- Security
- A
Frontend Risks #1: Bitrix CMS sends your clients' data to Ireland
As a result of my security research of 3,000 Russian frontend applications, it was discovered that Bitrix CMS has been transmitting website visitors' personal data to Ireland for more than 11 years. Companies risk fines from Roskomnadzor for cross-border data transfer without notifying the regulator.
Hello everyone! My name is Mikhail Parfenov, and I am an Application Security architect at DPA Analytics. In May 2025, I conducted a security research on Russian frontend applications. Over 3000 of the largest commercial Russian companies' applications were analyzed.
The main pages (corporate websites, portals, personal accounts, social networks, marketplaces, etc.) were opened in a frontend sandbox, which tracked the components and actions of the frontend application (primarily the behavior of the JavaScript code). Within one minute, user actions (scrolling, mouse movement) were simulated on the page. The analysis did not impact or load the applications and was based on publicly available information.
What was analyzed?
What scripts make up the application?
Do the scripts load from third-party hosts?
Where do the network requests go (hosts/countries)?
Which browser APIs (WebAPI) does the JavaScript code call?
Is Content Security Policy (CSP) used in the application?
How effective is the CSP configuration, and much more.
Research Results
A brief summary of the research results was presented in my report at PHDays 2025, and the full results will be published in my telegram channel @FrontSecOps at the end of June.
Interpreting the results of this study is not straightforward, especially from different perspectives (AppSec / IS / Dev), and will be discussed in a separate article. Here are a few key metrics.
64% of applications load scripts from hosts outside of Russia.
71% of applications send network requests to foreign hosts.
This is quite a lot given the political situation, the requirements of Roskomnadzor, import substitution, potential blocking of foreign IP addresses, and other factors. I decided to analyze which foreign hosts occur most often. In addition to the predictable hosts such as www.google-analytics.com, fonts.gstatic.com, cdnjs.cloudflare.com, the following host was also at the top.
Host | bitrix.info |
Subnet | 54.154.0.0/16 |
Country | Ireland |
Domain Registrant Organization | Bitrix Inc |
Let's look into this further. Indeed, all frontend applications sending data to this host are built on the CMS 1C-Bitrix. This might be the Bitrix Web Analytics module (https://www.1c-bitrix.ru/products/cms/modules/web-analytics/), but according to the documentation, this module works locally and does not load a script from an external host.
How does Bitrix Analytics work?
The code of the web pages contains an inline script, which, when executed, loads an external script into the user's browser from the address: https://bitrix.info/ba.js.
Here is the translated text in English while preserving the HTML tags:This script collects data about user behavior, web page fragments (such as headings), and other data typical of web analytics systems, and sends it to the endpoint: https://bitrix.info/bx_stat.
Are the data collected by web analytics systems considered personal?
The debate over what constitutes personal data (PD) and what does not will continue indefinitely. Questions regularly arise, such as whether PD only includes full name, or name + phone, or just email... I suggest following the actions of the regulator here.
In March 2025, Roskomnadzor sent requirements to Russian commercial companies to remove the Google Analytics script from their websites because "the use of the Google Analytics metric program may indicate the collection of PD using databases located outside of Russia," and also because since 2023, cross-border transfer of PD without notifying Roskomnadzor is prohibited.
Also, some analytics systems abuse access and collect excessive data from pages. For example, placing such scripts in personal accounts/online stores can lead to the transmission of PD of all visitors to third-party servers in plain view (if displayed on the page).
According to GDPR, online identifiers and user behavior data are considered personal.
Therefore, in my opinion, the data collected by any analytics system should be considered personal. Consequently, the Bitrix CMS sends personal data of our users/clients to Ireland.
I would also note that the likelihood of Roskomnadzor conducting control measures (including inspections) is influenced by:
Collection of PD using databases located outside Russia.
Collection of PD using foreign programs and services.
Cross-border transfer of PD to foreign countries.
I think the last thing Russian companies expect after implementing a Russian CMS is receiving a fine for cross-border transfer of PD without user consent and notification to Roskomnadzor, especially with the increase in fines for PD violations starting May 30, 2025.
How many companies are at risk?
According to a study, the Bitrix Analytics script was found in 21% of web applications, which includes more than 650 of the largest Russian companies. Below is the distribution by various industries.
Testing on the stand
In my opinion, an important question is whether companies are aware of the presence of an external analytics system in the CMS? Perhaps this option was consciously enabled, in which case the situation is not as critical.
For testing, a virtual machine of 1C-Bitrix was downloaded from the official website, and the latest version of 1C-Bitrix: Website Management (version 25.100.400) was installed with various license options.
In the "Business" license, there is a Web Analytics section in the admin panel, but it relates to other features not connected to the https://bitrix.info/ba.js script. There are also no other options in the admin interface that allow you to disable the embedding of this script on pages.
After creating a test site, the presence of the script on the pages was checked. The results are shown in the table below.
License type | Start | Standard | Small Business | Business |
Are there Web Analytics module settings in the admin panel? | No | No | No | Yes |
Do the Web Analytics module settings allow disabling the embedding of the https://bitrix.info/ba.js script? | No | No | No | No |
Are there other options in the admin panel that allow disabling the script embedding? | No | No | No | No |
Is the https://bitrix.info/ba.js script embedded by default? | Yes | Yes | Yes | Yes |
The CMS documentation does not mention the embedding of this external analytics script, which is hosted in Ireland. The script is embedded by default in all editions of 1C-Bitrix: Site Management (remember the Secure/Privacy by Default principle).
Thus, we can conclude that companies using the CMS might not be aware of this behavior unless they use specialized solutions to analyze the security of frontend applications.
How to disable it?
Two articles from 2017 were found online (first and second), showing how to disable the embedding of this analytics script.
You need to add the following object to the array of parameters in /home/bitrix/www/bitrix/.settings.php.
'analytics_counter' => array(
'value' => array(
'enabled' => false,
),
),I checked. It really works. The script stops being added to the pages. Is this option obvious and is it described in the official documentation? No.
Conclusion
From the perspective of information security, this behavior of the application (in this case, the CMS) is considered "undeclared capabilities" (UDC).
Considering that cross-border transfer of personal data without notifying Roskomnadzor is prohibited, and companies unaware of such behavior of the CMS do not indicate cross-border transfer of personal data in their data processing policies/consent for data processing on websites, this functionality of the CMS increases the risk of inspections by regulators and the possibility of fines/financial damage to companies.
I recommend that all companies using 1C-Bitrix: Site Management disable the use of this analytics script as soon as possible following the instructions mentioned above.
Software vendors must analyze the behavior of their frontend applications to avoid putting their clients/customers at risk (leaks in frontend applications are not detected by WAF, NGFW, or other protection tools, as they occur in the "blind" zone - directly in the user's browser).
Information security/AppSec specialists should analyze the behavior of frontend applications to detect such and other malicious script behaviors and react promptly to reduce the risks of data leaks and attacks on users.
Update 18.06.2025
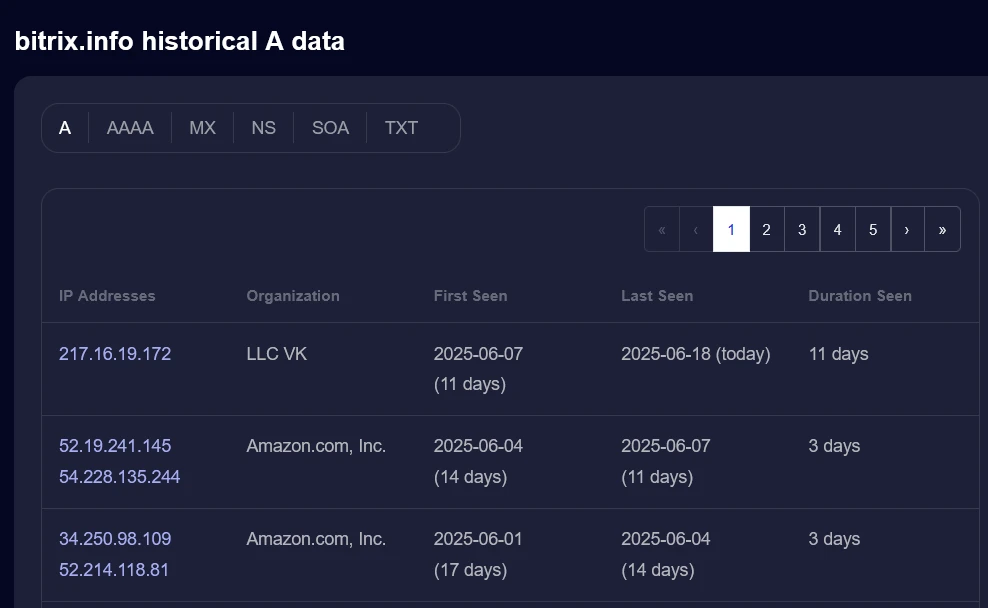
A few days ago (around 07.06.2025), the service was moved to the territory of the Russian Federation. Currently, the script at https://bitrix.info/ba.js returns an empty script, meaning data collection is not taking place, but the script is still being injected by the CMS core.
Thanks to the colleagues at Bitrix for their prompt response to this research. It would also be correct to disable the default injection of the analytics script.
I recommend that companies using CMS disable the script injection in any case, as the external script may be changed at any time.
P.S.
Judging by posts from 2017 on the forum about methods of disabling the described script and services displaying the history of DNS record changes, the Bitrix Analytics backend was hosted in Ireland since 2014. User data has been sent outside of Russia for over 11 years.
In most incidents involving frontend applications, the time the malicious code is present is measured in years/months/weeks. Classic protection tools (WAF, NGFW) and application security analyzers (SAST, DAST, SCA/OSA) do not detect data leaks on the client side. Even with a secure backend, data can leak directly into the user's browser for years if the behavior of frontend applications is not regularly analyzed.
I run a Telegram channel called FrontSecOps on frontend application security: https://t.me/FrontSecOps. Anyone interested in behavioral analysis of applications, leak detection tools in browsers, and script behavior analysis is welcome!




Write comment