.
First mentions
In 1978, one of the landmark works in the field of cryptography was published — "A Method for Obtaining Digital Signatures and Public-Key Cryptosystems". Young scientists Ronald Rivest, Adi Shamir, and Leonard Adleman proposed an asymmetric encryption algorithm with a public and private key — RSA (the abbreviation contains the first letters of the authors' surnames in Latin). This was not the first work of the scientists, but it was the one that gained fame and spread in the community.
The authors chose an unusual approach to illustrating the work of the data exchange protocol. If earlier standard users "A" and "B" were used to denote actors, the RSA team brought academic language to life by adding characters — Alice and Bob. In the publication, they send each other confidential messages and also use digital signatures to verify the authenticity of documents.
Over time, the characters only became more entrenched in science. So, in the same year, mathematician and Turing Award laureate Michael Rabin published a work on information exchange using the oblivious transfer mechanism. The first sentence of the article began with the words: "Bob and Alice have a secret...".
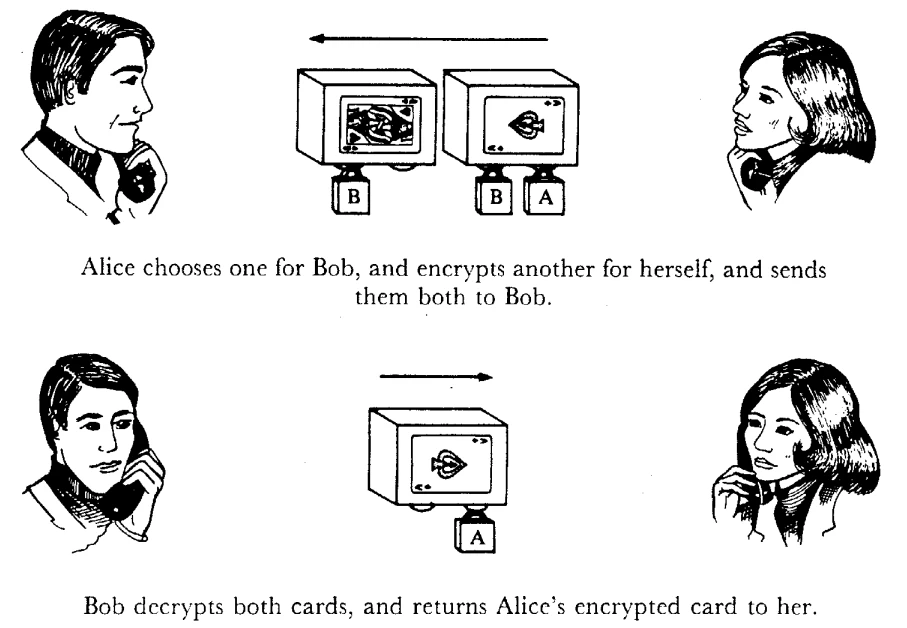
Subsequently, Alice and Bob became the heroes of numerous articles and thousands of scientific situations. At first, they included the exchange of encrypted messages, and then authentication protocols appeared, where Alice and Bob confirmed their identities. Key distribution scenarios and the use of electronic signatures, as well as zero-knowledge protocols, where Alice proved to Bob that she knew the secret without revealing it, took an important place.
Formation
A turning point in the history of the characters was the article by the scientist in the field of computational systems theory Manuel Blum "Coin Flipping by Telephone: A Protocol for Solving Impossible Problems", published in 1981. In it, he first outlined the context in which Alice and Bob operate: he vividly described the situation, introduced the characters, and gave them character. Blum wrote that Alice and Bob had just divorced, lived in different cities, and were trying to figure out who would get the car. They wanted to resolve the issue by flipping a coin over the phone.
Three years after Blum's report, scientist John Gordon gave a famous speech at the Zurich Seminar on Coding Theory, Ciphers, and Standardization. In his speech, the speaker actively used the personalities of Alice and Bob. For example, Bob worked as a stockbroker and actively sold shares to speculators. Alice bought shares from Bob, showing interest in speculation, but tried to hide it from her husband. The characters were forced to communicate via expensive telephone communication and sought to minimize costs. The quality of the channel and the regulators, who constantly listened to their conversations, complicated the matter. Malicious callers often called Alice, posing as Bob, while Alice had not heard his voice before.
Later, Gordon called this speech the first case when the story of the characters was so closely and vividly integrated into the report. Thus, eight years after their appearance, the characters became tropes in the cryptographic field.
Other heroes
Soon Alice and Bob had opponents. The first was Eve (from the English eavesdropper), invented by Charles Bennett and colleagues in 1985. In the publication "How to Reduce Your Enemy's Information (Extended Abstract)", Alice and Bob faced a problem: the seemingly secure communication channel became imperfect. Errors occurred during data transmission, and a third party, Eve, could arbitrarily substitute messages.
In early publications, Eve's moral character was not described. She simply collected information and did not wish harm to either Alice or Bob. But over time, Eve began to be assigned negative roles, such as a jilted wife eavesdropping on her husband's conversations with Alice, or, conversely, a mistress.
Another character, Trent, is a kind of neutral third party. For example, in the description of the Otway-Rees protocol, which allows key distribution without using timestamps, Trent acts as a trusted center known to both Alice and Bob. In the case of the Needham-Schroeder protocol, the participant Trent also plays the role of an authentication server.
Gradually, the cryptographic community invented a whole gallery of characters. Mallory (malicious) became the embodiment of an evil attacker. Another character, Carol, appears as a third participant in the connection. Oscar, whose name comes from the word opponent, acts as another attacker. Grace represents government agencies that monitor Alice and Bob and try to prevent them from exchanging messages.
Cultural Phenomenon
One of the authors of RSA, Ronald Rivest, said that Alice and Bob appeared due to his love for the work "Alice in Wonderland". The characters themselves became heroes of mass culture back in the nineties. For example, in the game Game Builder Garage, which offers to learn the basics of programming and game development, the helper spheres are named Alice and Bob. And in Remember11, one of the characters gives an example with Alice and Bob when explaining the principles of quantum teleportation.
Also, Alice and Bob are the subjects of many jokes and even rap songs. More obviously, they became the heroes of one of the covers of Physics World magazine and the mascot of the RSA International Conference on Information Security.
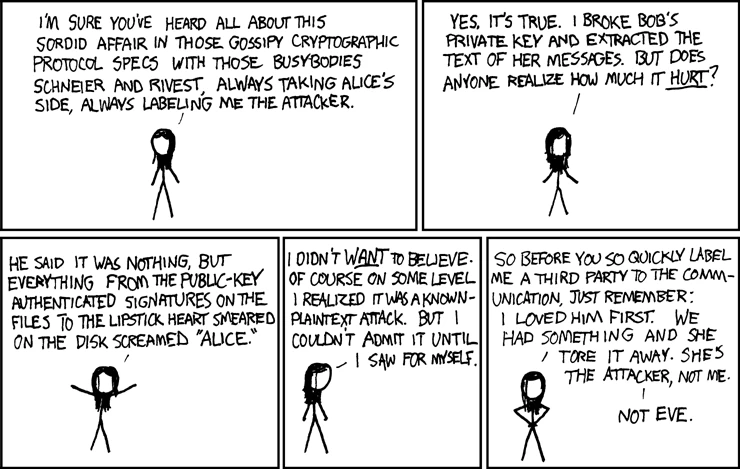
Alice and Bob appeared in xkcd comics. For example, in issue 177, Eve claims that she doesn't like the role of the "third party" and that she, not Alice, was the first to fall in love with Bob.
In episode 1323, it is described how to make a programmer listen to any boring story: just tell it using the characters Alice, Bob, and Eve.
And the comic 2691 is dedicated to a new secure messaging app that allows Alices to send messages only to Bobs and no one else.
Adaptation and future of the characters
Alice, Bob, and friends are used by specialists in the field of cryptography around the world. Against this background, some scientists want to revise and adapt such names to match the culture of their countries. For example, one specialist from India suggested using the names Sita and Rama from the epic "Ramayana" to illustrate cryptographic protocols. Among the advantages, the author of the initiative notes that the first letters of the names Sita and Rama coincide with the standard designations of the sender (sender) and receiver (receiver).
There is also an opinion that Alice and Bob should be completely abandoned. In 2015, scientist Philip Rogaway published an article "The Moral Character of Cryptographic Work," in which he expressed the opinion that the use of characters increases cognitive load — it is harder for the reader to understand the technical side of the issue through the story of Alice and Bob. Rogaway also believes that the excessive simplification of scientific articles leads to many underestimating the importance of cryptography and perceiving it as unserious.
But there is a counterargument to Rogavey's statement. Researchers in the field of narrative psychology believe that people perceive information presented as a story much more easily. Alice and Bob bring complex concepts to life and allow us to understand how the described scenarios are applied in real life. Therefore, Alice, Bob, and Eve remain relevant and have gone far beyond the academic sphere.








Write comment