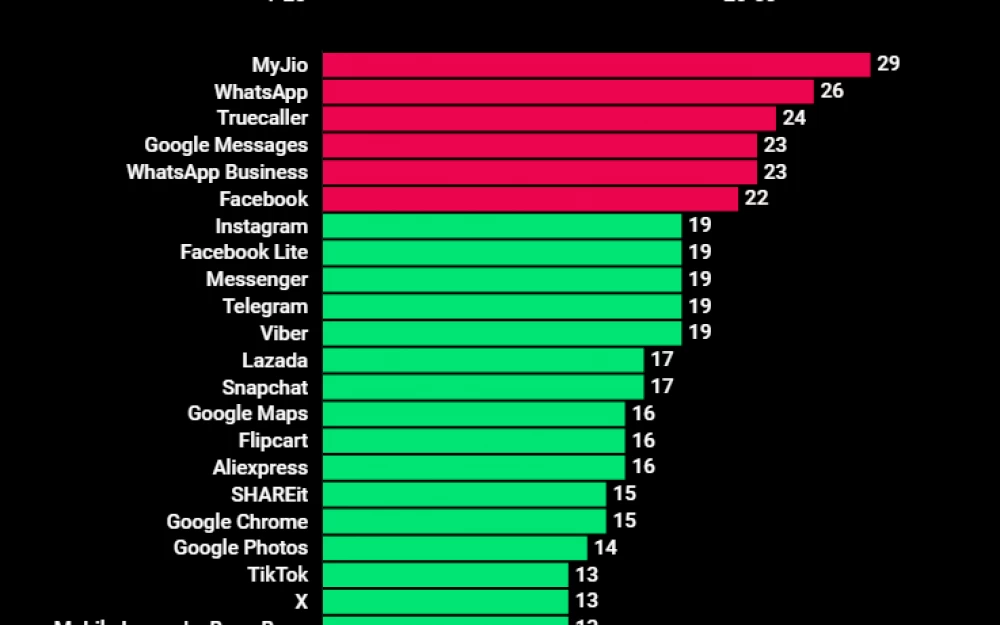
According to the tag NDR, the following results have been found:
What if you could create a mobile app without knowing a single line of Swift? Welcome to the world of vibecoding—the new style of "mood-based" programming, where natural language and LLM replace syntax and compilers.
Once, while traveling through remote Vietnamese villages, I asked a girl to squeeze me a glass of sugarcane juice. To explain, I used Google Translate. From her eyes, I understood that if my request was about sugarcane, it was about the wrong kind. I had to quickly simplify the message by first translating from Russian to English, and then from English to Vietnamese. Essentially performing the same algorithm that Google does when one or both of the languages are not English.
The rapid development of artificial intelligence has led to a surge in job openings in this field, and today many people are building exciting careers in it. For many years, American scientist Andrew Ng has observed how this happens with thousands of students, as well as engineers in large and small companies. Now he offers a practical scheme by which you can pave your own career track.
Hello tekkix, my name is Stanislav Gribanov, I am the product manager of the NDR group of companies "Garda". I have been working in information security since 2010, and since 2017 I have been developing products for network security, author of the blog "Cybersecurity and product expertise for business". Communicating with colleagues, partners and customers, I see many difficulties in classifying products for network security and understanding the unique value of a particular class of solutions.
In my previous article, I mentioned the implementation of a device that was developed to facilitate the process of setting up sensors by the maintenance staff, and the attached survey showed that you are interested in the topic of implementing this device.
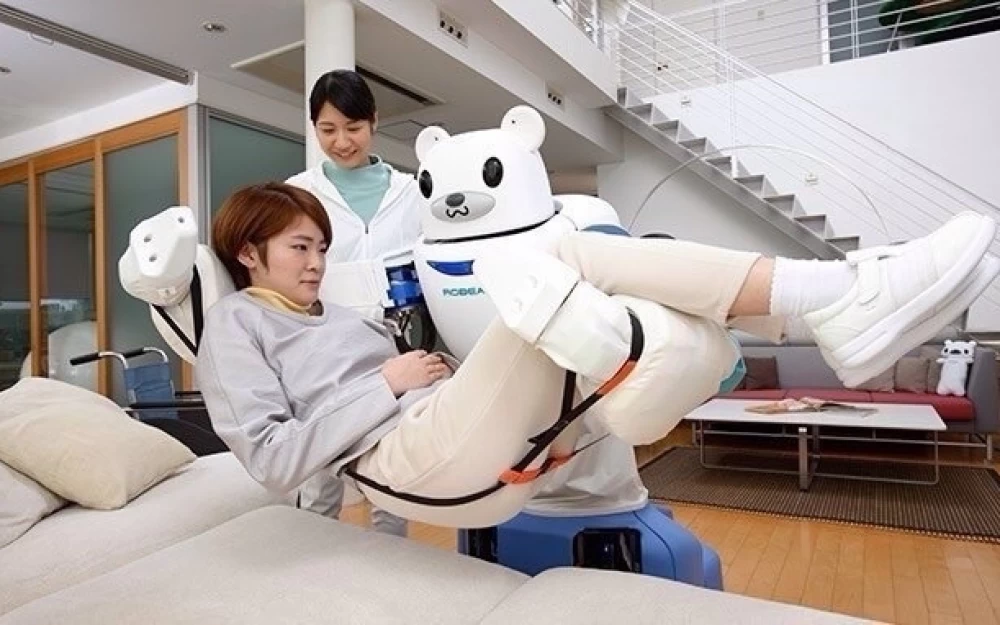
The field of elderly care is a complex and, frankly, unprestigious job that almost no one strives to get into. The idea of introducing helper robots into this area seems sound and logical - especially considering that the most roboticized countries are also the oldest. But can machines replace humans in a craft that requires not only practical skills but also empathy?
Hello, tekkix, my name is Alexey Onosov, I am an author at vAITI media. In this article, I will talk about setting up DLNA on servers, TV and mobile players, and hardware receivers. At first, this may seem like a daunting task, but in practice, it is not. The main thing is to choose the right equipment and software that meets your needs.
Hello tekkix. I will tell you about my experience of building a home theater with multichannel sound on an Android TV box.
It is no secret that bug hunting is gaining popularity every year, attracting the attention of both companies seeking to improve the security of their products and white hackers who want to apply their technical skills and earn money by finding vulnerabilities. More and more companies are creating their own bug bounty programs, some are integrating into existing platforms.
My career in information security began, like many others, with work in IT infrastructure. Initially, my company was engaged in maintaining the stability of networks and systems for various companies, and regularly faced typical problems associated with cyberattacks.
On August 21, the Chrome browser received an update that fixed 37 security-related bugs. The attention of researchers around the world was drawn to the vulnerability CVE-2024-7965, described as an incorrect implementation in V8. In practice, this means the possibility of RCE in the browser renderer, which opens up space for further exploitation. Researchers' interest increased even more when on August 26, Google reported the use of CVE-2024-7965 "in the wild".
Many people have photos of their passport, driver's license, and child's birth certificate on their phone. But not everyone realizes how easy it is to access them. One permission granted to an application can lead to data disclosure. We studied the 50 most popular Android applications and found that most of them want to get an unreasonably large number of permissions. Let's figure it out.
In the article, I will tell a case from the practice of analyzing the protection of Android applications. Names and places of events have been changed. Any coincidences are accidental)