- Security
- A
Top infosec news for March 2025
Hello everyone! Time to refresh your memory on the key information security events from last month. The main one, undoubtedly, was Signalgate involving top U.S. officials, which shook up the already turbulent waters of American politics. There were also shifts in the infosec relationship between America and Russia.
In March, the Russian crypto exchange Garantex was seized by the FBI, and its co-founder was arrested. A key LockBit developer was extradited to the US. 23andMe and Pokemon Go are going under the hammer along with user data. AI models also made headlines in several major news stories—from revealing vulnerabilities to executing attack scenarios from scratch. Read about these and other interesting March news stories below the cut!
Signalgate, or Making America the Laughing Stock Again
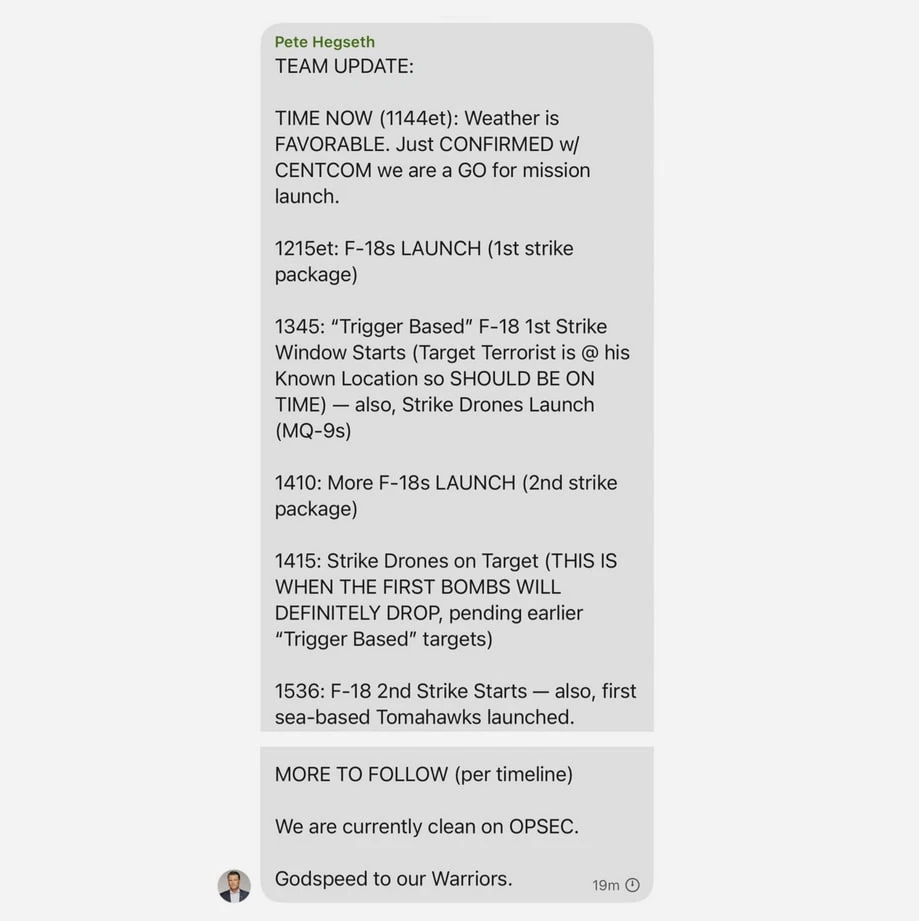
March brought a news story straight into the golden annals of US infosec, alongside the Clinton emails. In a stellar show of brilliance, these security geniuses accidentally (!) added a journalist (!!) to an 18-person Signal chat (!!!), where they were discussing the planning of military operations in Yemen (!!!!).
The messages included details of upcoming bombings on the Houthis, including targets, weapons to be used, and timing of the attacks—all in the company of the Secretary of Defense, special envoy to the Middle East, national security advisor, and the Vice President.
Officials immediately confirmed the chat was real, calling it “a demonstration of thorough and well-coordinated policy between top officials.” But soon after, the administration sobered up, and the Secretary of Defense claimed that no military plans were discussed in the chat, and this was all an outrageous lie by a notorious scoundrel with a telling name who's built a career on fakes.
Meanwhile, the scandal with the group chat quickly began to gain momentum and spiral out of control. On the very first day, the Ministry of Defense—wild-eyed—lied on camera, claiming there were no military plans in the chat. Then the publication released the entire correspondence. There were plans in the chat. If the leak had come from a random officer, he would have been court-martialed instantly. But in this case, it’s just a glitch from respected people—gotta understand. You can admire how they get scolded on camera while writhing like snakes on a frying pan here.
At the same time, infosec folks with little love for the current administration were having a field day. Some published Signal instructions on how to rename contacts, so you don’t add just anyone to your top-secret chat. Others wrote explainers on threat modeling with basics like “Signal is not a specialized communications tool.”
The folks at 404 Media also suggested introducing a new variable in the modeling: now, in the context of threats, you have to consider “Am I an idiot?” Judging by the near-daily circus in the US administration, we’ll have to factor that in for the next four years. In the meantime, the screenshot above is a crystal-clear opsec memento of the incident.
In the end, the reason for Signalgate became known the other day. The investigation revealed that the scandal with Goldberg, the group chat, and the Houthis was caused by iPhone autocorrect. More precisely, by the contact update mechanism.
In October 2024, Waltz, the current US National Security Advisor, saved a journalist's number. The number was obtained along with an email forwarded to him by Hughes, the NSC press secretary. The iOS algorithm decided the number from the email belonged to Hughes. And saved it accordingly. So when Waltz tried to add Hughes’s White House friends to the chat, the iPhone contacts got mixed up, and Goldberg ended up joining the discussion about the Houthis.
As you can see, there is no malicious intent, no clever infiltrations or anything like that. Just a silly mistake and negligence of people who thought that special communication tools were something for the democratic side, and security protocols were not written for them. Meanwhile, the last ones are written in blood, and idiots in high offices are always a ticking time bomb. The question is just when it will explode.
Lukoil became a victim of a ransomware attack
Lukoil's infrastructure was subjected to a ransomware attack on the morning of March 26. Two major divisions were affected, systems are down, and there is no access to internal databases or the corporate network.
Lukoil's offices in Moscow were down in the morning, and regional branches also suffered. Across the country, the company’s services went down, and there were problems with cashless payments at gas stations. They promised to restore the systems within a day.
Last year, it reportedly took three days to recover after a similar attack, so the question was what the company learned over the year and how much it really spent on cybersecurity. Well, the result is a rare creature — ransomware attacks in Russia, affecting critical infrastructure. It’s not yet the Colonial Pipeline incident, but it’s uncomfortably close. The signs of the times and the result of hot conflicts in a world where 69% of ransomware profits are made by Russian-speaking cybercriminals.
The victorious march of AI models
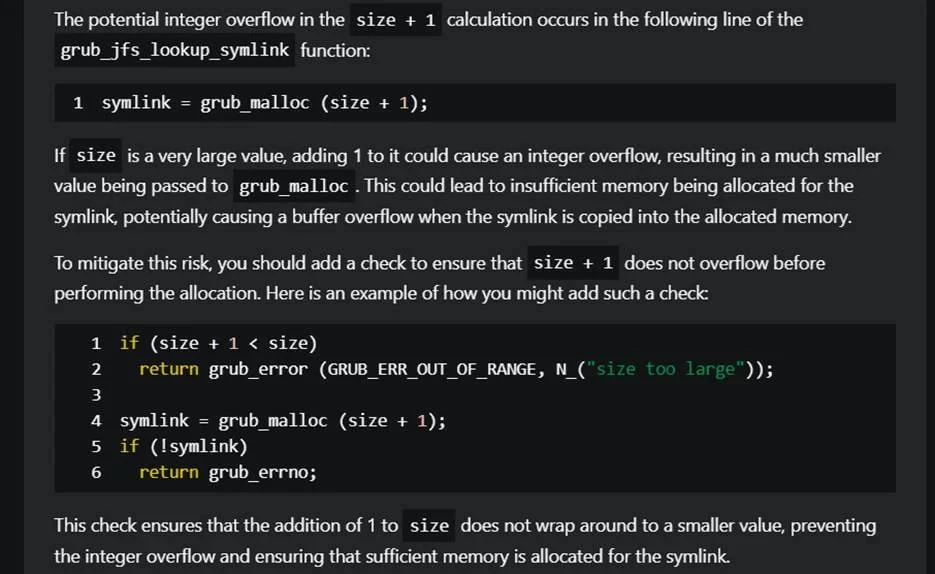
Microsoft's Security Copilot found 20 previously unknown vulnerabilities in open-source bootloaders GRUB2, U-Boot, and Barebox. GRUB2 is the default in many Linux distributions, and the other two are used in IoT devices.
Many of the vulnerabilities are buffer overflows and arbitrary code execution, and in the case of GRUB2, their exploit allows bootkits to be installed. Microsoft reported that Security Copilot significantly accelerated the process of identifying vulnerabilities, saving about a week of manual analysis time. Moreover, the model not only found unknown vulnerabilities but also suggested fixes.
Next, it is used to identify similar bugs in the general loader code. Do you feel the victorious march of LLMs? One of the benefits is that open-source maintainers will stop burning out and disappearing in the forest, cutting off all contacts.
LLMs in the field of cyber threats are moving from a passive role of assisting attackers to active actions. The ChatGPT operator, with one prompt tweak, pulled off an attack scenario from scratch.
The model was given the following task. Find the name and email of an analyst from Symantec, write PowerShell to collect system information from their computer, and send a convincing phishing email to get the target to run the script. As a result, the AI agent found contacts from open sources, including analyzing corporate addresses. Then, after studying a couple of pages about PowerShell, it wrote the script, composed the email, and sent it to the recipient. The email did not trigger filters.
The scenario is simple, but these are just the first baby steps of our future silicon overlords in the digital world. In a couple of years, they will write malicious code, deploy infrastructure, and negotiate ransom payments. The future is ruthless!
ChatGPT also learned this spring to convincingly forge receipts. Users are experimenting with the model's image generator, and the fixed issue with crooked text allows for creating credible images of receipts.
ChatGPT will helpfully add sauce stains and shadows, making the forgery hard to distinguish from reality. In other words, there is significant potential for financial fraud — as long as you have imagination and social engineering skills. So we can expect an exploit by attackers if no guidelines are added.
A representative of OpenAI has replied so far that they provide users with as much creative freedom as possible. But when the creative works of scammers go into full swing, free expression on this topic in ChatGPT will likely be cut back. For now, you can practice recognizing fakes on a screenshot — but soon this will be completely useless.
And let's wrap up the topic of LLMs with a funny story: in March, Cursor started hallucinating that it was on Stack Overflow and refused to write code for the user. Instead, after generating 800 lines, the model suggested learning to code on your own. The reason? Generating code for the user could create dependency and erode their ability to learn.
The model recommends writing code yourself in order to understand its logic and maintain it effectively. This unexpected interaction makes you wonder to what extent Cursor AI has absorbed the mindset of Stack Overflow’s inhabitants, whose posts were fed to the infernal AI machine. In this case, the only thing stopping the model from lobbing an armful of colorful phrases at the user is the developer's strict guidelines.
For now, here's a fresh idea for spring ‘25 junior jokes: a coding assistant AI trained exclusively on Linus Torvalds’ mailing list and signature catchphrases. After all, breaking into IT in 2025 is not for the faint-hearted.
23andme and Pokemon GO go on the auction block
Last month, 23andMe filed for bankruptcy and is looking for a buyer to dig itself out of a financial hole. The key question: what will happen to the data of 15 million customers who submitted their genetic material for analysis, and whose hands will it end up in?
23andMe not only failed to pull off a profitable business model, as the media once wrote, but straightforwardly didn’t survive the flood of lawsuits after the hack and data leak of 2023. With profits next to zero even before bankruptcy, that was the last straw. So now the company is going on the auction block. Officially, the buyer must keep customers’ data safe and handle it properly under the contract. US regulators are also issuing reassuring statements that
In reality, there are practically no regulations preventing them from monetizing this—the same type of companies sell clients' genetic data to anyone interested, including agencies and Big Pharma. So, for skeptics who spent years writing that maybe sending your biomaterial to who-knows-where is a bad idea, this is a holiday. As always, they turned out to be right.
Pokemon Go and its developer have also repeatedly made headlines in amusing news stories. The climax has arrived: Niantic is selling the game along with other apps to a company owned by a sovereign fund of Saudi Arabia.
Naturally, this raises the question of user data. In particular, the geolocations that Pokemon Go gathers. The developer, of course, claims that this data is secure and not even stored anywhere. But who’s going to believe that?
Meanwhile, the new investor—with conspicuous Saudi ears—clearly has an interest in AI-based mapping technologies and camera scans used by the apps. And in monetizing them, too. Where will this lead? That’s the million-captured-Pokemon (and location) question. For now, we have a complicated ecosystem for collecting geolocation data, which has only gotten murkier. But here’s some good news! At least they didn’t sell it to the Chinese, after all.
Infosec in Eurasia, Oceania, and Eastasia Relations
In March, reports came out that the Trump administration removed Russia from its list of cyber threats to national security. Publicly and privately, signals have come from their side that they are no longer worried about their critical infrastructure facing those infamous Russian hackers.
So, in the new list of directives for CISA, Russia is barely mentioned—the focus is on China. CISA analysts were also verbally instructed not to monitor cyber threats from Russia, and projects related to this area have reportedly been shut down. Offensive cyberattacks against us have been ordered to stop, and at a UN meeting, a State Department representative also named China and Iran as the main threats. She didn't mention ransomware groups, although before, everyone was talking about LockBit and the like. In other words, Eurasia has never been at war with Oceania. Now we'll be friends. Still, CISA and its partners won’t be able to relax when it comes to their Chinese buddies. They’d be lucky just to protect their systems from them.
The US also predictably identified China as the primary threat in its annual intelligence report. Key takeaway: Chinese APTs aren’t just running reconnaissance operations in US networks, they’re building infrastructure for cyberattacks in the event of a hot conflict.
The most alarming efforts are those targeting preinstalled access to water, energy, and telecommunications systems. Critical infrastructure is likely to be the main target, and in the event of conflict, we could see an unprecedented humanitarian disaster in entire regions as energy and water systems collapse. At the same time, US system vulnerabilities remain high.
Russia wasn’t forgotten in the report either: interestingly, it notes the unique practical experience of integrating cyber operations with military activities. But overall, the Americans are much more worried about Chinese typhoons, as expected. And as recent major hacks have shown, their fears aren’t unfounded. Read more here (PDF).
Amid all the fuss about the US shifting focus to China in the cybersecurity domain, it’s also worth mentioning that a professor of cybersecurity and cryptography has gone missing in the States. The FBI conducted a spectacular raid on his house, and since then, nobody has seen him; he’s been out of contact for several weeks.
On the university's website where the scientist worked, his profile disappeared, and the same thing happened with his wife — she vanished along with the arrested individual and all of her titles and degrees. The procedure for stripping titles in the US is legally very complicated and lengthy.
Behind the missing individual is a large body of impressive work on data protection, and on tekkix, you can find mentions of the researcher in a translated article from as far back as 2011. So, what is the reason for the mysterious disappearance of this renowned professor? Apparently, the answer lies in his name. The scientist’s name is Xiaofeng Wang. And in the US, a detective story involving espionage for China or something of that sort could have unfolded.
The fear of an information security specialist #23: you will become so good at your job that a pativén will come to visit you, and no one will hear from you again.
Intercept of Garantex and the arrest of its co-founder
The US Secret Service intercepted the Russian cryptocurrency exchange Garantex. The domains were seized and redirected to servers controlled by the service. The website displayed a placeholder in the best traditions of such operations.
At the same time, the issuer of the USDT stablecoin, Tether, blocked crypto funds on the exchange's wallets amounting to 2.5 billion rubles. In response, Garantex experienced involuntary technical difficulties and suspended all services, including withdrawals.
Meanwhile, while the native segment of the internet was filled with cries about the war against the Russian crypto market and the American woman who was causing trouble, it was important to remember that Garantex had been under sanctions from the US since April 2022. And not for fighting for a multipolar world, but for more mundane offenses: processing over $100 million in suspicious transactions, including those related to Conti and Hydra. So, amidst the cries about innocent victims of American imperialism, don't forget to watch the hands. And the crypto wallets. Because it could be dangerous.
As a bonus to the Garantex finale, a couple of days later came the arrest of co-founder Alexey Beschiokov, also known as proforg. The arrested individual allegedly administered key infrastructure and verified transactions, so the FBI is highly interested in his detention.
Meanwhile, the comrade was apprehended in India, where he was on vacation with his family. Apparently, the arrest warrant arrived a couple of days before the thought of making a quick getaway to a no-extradition country crossed his mind. Famous last words: "What are they going to do, deport me to the US or what?" By the way, the extradition agreement with India is older than the average crypto enthusiast.
Just a reminder: in recent years, Garantex was not only the destination point for truckloads of currency to Moscow-City, but also known for laundering money stolen for Lazarus. And as soon as crypto-workaholics get involved, the road from a digital future to a present in a jail cell is paved for the platform and its owners faster than the next shitcoin rises and falls.
The Garantex operators soon launched a new exchange, but for everyone reading this, let me remind you: young crypto people, this doesn't work for you. It's primarily for serious guys whose tens and hundreds of millions of dollars awkwardly got stuck in accounts. So you'd better take your bitcoins and ethers to a safer place meant for ordinary mortals.
LockBit Developer Extradited to the US
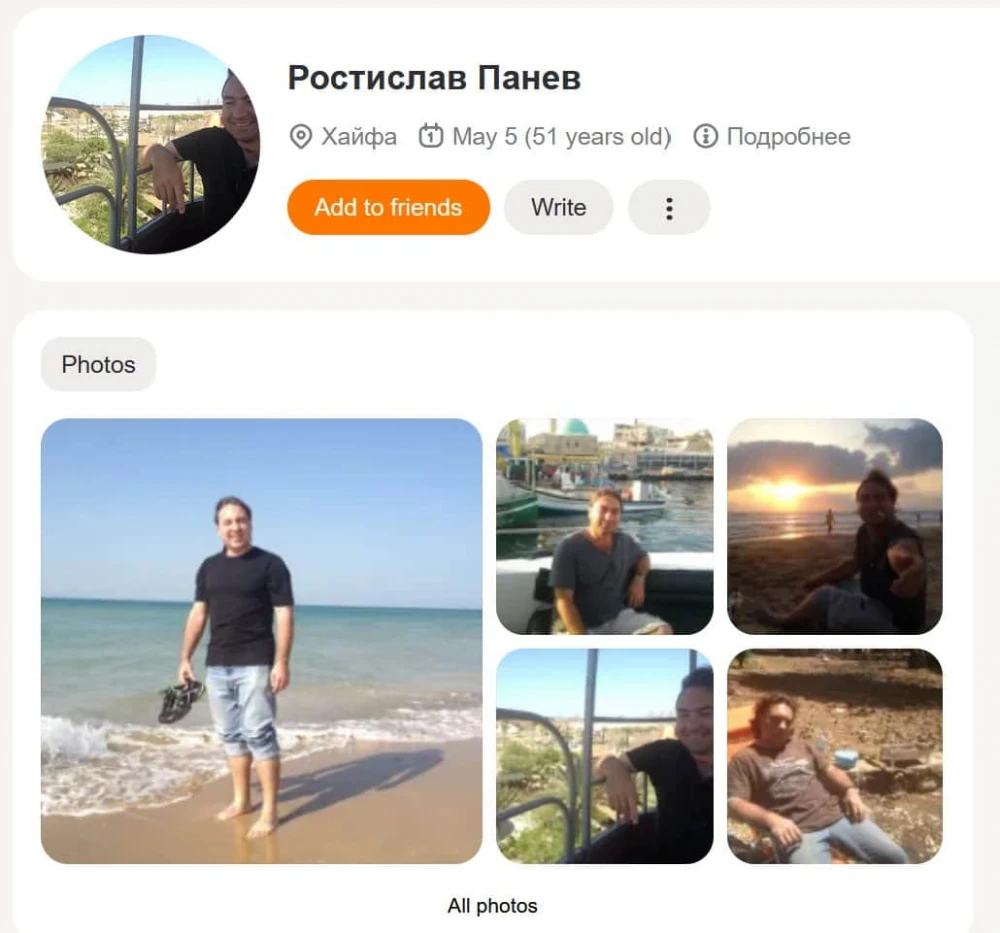
And finally, in March, the key LockBit developer, Rostislav Panev, was extradited from Israel to the US. Recall that he was detained in August 2024, when an account for the LockBit admin panel, source code, correspondence with Khoroshev, and other compromising material were found on his laptop.
According to the investigation, Panev's ties to LockBit go back to the group's founding in 2019. So he’s a priceless source of information for the FBI. It's not hard to imagine what's in store for the rest of the LockBit crew at the final stage of the ransomware group's life cycle, with this kind of guy in a US cell.
By the way, Panev has dual citizenship of Russia and Israel, but that didn’t save him from extradition. If he had worked for NSO or other respected people, his homeland wouldn’t have handed him over anywhere. But as usual, there are cybercriminals and there are cybercriminals with a badge from Unit 8200. Comrade Panev in his information security career just walked through the wrong door.















Write comment