- Security
- A
My first Standoff, or How I looked over the shoulder of a cyber attack investigator
Hello everyone! My name is Sasha Korobko, I have been working at Positive Technologies for more than a year and I am already actively involved in the processes of various products and services. In this article, I will tell you about one of my days at the Positive Hack Days cyber festival last year. More precisely, about a very important part of it — the Standoff 13 cyber battle. The fact is that in 14 years of working in IT, I have never made it to the famous PHDays. Of course, I heard, absorbed the enthusiastic stories of colleagues who participated. It was fun to watch this: you haven't been there yet, but you want to get there. And I'm not so much about the festival itself, but about meetings, networking, provocative jokes, new features: how someone was hacked, what trends, who learned how to use new tools... And in May 2024, I was lucky to get to Positive Hack Days for the first time, to be in the thick of the cyber battle, namely: on the side of one of the defense teams. But first things first.
Hello everyone! My name is Sasha Korobko, I have been working at Positive Technologies for more than a year and I am already actively involved in the processes of various products and services: with the guys from the MaxPatrol EDR team, as they say, we have our sleeves rolled up equally.
In December, the announcements of the new Positive Hacks Days were released, and while you are thinking about the expert reports and tracks that interest you as listeners or speakers, I will tell you about one of my days at the cyber festival last year. More precisely, about a very important part of it — the cyber battle Standoff 13.
In May 2024, I was lucky enough to attend the cyber festival Positive Hacks Days for the first time. Yes, it may not be new to you, many have been there as partners, cool researchers, inquisitive minds, representatives of renowned vendors, etc. And in my 14 years of working in IT, I have never attended it. Of course, I heard, absorbed the enthusiastic stories of colleagues who participated. It was fun to watch this: you haven't been there yet, but you want to get there. And I'm talking about meetings, networking, provocative jokes, new features, how someone was hacked, what trends, who learned how to use new tools...
Positive Hacks Days in 2024 turned out to be really cool. Several days, sunny weather, large space, freedom. I didn't get to see the opening, but I don't regret it, because I initially had a different task at PHDays. I looked around the entire venue the day before May 23 — the official start of the festival. Not because I was part of the organizers, but because on the 22nd the Standoff 13 cyber battle began.
It was important for me, and thanks to the project team for this opportunity, to be in the thick of things on the defenders' side. I know, earlier we had already given our various products to the blue teams, including they could respond to attacks. And now, for the second time, the defenders fully utilized the capabilities of Positive Technologies solutions. I was wildly interested in what the "blue" teams would do with all this, how they would start repelling attacks and, no less importantly, how understandable and convenient our MaxPatrol EDR would be for these people.
What is the Standoff 13 cyber battle
Cyberbattle Standoff 13 is a competition in which cybersecurity specialists tested the cyber resilience of companies from various sectors of the economy of virtual states over four days (from May 22 to 25).
The competitions included critical events — consequences for the virtual infrastructure, for the implementation of which hackers received the most points. For a virtual city, for example, this could be triggering a fire alarm, stopping air conditioning systems. For production — stopping automated process control systems (APCS), disrupting the production cycle, decommissioning turbines, and much more.
During the cyberbattle, 25 attacking teams ("red" in Standoff language):
competed for a total prize fund of 15 million rubles;
attacked two virtual states with their infrastructures and industries;
looked for weak points in defense, practiced trending attack techniques.
And 11 defending teams ("blue"):
repelled attacks on their industries;
checked which attacks they were prepared for;
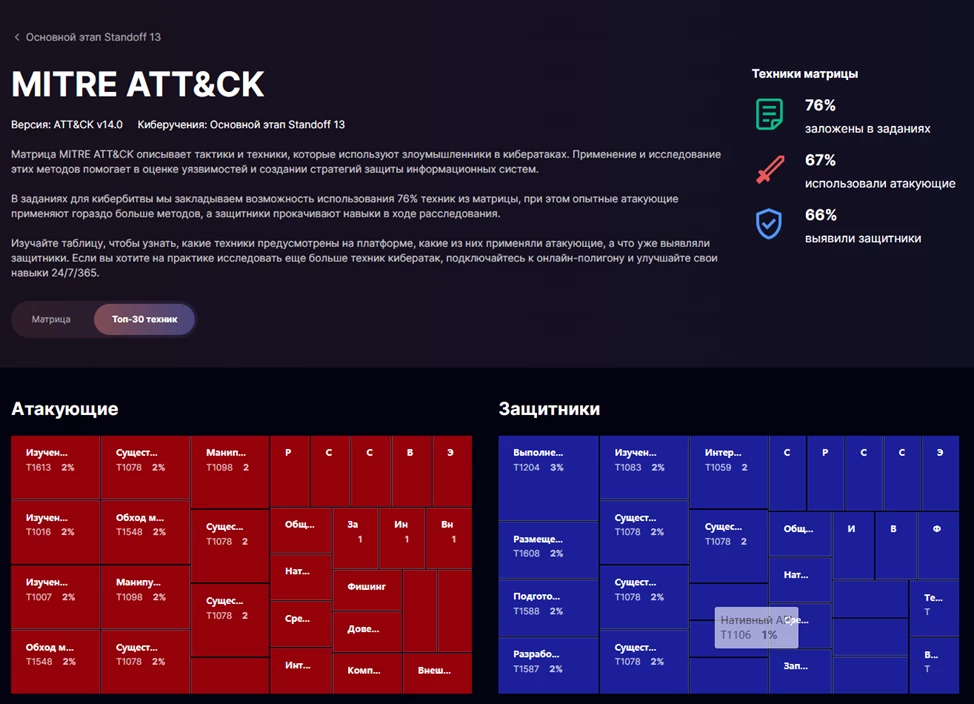
I will not boast about the results of these teams, the guys from Standoff specifically did not make defender ratings. You can find out how it all went and decide how important or useful it is by the tournament tables and by the coverage of the MITRE ATT&CK matrix. I invite you to participate in the next Standoff cyberbattle yourself!
Two teams
These are experienced specialists who have already encountered white hackers in competitions and even in cyber ranges. In the virtual environment, they essentially built their own SOC, created cybersecurity processes (event handling, data collection for investigation, incident report generation), and formed incident tables: some had their own IRP (Incident Response Platform, software for incident handling), some had an operational messenger and headsets for work, and some had guys from the pentest team. And I was allowed to be with one of them! It was a team of over 20 people who protected the nuclear industry. They had their own division of specialists into roles (pentest, analytics, monitoring, threat hunting, response).
Standoff 13 took place at the small sports arena of Luzhniki. The scale of the cyber range construction was colossal, behind the scenes there was an interesting symbiosis of Soviet construction and our modern structures: black drapery fabric, kilometers of wires, neon light, and other cyber visuals.
The pavilion was already filled with the atmosphere of a virtual battle: everything was working, the "red" stands were opposite the "blue" ones, the polygons of the attacked infrastructures were erected, some spotlights were everywhere... and silence. Only the barely perceptible hum of negotiations in each of the teams (and there were many of them). They were already working in their space, even before the festival opened. At that moment, there were no spectators, no host, no speakers on stage, no announcements of results. That's why I remembered this silence, the working screwdrivers, and the periodic sound check.
I roughly understood where my place was in this room, I needed to find the team and sit on any free chair. Nothing complicated when all the scaffolding is removed and you can see where the stairs are located. So: I'm in place, in the "blue" stands in a team of 20+ people. They found me a workplace with a monitor and a chair. All the team members I had the chance to mentor (I accompanied the guys and answered questions about the product they had: the team had no previous experience with MaxPatrol EDR) were divided into groups: monitoring with MaxPatrol SIEM, incident registration, response with MaxPatrol EDR, working with PT NAD network traffic, proactive threat hunting, and checking hypotheses on the attackers' next steps. I didn't have access to the guys' infrastructure, so I just decided to take out my work laptop, record the team's feedback on working with the product, and note any questions or problems that arose.
The day was going to be long: narrow space, many people, four more ahead. I brewed my favorite pu-erh tea in a thermos and slowly enjoyed it. It's a pity that the first thing I did was spill this thermos on my laptop and the neighbors' table. Such a "team integration." Fortunately, everything turned out fine: nothing short-circuited, the equipment remained intact. And I noticed that the guys brought their battle machines covered with stickers. I felt uneasy about what had happened and could only hope that the 700 grams of jerky I make myself and politely distribute would allow me to stay in their ranks. And so it happened.
The first hours passed, people were getting used to the infrastructure, synchronizing on reports and working with the jury. Already after 4 hours of cyber battles, the first incidents began to appear. Team members entered them into a common table, which they worked with (not immediately, but they gave me access to it), supplemented with data from monitoring systems, and suggested response options to prevent hackers from advancing.
Almost immediately, I began to hear behind me "Dima, let's block... so, we block the host...". This was addressed to a team member who was responsible for MaxPatrol EDR. He knew which incidents were in progress and what the hackers were doing, and together with the team, he made decisions on when to stop the attackers' activities. We quickly found a common language with him, as he was genuinely interested in the product and had not worked with it before the cyber battle. Surprisingly, without experience, without reading the documentation, he immediately began to apply it. My respect to the mentors: they prepare the participants for the infrastructure, tell them what is on the online ranges and which of our tools will be used.
Dmitry and the team went through a whole stream of attacks in four days, applying many response techniques. I only had to answer questions in a timely manner and show the interface. Naturally, we found a couple of suboptimal cases, bugs, but overall the team appreciated how powerful and effective the tool was in their hands, and felt confident in countering the hackers.
The mechanics of the cyber battle did not involve automation of response, and some restrictions could not be imposed permanently, as this was prohibited by the competition rules. This is a serious cheat, and using them in any game is unfair, don't you agree? That is, if the defenders simply isolated key nodes from the network, they would, of course, cut off the attackers, preventing them from carrying out critical events (in other words, conducting attacks). But this would significantly reduce the availability percentages of the infrastructure (a parameter that affects the team's performance). Therefore, they closely monitored to somehow respond, and after 15 minutes rolled back the restrictions. According to the competition rules, a timer was introduced - the response, during which something is isolated (computer, account, network), is limited to fifteen minutes.
No defender team at Standoff 13, working in response mode, aimed to completely block any possible access to the infrastructure - they always allowed the attackers to advance in their attacks. The goals of the "blue" teams are to study techniques, investigate incidents, and not just block. A very conscious approach that allows you to improve skills for real work in your SOC.
The response teams were able to achieve good results:
protected the sectors of "Energy" and "Nuclear Industry", represented in the infrastructure of our virtual State S;
prevented a total of 117 incidents, investigated 23 critical events;
achieved minimal response times to incidents - 24 minutes;
worked like real SOCs: with role separation, analyst lines, with the incident processing process (initiation, enrichment, response, report);
in 20% of initiated incidents used MaxPatrol EDR for response (the teams had more than 800 such incidents in total).
The attacks included the following malware families:
Cobalt Strike;
Metasploit;
Impacket;
Hot Potato;
LaZagne.
It was completely unusual for me, but pleasant to watch as the guys sent more and more requests to my new acquaintance Dima. And all with phrases like "So, they are scanning the network from the host, we block it... there is activity from the Hubbard account, we need to block it... we checked the file, this needs to be deleted everywhere and the processes stopped".
Some response options caused difficulties for the guys: they pressed these buttons in the product console for the first time. But it must be said that in the end, the tasks were solved. Then they said that in general, it is easy to start working without documentation, not everything is intuitively clear, but most of it works "on the fly".
What response techniques the defenders were able to use:
blocking traffic by specific IP address (this helped to identify cases when attackers scanned the network from some compromised nodes and connected to C2 servers);
partial network isolation (it helped a lot when it was necessary to prevent advancement, deal with the node, study the activity on it more thoroughly);
checking files in the sandbox and by hash sums - deleting files (print.exe, d.exe, wmihost.exe, juicypotato.exe, nmap.exe and other variants of popular exploit names);
stopping processes (generally important for stopping PowerShell);
blocking accounts (one of the new modules at that time, with which it was possible to isolate local accounts on devices to stop privilege escalation attempts).
As a result of the cyber battle, the Standoff team also had a completely extensive version of the MITRE ATT&CK matrix. It showed which techniques the attackers actually used and which of them our products saw and stopped over these four days.
These attacks are relevant to real-world conditions, all techniques and tactics are used by "wild" attackers.
Almost 70% of the techniques from MITRE ATT&CK that we included in the tasks were found and used by the "red" team.
In real infrastructures, solutions are needed that can protect not against specific malware files, but against TTPs. Products are needed that can detect the attacker's chain of actions as early as possible.
MaxPatrol EDR covers attacks relevant to endpoints, and we are constantly expanding the expertise in the product.
In addition to the conclusions from the cyber battle itself, in which the leaders showed themselves, my colleagues worked out complex scenarios, brought the online range and competitions to the international level, and I was lucky to gather a lot of feedback for product development.
We have six user interviews, four days of intense immersion, feedback from participants, telemetry, metrics that we can carefully study to improve detection and response quality.
Ideas for changing or updating the interface to give the user an understanding of how the system performed the desired action (for example, the file has already been deleted, renamed, moved, but cannot be deleted; or when it is not obvious to the user what capabilities are available for Linux or Windows devices).
Suggestions for developing capabilities on Linux (this includes node isolation; but we have already added remote shell 😊).
Suggestions for the scenario of deleting files by hash sums. This is one of the new modules, and we still have to add new scenarios for users.
What's next?
First of all, we in R&D are very pleased that our MaxPatrol EDR continues to be actively used in battle - at "loaded" events.
We are preparing for such events, trying to provide clients with the most effective and up-to-date tools. This was the case with MaxPatrol EDR 6.0, a release that we tried to present on time, especially for the Standoff 13 cyber battle. And it worked. A lot was done behind the scenes: restructuring processes, improving quality, fulfilling agreements, forming a transparent picture of product development for clients.
We definitely use the acquired knowledge and raw data from online ranges. For what? For testing, analyzing techniques, and adding the most appropriate expertise to the product.
While I was writing the article, the new cyber battle Standoff 14 took place. It was held completely online, but it did not become any less exciting and dramatic: with the new version of the product, taking into account the wishes of our clients and those who used the product for the first time at the 13th cyber battle, with new tricks of the attackers, attempts to bypass MaxPatrol EDR, and, of course, the response to threats by the defender teams. However, that's a completely different story :)
Have you been to the Standoff cyber battle? What did you like and catch the most? Share your memories and experience.








Write comment