- Security
- A
Top cybersecurity news for December 2024
Hello everyone! We are closing the year with our traditional news digest. December was rich in spyware news: Pegasus was highlighted due to the won Whatsapp case, its competitor Paragon was bought by the USA, another scandal unfolded in Serbia, and unknown Chinese spyware was discovered.
In addition, the estimates of Russian data leaks were disappointing, as were the amounts of cryptocurrency stolen in 2024. Cl0p hacked another file manager with far-reaching consequences, and Europol forcibly brought Matrix secure communication platform users into harsh reality. Read about this and other interesting events of the last month of the outgoing year below!
Russian data leaks: the bottom is the new frontier
At the end of the year, we have disappointing statistics: data from 59% of Russian companies is available on the darknet and Telegram. These are the realities at the end of 2024. This year, the number of corporate data leaks reached 16 thousand, which is 60 percent more than the previous year.
Phishing is still at the top - it accounted for 44% of successful attacks, and in most cases, emails are disguised as invoices and payment documents, sometimes from hacked contractor accounts. The most attacked companies are still in the financial, IT, and real estate sectors. According to our data, in the spring of 2024, the number of attacks increased 80 times compared to the previous year.
While businesses are slowly exploring the wonderful world of information security and the restrictions imposed by the presence of experienced and motivated attackers, the numbers are growing exponentially. To some extent, this can be called the side effects of geopolitical splits on the cybercrime scene in the CIS, which has voluntarily and involuntarily turned into hacktivists over the past three years. You could even write research papers based on this, although it is unlikely that you will find a scientific advisor for such a topic.
Outlook for 2025: Cl0p hacks Cleo
Cl0p closes the outgoing year with a new large-scale hack: another compromised file transfer platform — the group's specialization lately, another long list of affected companies. The attackers threaten to publish the names of 66 organizations if they do not get in touch. Considering that people only want to leave the office until January, it turned out awkward.
This time Cl0p hacked Cleo's software. In October, the developer fixed a zero-day that was exploited to install backdoors. Unfortunately, the fix was unsuccessful — the patch did not solve the problem, the exploit was still possible. A couple of weeks ago, the vulnerability received a new CVE and a fix, but it was too late. Companies have already been hit by an infostealer.
The number of victims is still unknown, but Cleo claims to have more than 4,000 clients. So if Cl0p has repeated the MOVEit story even on a minimal scale, we can already say that the holiday season has not worked out for many companies. Only the victims of previous attacks can breathe a sigh of relief — the group promised to leave them alone, stating that they deleted the data from previous attacks to focus on hacking Cleo. Our condolences to the rest.
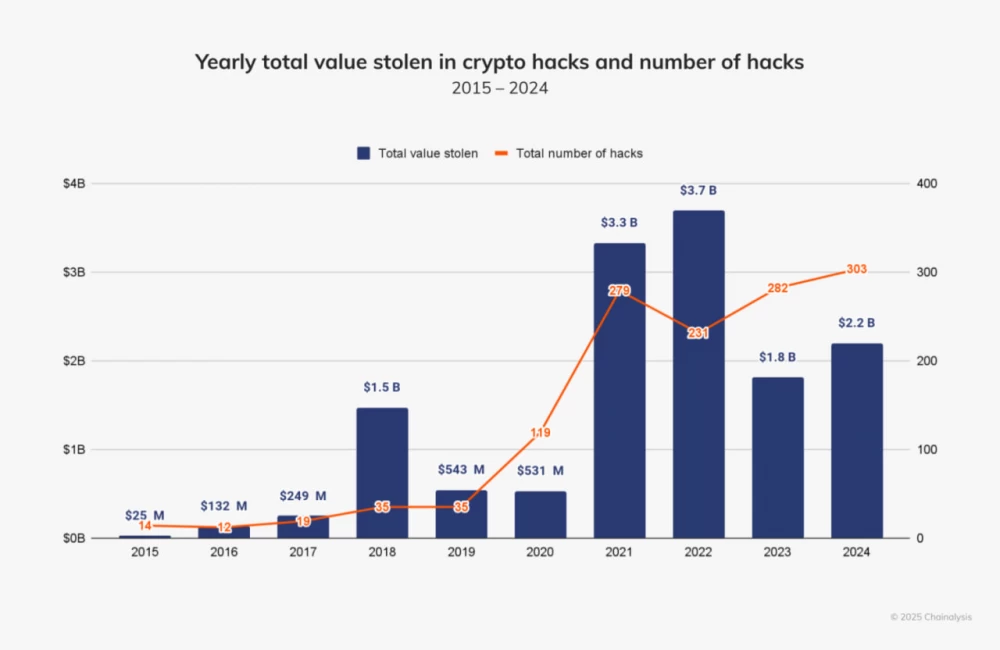
Crypto thefts of 2024 and the hard work of North Korean Stakhanovites
We close 2024 with new records from the world of crypto theft: the number of recorded attacks for the year is 303. A total of $2.2 billion was stolen, which still pales in comparison to the bountiful 2022 for the North Korean budget and beyond, closed at an impressive $3.7 billion.
Compromise of private keys still rules the roost: almost half of the funds were stolen due to the low culture of basic infosec among holders of solid crypto stashes. The year was also marked by the return of attacks on centralized platforms: the hacks of the WazirX and DMM Bitcoin exchanges accounted for half a billion stolen. The latter eventually closed.
At the same time, the activity of crypto miners from the DPRK mysteriously decreased sharply in the middle of the year, which gave rise to speculations with a geopolitical flavor. If this had not happened, the year could have been unprecedented in terms of the amount of thefts. But the strategic brothers still set their personal record: they expropriated $1.3 billion, which is twice the result in 2023. The party is proud of you, IT soldier! You are the building philosophy of the Juche idea!
Regarding the North Koreans. In December, it became known that their scheme of employment in Western companies brought at least $88 million to the DPRK budget over the past six years. This conclusion was reached by the State Department, sharing the details of a cunning cybercriminal scam.
North Korean infiltrators worked from two front companies. There were more than 130 people in them, and within the company, they were actually called "IT soldiers". The task of a North Korean IT soldier is to earn $10,000 a month for the benefit of the party and pull proprietary code for blackmail.
The FBI warns that this is just the tip of the iceberg: the DPRK has allegedly trained thousands of IT specialists under this scheme, and they threaten American companies every day, and cases of theft and data leaks are becoming more frequent. The transformation of the DPRK into a dashing cyberpunk Tortuga is perhaps the most amusing event in the industry in recent years.
Arrests and charges against cybercriminals
In the past month, the US charged the LockBit developer. Russian and Israeli citizen Rostislav Panev participated in the development and administered the group's infrastructure. The US Department of Justice is seeking his extradition after his arrest in August.
Unlike other cases of the "Did they take the right one?" format, everything is simple with Panev: an account from the repository with the source codes of several versions of the LockBit builder was found on his devices. It also contained the source code of StealBit, the leaked source codes of Conti, on the basis of which LockBit Green was assembled... In general, a full set.
In addition, Panev was in contact with comrade Khoroshev and discussed the development of malware and control panel in correspondence. And during interrogations by the Israeli police, he allegedly already confessed. So the year for LockBit started not very well, continued even worse, and is also ending on a minor note. The final life cycle of a ransomware operation is like that. In a word, depressing.
At the same time, the group expects a triumphant return in 2025. It is customary to dream about the future on New Year's Eve. The remnants of LockBit also dream: of luxury cars and available women. More precisely, that promises of these will attract partners for the release of the LockBit 4.0 encryptor. It is scheduled for February 3, it was announced at the beginning of the year, and little remains of the group's reputation. And the ransomware scene in the vacuum that formed this year was taken over by RansomHub. It is considered the key threat for the next year, so LockBit's chances of becoming a ransomware star again are low.
In December, a hacker from the "Com" group, associated with the high-profile spring hacking of 165 companies through the Snowflake cloud service, as well as swatting, crypto thefts, and other entertainments of Western cybercriminal youth, was arrested in Canada. The online persona Waifu was a 25-year-old Canadian.
The profile, as in the case of many other Western cybercriminals, is telling. Autistic, did not finish school due to bullying, lived with his grandfather. Where in the CIS the average cybercriminal is a respected piglet with a helicopter, Lamborghini, and connections, English-speaking ones are often troubled teenagers sitting on a pile of crypto in front of two monitors.
Comrade Waifu also distinguished himself by the fact that until the day of his capture, he regularly corresponded with Krebs, offering to play chess with him in exchange for an honest conversation. Following the arrest, the WSJ recalls the deep lore of Krebs, including how Vovnenko sent him heroin. It's time to refresh the classics in memory.
Spyware cases
December was marked by numerous news about spyware. Thus, Whatsapp achieved a major legal victory over NSO Group: the court sided with the messenger in the Pegasus case. And found the company responsible for hacking 1,400 devices. This is the first successful case of this kind against NSO.
At the same time, the judge criticized NSO Group for obstructing the case: the company did not provide complete source codes, which was one of the key factors in favor of the decision. The company was also accused of violating Whatsapp's ToS. In general, as a result of the case, we not only have insights into the internal workings of the spyware developer, confirming that the company acts as an operator for clients, but also a serious precedent.
Damage proceedings against Whatsapp will begin in March. And then, perhaps, NSO and the company will be able to act with less impunity under the rhetoric of "a safer world" and other not very convincing approaches from their marketers.
The company iVerify, which developed software for detecting spyware, in December shared the results of their work. Of the 2,500 devices they checked, 7 were compromised by Pegasus. The number may seem low, especially considering the target audience of the software, but the very fact that a non-selective scan found infections is already alarming.
The most interesting thing in the report is different. Among the victims were not only journalists and opposition, but also businessmen, managers, and government officials. In other words, the dirty reputation of "spyware for hire, which is abused for tracking activists" is not the limit for NSO Group.
And as a result of the analysis, it may well turn out that the profile of Pegasus's work is essentially no different from that of an average state hacker group or MaaS operation. As usual, the bottom is the new frontier. However, raise your hand if you will be surprised if "former" intelligence officers on a short leash of Mossad work in the APT format.
Last month, researchers discovered undocumented spyware, this time Chinese. Unlike the countries of elves, where dubious software is brought into the private sector for plausible deniability and other digital expertise, in China it's simple: C2 hangs on police domains. And the admin panel is called the "Legal Stability Maintenance System". Why should they be shy.
The spyware has been used since at least 2017, is actively developed, and works on Android and iOS. It collects call records, contacts, messages from messengers, geolocation data, and files, records the screen and audio. They don't bother with installation either: the spyware is installed when the device is seized during a search.
In other words, recommendations for business trips to China with disposable phones and empty laptops are not excessive caution, but a vital necessity. More details about the discovery in the report.
Another spyware scandal is also brewing in Serbia. According to an Amnesty International report, journalists, activists, and environmentalists were monitored in the country. For this purpose, the Serbian brothers had their own spyware NoviSpy, which was installed during arrests and interrogations. Call logs, contacts, and correspondence, audio recording, and screenshots were all collected as expected.
The story is spiced up by the fact that initial access to the phones was obtained using software from Cellebrite - its traces were found on the devices in addition to the spyware itself. So, under the guise of digital expertise and crime fighting, another violation of rights is taking place.
Cellebrite has already expressed deep concern, referred to its ToS with a nominal mention of human rights, and promises to "revoke the license" for its software from the Serbian authorities if the information is confirmed (as they revoked it, for example, from the Chinese). This has never happened before, and here it is again.
And finally, in December, a private investment company in the USA acquired the Israeli spyware developer Paragon. The latter work without attracting attention, but at the same time they are direct competitors of NSO Group in friendly rivalry with comrades from unit 8200.
Paragon's key product, the spyware Graphite, boasts impressive functionality and is highly favored by American authorities. In no small part because these cunning traders initially targeted the American market, so they did not work on US citizens and, unlike NSO Group, were not noticed in hacking their officials. The strategy paid off: the deal amount could reach almost a billion dollars.
Meanwhile, the States continue the long-standing tradition of investing in promising spy software, as was the case with NSO itself and the Italian Hacking Team back in 2014. Business acumen, what can I say.
Everyone exit the Matrix, as well as with Rydox and Anom
Last month, Europol took down another secure communication platform for criminals: this time it was Matrix. Invite-only, with quality encryption. But, apparently, not good enough. Servers intercepted, three suspects detained, including the alleged owner, a citizen of Lithuania.
Details are not disclosed, but they claim to have access to correspondence. And this is 2.3 million messages in 33 languages from ~8 thousand clients worldwide. The EncroChat interception in 2020 led to the arrest of nearly seven thousand people and the seizure of ~800 million dollars. So the groundwork for arrests is good. And with the recent Ghost interception, the secure communications market has thinned out considerably and will finally crumble into local services.
Meanwhile, the Matrix placeholder was designed in the appropriate style, but without thematic jokes. This, of course, is an oversight of the intern: a whole platform for drug trafficking fell, and not a single jab about red pills and Europol screwing everyone in the placeholder.
In December, another long-lived cybercriminal marketplace fell under the FBI's knife. This time it was Rydox. Three admins, citizens of Kosovo, were arrested; two are awaiting extradition to the US, and one will be tried in Albania as an additional punishment. However, there are, of course, possible variations.
Rydox had been active since February 2016, had 18,000 users, and according to documents, brought the admins a modest $230,000 from the sale of stolen access data and various cybercriminal gadgets. However, it seems that this is just the amount seized in crypto. As is customary among Albanians, crime is a family affair. So, comrades Ardit and Jetmir Kutleshi are awaiting extradition. Based on the totality of the charges, both risk enhancing their reputation in criminal circles for up to 37 years, but in reality, they will likely get something around ten years.
Recently, details of the FBI's Anom operation surfaced, and the process against the distributors is still ongoing. And it has taken an interesting turn: the defense demands to reveal the informant's name. He is the creator of Anom, who handed over control of the platform to the security officers, who organized an exciting startup based on it.
At the same time, the prosecution is obliged to reveal his identity if the case goes to court. So, at the behest of Alexander Dmitrienko's lawyers and other federal service personnel, the key figure in the FBI's favorite operation in its recent history risks being exposed. To the cartels and other wonderful people who want to thank him for the impressive honeypot.
So, the privacy issue for comrade Afgoo essentially becomes a matter of life and death. It is clear that he will be hidden away under the witness protection program. But the bad taste will certainly remain.


















Write comment