- Security
- A
Key to all doors: how a backdoor was found in the most secure* access cards
You apply the key card to the reader, and the office door opens. But what if such a pass can be hacked and copied by anyone?
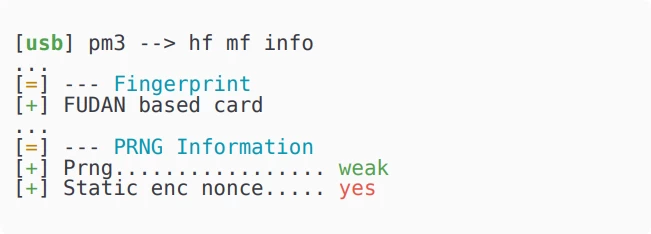
In 2020, Shanghai Fudan Microelectronics released new smart cards FM11RF08S. The manufacturer claimed their complete security against all known hacking methods. A group of researchers tested these claims and found a built-in backdoor that allows full access to the card's data.
In this article, I will tell an exciting story about how this backdoor was found and analyze the catastrophic consequences of its implementation. This case clearly demonstrates the danger of blindly trusting marketing claims about security and the importance of independent auditing of critical systems.
The standard that survived: the phenomenon of MIFARE Classic longevity
MIFARE Classic is a dinosaur in the world of contactless cards that somehow has not yet become extinct. Every day, millions of people around the world attach these cards to readers: they open office doors, pay for subway rides, and get discounts on their favorite coffee.
Alas, this standard turned out to be very unreliable. MIFARE Classic has been hacked so often that it has become a popular sport among hackers. Remember our article about hacking Boston subway tickets? This is just the tip of the iceberg.
And the manufacturers? They took the path of least resistance. Instead of completely redesigning the vulnerable architecture, they release "patches," as if trying to plug holes in a sinking ship. All for the sake of backward compatibility with old equipment installed around the world.
And so in 2020, the large Chinese company Shanghai Fudan Microelectronics introduced another smart card based on MIFARE. The manufacturer called it invulnerable to existing hacking methods. The marketing materials were full of loud phrases: "enhanced protection", "elimination of algorithm weaknesses", "next-generation security features". At the same time, the FM11RF08S technical documentation mentioned only "cryptographic protocol improvements" — without a single specific detail.
The hacker community initially responded with the traditional "challenge accepted" and prepared for a quick victory. But something went wrong. Several years passed, and the new cards remained impregnable.
It seems that the developers really did a serious job on the mistakes.
And then a team of researchers led by Philippe Theven came on the scene. They decided to take on this challenge, not suspecting what amazing discoveries lay ahead.
Card operation algorithm
To fully appreciate the discoveries of Theven and his team, we first need to discuss the initial stages of the CRYPTO-1 protocol, which is responsible for the authentication of MIFARE Classic cards.
The user brings the card to the reader.
The reader sends an authorization command to the card, specifying two parameters: the target memory block and the key it will work with. Let's say it's KeyA.
The card's memory is divided into blocks (sectors) — 16 or 40 depending on the model. Each block is protected by a pair of keys with different access rights. KeyA usually allows reading information, such as the owner's identifier, while KeyB allows changing data in the block.
The card responds to the reader's request by generating a four-byte pseudorandom number — Nonce (number used once).
The reader combines the Nonce with a pre-known key. In our case, this is KeyA. This combination passes through the CRYPTO-1 cipher. The resulting encrypted value is sent back to the card.
The card simultaneously performs the same calculations using its copy of the key and the generated Nonce. If the card's calculation result matches the reader's response, the authentication is successful. After that, the system generates a key stream for subsequent data encryption.
All further communication takes place in encrypted form. To access a new block of the card, the nested authentication process is initiated: the reader encrypts the corresponding command, and the card encrypts the new Nonce with the key from the new block. Remember this moment — it will become key in our story.
First findings: features of CRYPTO-1 implementation in FM11RF08S
The research group led by Teven began to study the differences between the implementations of the CRYPTO-1 algorithm in the new version of the card and the original MIFARE Classic.
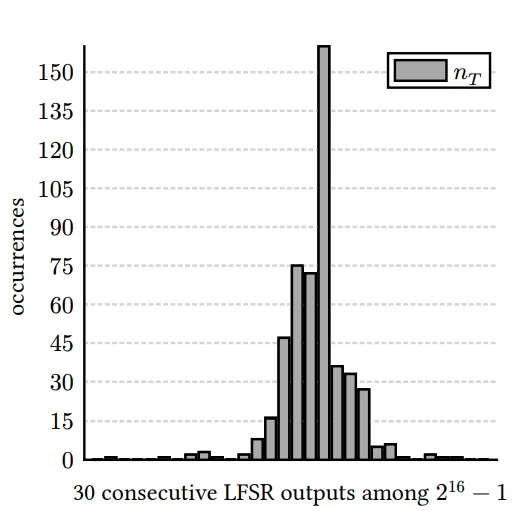
In the new card, static Nonce values were used during nested authentication — that is, numbers that should be random turned out to be unchanged. For comparison: in the original MIFARE Classic cards, the Nonce value was dynamically formed using a Linear Feedback Shift Register (LFSR).
Experienced hackers knew: if you keep the card near the reader long enough and try to authenticate again and again, the generated values become predictable.
This feature of Nonce values in MIFARE Classic makes it possible to conduct so-called Nested attacks.
The developers of FM11RF08S took a different approach. At the first acquaintance of the card with the reader, everything went according to the classic scenario. But then the most interesting part began: during nested authentication, the card issued the same Nonce for each memory block. Further research showed that this value depends on three parameters: the sector number, the card UID, and the access key value. Thus, each FM11RF08S card contained an individual set of constant Nonces tied to a specific combination of keys and sectors.
At first glance, the idea seemed good. The classic Nested attack really didn't work — because now the attacker couldn't predict the next Nonce value, no matter how much time they spent observing the card. But, as often happens in the world of security, by closing one door, the developers accidentally left a window open...
When using one access key for authentication in two different blocks during nested authentication, the card issues different Nonces but encrypts them with the same key. An attacker can collect several pairs of such encrypted values and recover the original key without a full brute force. Researchers called this hacking method the Reused Keys Nested Attack.
Imagine there is an unknown KeyX that is used in several blocks of the card. To select it, it is enough to have access to just one "legal" key in any other sector of the card:
You perform the first authentication using a known key, thus establishing an encrypted connection with the card.
You conduct nested authentication in the blocks where KeyX is presumably used, and save each encrypted Nonce that the card provides.
You iterate through all possible key values. For each collected Nonce, you get hundreds of keys that could theoretically have encrypted it.
You compare the obtained sets of potential keys for Nonce from different sectors. You need to find the key that is present in each set: voila, this is the desired KeyX.
The advantage of this attack is speed: the computer iterates through the keys "offline" without accessing the card. However, two important conditions must be met for a successful attack. First, you need to have at least one working access key — a kind of pass to the system. Second, the same keys must be used somewhere in the card for different sectors.
Even meeting these conditions does not guarantee a successful hack: you will only be able to find out the repeating keys — the rest will remain safe. It may seem like not the most practical hacking method, but this is not all that Philippe Teven's team found.
Suspicious Key
The researchers applied fuzzing — they sent non-standard commands and distorted byte sequences to the card, observing the card's reaction.
In theory, the card should be quite selective in communication. At the authentication stage, it should respond only to three commands: authentication with keyA (code 60), authentication with keyB (code 61), and the HLTA stop command (code 5000). But Philippe Teven's team found a protocol deviation: the card sent Nonce in response to any command of the 6*00 series, from code 6000 to 6f00 regardless of the block.
Intrigued by this behavior, the researchers decided to dig deeper. They took a card with known keys, set different keys keyA and keyB, and began methodically checking all variants of the 6*00 commands. It turned out that the commands could be divided into 4 groups based on the card's behavior:
Group 1: 6000, 6200, 6800, 6a00 → gives Nonce 4e506c9c (authentication successful);
Group 2: 6100, 6300, 6900, 6b00 → gives Nonce 7bfc7a5b (authentication successful);
Group 3: 6400, 6600, 6c00, 6e00 → gives Nonce 65aaa443 (authentication failed);
Group 4: 6500, 6700, 6d00, 6f00 → gives Nonce 55062952 (authentication failed).
When they changed keyA, the Nonce for groups 1 and 3 changed. They made keyA and keyB the same and got two different Nonces instead of four: one Nonce for groups 1 and 2 with successful authentication and another for groups 3 and 4. It seems that for the last two groups of commands, the card expected to receive some other key — keyC…
Key Selection
And then it clicked in the researchers' minds: "What if this mysterious keyC is used in all blocks of the card?" And if so, then... Bingo! The already familiar key reuse attack can be applied to it. The algorithm is simple:
Perform initial authentication using keyA.
Perform several nested authentications using anomalous commands in other memory sections and save the obtained Nonces.
Calculate all possible key values for each collected Nonce.
Compare the obtained sets of values and identify the key that appears in each of them.
The Python script completed the task in less than two minutes and successfully calculated the desired key:
Disappointing Conclusions
Perhaps the story with FM11RF08S will go down in textbooks as a classic example of how not to design security systems. The discovered backdoor turned "the most secure implementation of MIFARE Classic" into a sieve, putting millions of devices around the world at risk. Including at important facilities: airports, power plants, and industrial enterprises.
How to eliminate the risk? Alas, there is only one solution, and it is similar to removing a diseased tooth - a complete refusal to use compromised cards. And their number... well, let's just say that the count goes into millions.
Soon after the first hack of FM11RF08S, an identical backdoor with the same master key was found in older cards from Shanghai Fudan Microelectronics (FM11RF08 and FM11RF32), as well as in products from other manufacturers - NXP Semiconductors until 2009 and Infineon until 2013.
This suggests that the backdoor was deliberately embedded in production many years ago. Maybe for debugging purposes? Or were there some agreements with government agencies? Or... we can only guess. But the fact remains: security systems around the world have been using cards with a built-in vulnerability for years.
This story teaches three important lessons. First: reputation does not guarantee security. Second: the principle of "security through obscurity" in cryptography is untenable. Concealing algorithms creates only an illusion of protection - the only reliable solution is to use open algorithms verified by the expert community. Third: trust, but verify. Independent audit and penetration testing are not unnecessary expenses, but a vital necessity.
P.S. The article is based on original research by Philippe Teven MIFARE Classic: exposing the static encrypted Nonce variant and a number of open publications.










Write comment