According to the tag crypto, the following results have been found:
Hello everyone! Sergey Sobolev is here, a specialist in distributed systems security at Positive Technologies, our team is engaged in auditing smart contracts. Today I will tell you about the results of our team's research and conclusions regarding the security audit of smart contracts in the FunC and Tact languages of the TON platform.
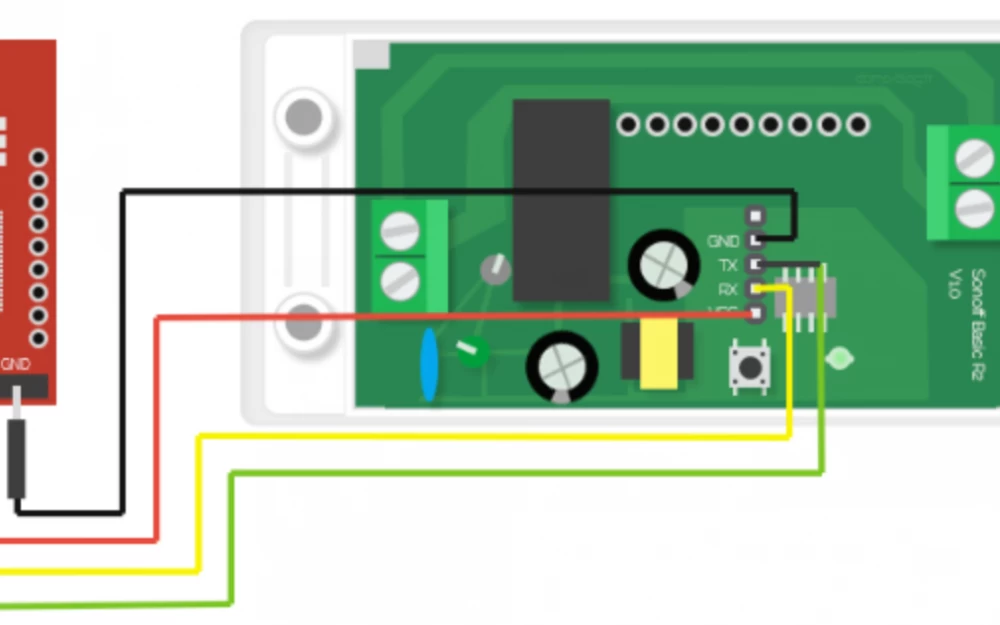
This project — A simple way to use cryptocurrencies to control devices.
Among the bright symbols of the Middle Ages are sorcerers, witches, and alchemists who "enchant and turn mercury into gold." Cryptography at this time also went hand in hand with magic: take, for example, the ciphers of occult communities.
For decades, backups have primarily protected us from physical equipment failure and accidental data corruption. A good backup system should survive a fire, a flood, and then quickly enable the business to continue normal operations. But another problem has emerged, which is much more likely than a flood and from which fireproof barriers and physical separation of sites in different cities do not save.
This article opens a series of materials dedicated to the problems of the modern internet, its centralization, and possible solutions. The introductory article reveals the main issue: how the internet, conceived as a free and decentralized space, has turned into a controlled and centralized network. Here and in the following articles, I will present a detailed analysis of the decentralization technology I have developed, which can offer a solution to overcome these problems.
Hello! Today we continue to implement encryption. In this article, we will look at the Magma cipher algorithm, which was developed and used in the USSR.
How does a VPN work? How does a service bundle work for reliable and secure data transmission between branches and remote employees? What is quantum communication?
I will briefly introduce the age encryption tool. We will learn to encrypt both personal and corporate backups with one simple command, and then argue about why openssl is such a bad tool and not suitable for practical use by ordinary users/admins whose understanding of crypto algorithms is roughly expressed in the KDPV.
For example, an open-source project contributor wants to share plans while remaining anonymous.
Machine learning is now used to a greater or lesser extent in various industries. Cryptographic analysis is no exception. In this article, we will look at the CipherGAN generative adversarial network, which is used to determine the basic encryption mapping from banks of unpaired encrypted text and plaintext.