- Security
- A
UserGate 7: test results + migration from old versions
In this article, I will talk about a relevant issue for many — migration from UserGate 6 to version 7. After the departure of foreign developers from the Russian market, UserGate solutions have proven to be an effective alternative to foreign products, solving many import substitution problems. The latest version of UserGate software has been significantly improved and has become an even more serious tool in the fight against information security threats. Under the cut, I have collected everything about the advantages of UserGate v.7 with instructions on how to migrate to it from the previous version.
Hello everyone! My name is Vlad Permyakov, I have been in information security for more than 15 years and I hold the position of senior systems engineer at K2 Cybersecurity. Our company is an integrator and consultant for information security solutions, so we actively test the products available on the market and use the best of them both in our own work and in client projects.
About the capabilities of UserGate 7
Probably everyone who decided to read the article is aware, but just in case, I will leave here a description of UserGate as defined by the vendor itself.
UserGate combines a next-generation firewall, routing, gateway antivirus, intrusion detection and prevention system (IDS), VPN server, content filtering system, monitoring and statistics module, and many other functions. The product allows you to manage the company's network, optimize its traffic, and effectively prevent internet threats.
The seventh version of UserGate was released last year. Currently, v.7.2 is available. It has been significantly improved and is aimed at working in high-load network services. One of the main features is more flexible infrastructure management, which means greater control over traffic in your network.
After a year of testing, I can highlight the following main advantages:
extended functionality for diagnostics and monitoring of both incoming and outgoing traffic;
sending decrypted traffic to external servers and checking decrypted SSL traffic using SOC/IDPS;
integration with domain directories using UserID;
a new UserGate Policy Language tool that makes it easier to write security rules, allowing you to manually create very precise and comprehensive rules;
functional CLI, which provides both monitoring tools and the ability to configure the firewall — from creating bond interfaces and routing to setting up VPN and building a cluster;
an updated (but not significantly yet) web interface.
We are waiting for the refinement/release of the following features:
UserGate Client — a new solution that will combine VPN, NAC, and EDR.
A new WAF that should expand the functionality of UserGate NGFW.
UserGate SIEM with extended IRP and SOAR functionality.
Fixing web interface errors when installing a large number of VLANs. If you create more than 30 VLANs in UG, the web console interface gives an error, and the cluster stops successfully switching the master role.
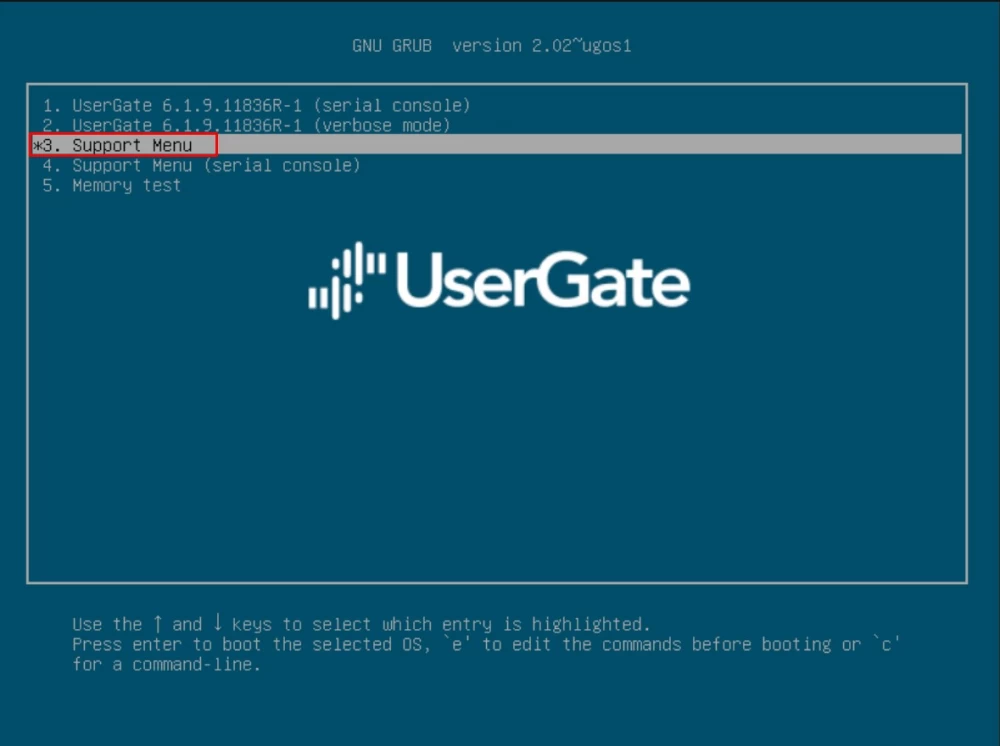
Switching to Usergate 7.2 — instructions
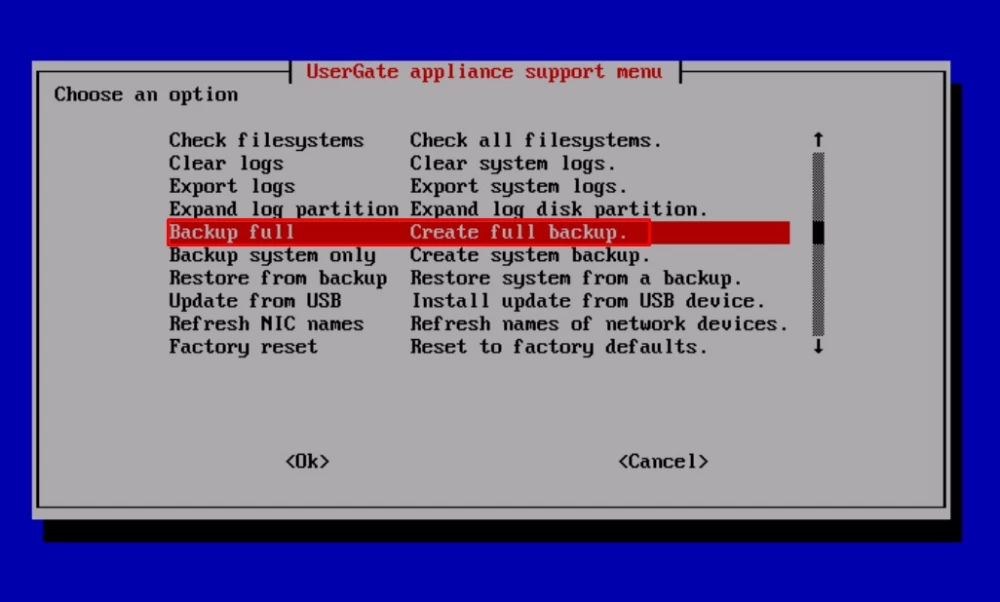
Step 1. Backup
Export the configuration of your old v.6.x.x using the standard tools in the current version. In the Device Management section, click on the link Export settings-->Export. The system will save the current server settings under the name database.bin.
I also recommend making a full backup of the PAC hard drive. If you are not satisfied with something after the update, you can always restore to the backup point.
You will need an external hard drive or flash drive with a capacity comparable to the PAC HDD.
If you have a cluster, first turn off the passive node, back it up, and then turn off the master node and back it up.
Step 2. Installing the new version
We are installing the image. This takes an average of 1 hour, depending on the equipment model. Detailed instructions are available on the vendor's website.
After the update, new keys from version 7 will be needed, version 6 keys will not work.
Step 3. Import old configurations
Activate and upload the configs from the old version 6. In the Device Management section, click on the link Export settings-->Import and specify the path to the previously created settings file. The specified settings will be applied to the server, after which the server will be restarted.
Pitfalls — L7 and SOV rules may be transferred incorrectly or not transferred at all. They will need to be recreated manually.
According to the developer, when importing old configurations to version 7.1.x, firewall rules containing L7 will be forcibly disabled. They will be set to action = accept and a created L7 profile will be added. Filters for each application group will be added to the profiles according to the following rules:
for the "All" group — the "Any signatures" filter;
for category groups — a filter like "category = name or category number";
for custom groups — a filter including signature identifiers, like "id IN (...)".
SOV profiles will be converted to the new format upon import. They will have one filter like "id IN (...)", which will include all SOV signature identifiers from the old version SOV profile.
SOV rules will not be able to be imported. The user will need to reconfigure IDPS after completing the import operation, using the new SOV profiles and firewall rules.
After importing SOV signatures and applications, you will need to start their update.
As shown by experience, it is necessary to maintain a pause of 20 seconds between operations. For example, you created a script for 1 VLAN, wait 20 seconds and create the next one.
Conclusion
NGFW UserGate is currently one of the few products on the Russian market that really competes with foreign ones and solves many import substitution issues. The main advantage that my team and I see is the development of a full-fledged UG SUMMA ecosystem, which includes: NGFW, DCFW, ICS, EDR, WAF, MC, and SIEM.
The transition to UserGate 7 is not a complicated process. However, if you have many security policies, it will not be possible to transfer them to the new OS without any problems. It will definitely require some "manual" work by an information security specialist.







Write comment