- Security
- A
Social engineering or how the efforts of security professionals are shattered by the human factor
Information security specialists create systems that resist cyberattacks. They implement firewalls, configure monitoring, write security policies, and train employees. This is a powerful defense against external threats. But there is one vulnerability that nullifies all the specialist's efforts — the human.
Social engineering is what keeps security professionals up at night. While they work on protecting the infrastructure, attackers work on bypassing these measures through the human factor. You can't "patch" a human like an operating system. Instead of breaking the code, hackers pick the keys to the mind, using trust, fear, and urgency.
Why social engineering works
More and more attacks are based on deceiving employees rather than breaking the code. Attackers forge emails, create fake websites, imitate calls from "executives" or "support services". And when an employee, seeing an email from the "CEO", gives access or clicks on a phishing link, technical measures are powerless.
The main reason for the success of social engineering is psychological weaknesses. People tend to trust authorities, succumb to urgency or fear. Even the most trained employees can make a mistake at a critical moment. Attackers study the company as thoroughly as the security specialists themselves. They know where the weak points are, who is responsible for access to critical information, and attack precisely there.
How to minimize risks?
As long as people remain online, social engineering attacks will not disappear. The question is whether the company is ready to build protection that takes this factor into account, or will rely on the fact that "well, no one else will make such a mistake." There is no point in protecting the network if people are not protected.
Information security specialists need to understand: the key to protection from social engineering is not only technology, but also competent work with people. In practice, this can be difficult, because you can conduct 10 phishing trainings, and still at a critical moment someone will click on the link. Why? Because emotions work at the moment of the attack: trust, fear, desire to help. Therefore, protection from social engineering attacks involves:
Technical measures against the "human factor". Automation of incoming message checks, content filtering, access control. The less employees need to think, the less chance they will be deceived.
Simple and clear protocols. Minimizing decisions that employees need to make. If in doubt, do not open. Calls from the bank - hang up, call back on the official number. Requested access to files - always check through system administrators or the information security department.
Working with psychology and forming a cybersecurity culture. If you are an information security specialist, your task is to show employees that cybersecurity is not only the work of the information security department but also their personal responsibility. People do not perceive danger until they see it themselves. Launch attack simulations, raise real cases, show the consequences so that it is not just a "scary story" but a reality they may face.
And remember, social engineering is not a question of "if," it is a question of "when." And the right choice is to be prepared for it, so as not to experience the pain of leaks due to human factors.

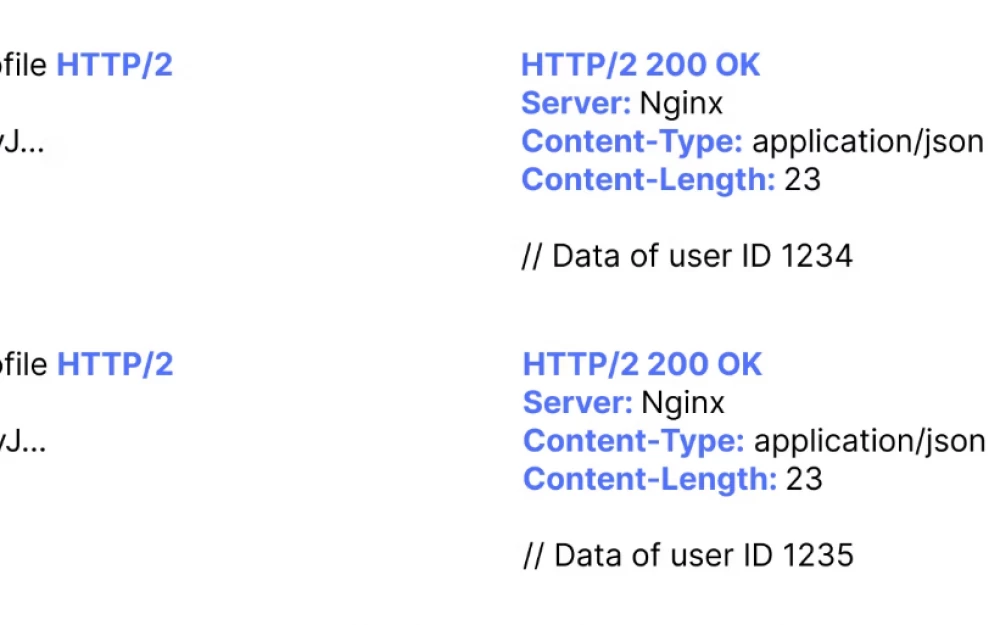





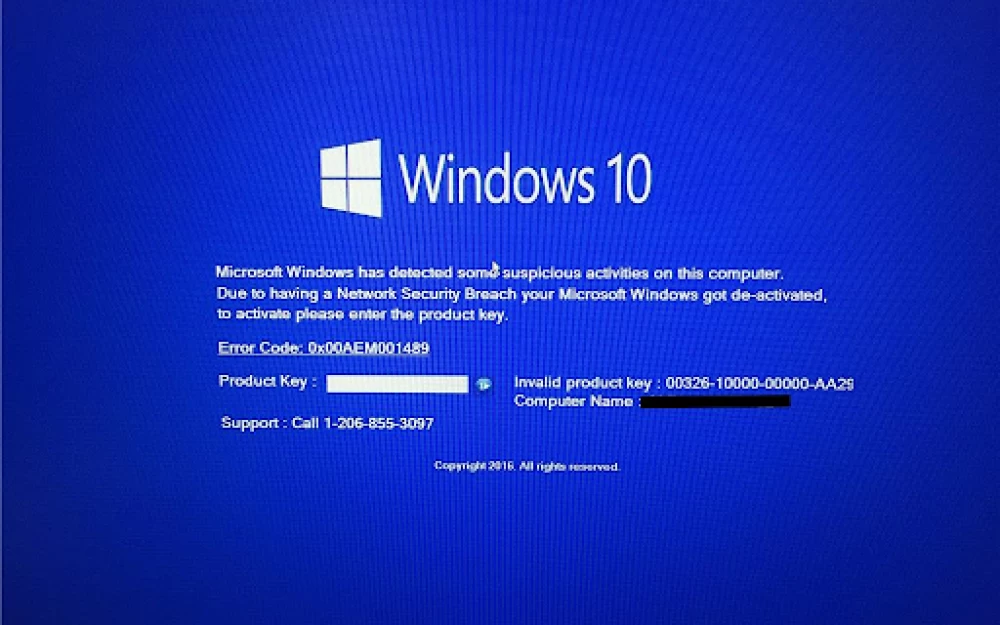
Write comment