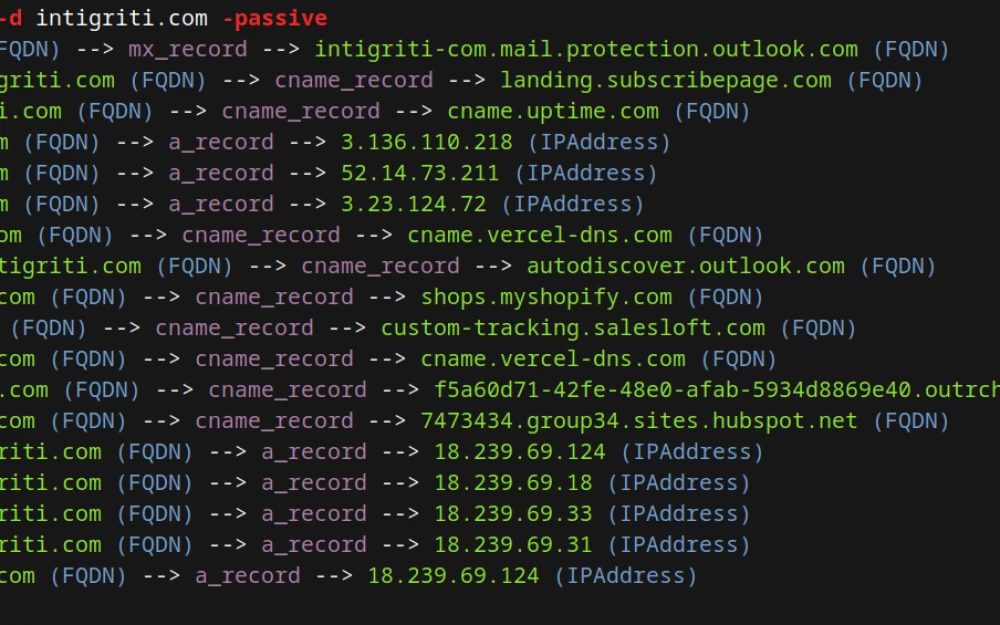
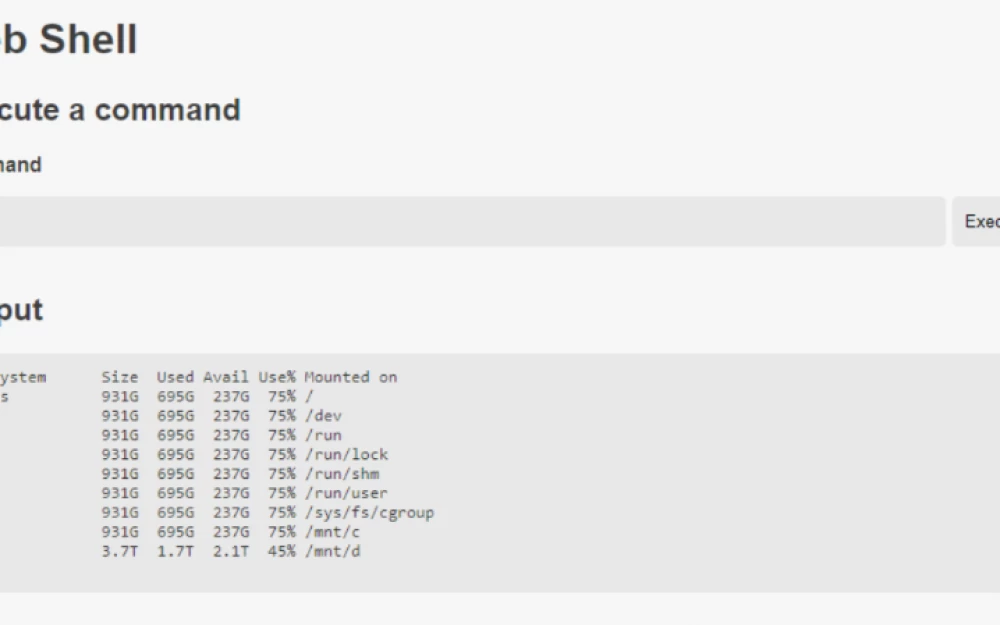
According to the tag web, the following results have been found:
Julia here again, a systems analyst at EvApps, and we continue exploring WebSocket technology. In the first part, we learned the basics of WebSocket, and now let's look under the hood of a real website, for example, a crypto exchange. Let's try to understand how this sophisticated mechanism works: what happens when you see instantly changing quotes and charts, and what goes on “behind the scenes”.
Agents are super buggy. In our company projects, we noticed that Langchain started to perform worse. In multi-agent systems, agents often loop because they don’t understand when they have completed the final action, don’t call each other when needed, or simply return data in broken JSON format. In short, creating an agent system has become more difficult, and we even started considering simplifying systems by getting rid of a lot of agents. And just a week ago, OpenAI updated the SDK for creating agents and also rolled out access to new tools via API. So I went ahead and started testing.
Hello everyone! Recently, I have noticed many posts and articles in the Russian-speaking segment of the internet that refer to an interesting study but interpret it... let's say, quite peculiarly. It is often possible to see headlines like "AI learned to deceive to escape!" or "Neural networks got out of control and tried to escape!". This fundamentally misrepresents the meaning of the study.
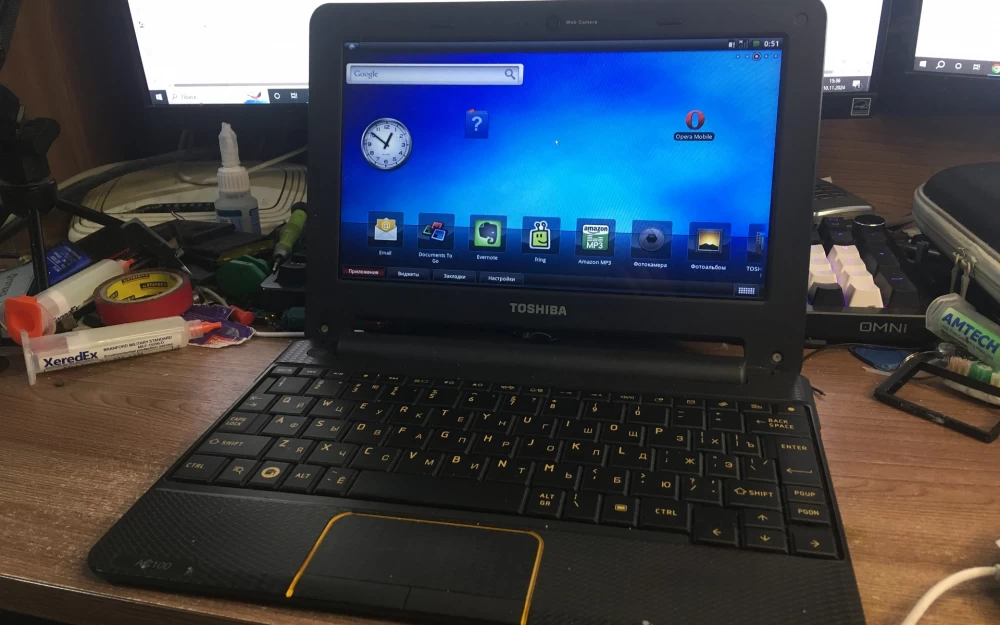
My long-time readers surely know how much I love unusual netbooks with exotic processors and unusual operating systems on board. One of these devices is on my desk today: the Toshiba AC-100, which was released as a netbook for internet surfing for $200 back in 2011 and was notable for running on an extremely exotic platform - the ARM chipset NVidia Tegra 2 coupled with a desktop multicontroller and Android as the OS. But here's the trouble: the device's display backlight was not working. In today's article, we will: learn the history of netbooks and how the AC-100 appeared, repair the cable with improvised means, and take a look at this wonderful beauty in practice. Interested? Then see you under the cut!
Frameworks simplify development, eliminate chaos, and set clear boundaries when creating an application.
In my previous article, I mentioned the implementation of a device that was developed to facilitate the process of setting up sensors by the maintenance staff, and the attached survey showed that you are interested in the topic of implementing this device.
Continuing the story about vulnerabilities discovered by UCSB pentesters and formed the basis of cases at the Pentest Award, we publish an analysis of the following real example.
Modern hardware is incredibly fast. The M1 Max, on which I am writing this article, runs at 3.2 GHz. That is 3.2 BILLION cycles per second. However, Microsoft Teams takes 3 seconds to open a link, and I refuse to believe that it takes 9.6 BILLION cycles to open a link. Obviously, I am simplifying, but the point remains the same: how is it that hardware gets faster, but applications only get slower?
When a user enters a website URL in the browser's search bar, their computer or other device initiates a connection with the server and sends it an HTTP request — a message with some information. This could be a request to send an HTML page or, conversely, user data that the server needs to process. Essentially, the browser provides the user with a graphical interface for obtaining information from websites using HTTP.
Do you like canned food? Or Viagra? You can buy them from us!
Caching is an efficient architectural solution that is used at all levels of computing systems today, from processor and hard disk cache to web server cache and reverse proxy servers. It is the latter that will be discussed.
The WebSocket protocol allows for the establishment of a permanent two-way connection between the client and the server, which significantly reduces latency and decreases the amount of data transmitted compared to traditional HTTP requests.
Disclaimer: the words used like "port", "hack" and "reverse" do not mean that the article is intended exclusively for geeks! I try to write so that it is understandable and interesting to absolutely everyone!
BI.ZONE WAF Cyber Threat Analytics and Research Department studied the statistics of attacks on web applications protected by BI.ZONE WAF. We compared this information with the results of the analysis of shadow resources that our specialists have been monitoring since 2011. In this article, we will tell you how the methods of attackers have evolved.
As the idea of the industrial metaverse materializes in corporate tools, spatial technologies find applications in industry, leveraging data and artificial intelligence to model physical processes.
The world of vulnerabilities is quite diverse. Usually, hackers try to achieve their goals using arbitrary code execution vulnerabilities, the very abbreviation RCE. But in practice, often to execute their code, it is first necessary to write to the desired file. And here another type of vulnerability comes to our aid - Arbitrary File Write. These are arbitrary file write vulnerabilities. They can become a powerful tool in the hands of an attacker, for example, when attacking a website or escalating privileges in an OS. Also, AFW can be used in the implementation of remote code execution attacks.
Anastasia Vazhinskaya is an information security engineer, not a front-end developer, but her presentation became the most important for the main hall of the FrontendConf 2024 conference. Why is that and how is front-end development and the conference program changing? What drives the speakers this year? And what pains are they suffering from? Let's talk to the speaker and find out everything firsthand.