How to Catch Phishers: An Overview of Technical Tools for Protecting Mail Traffic
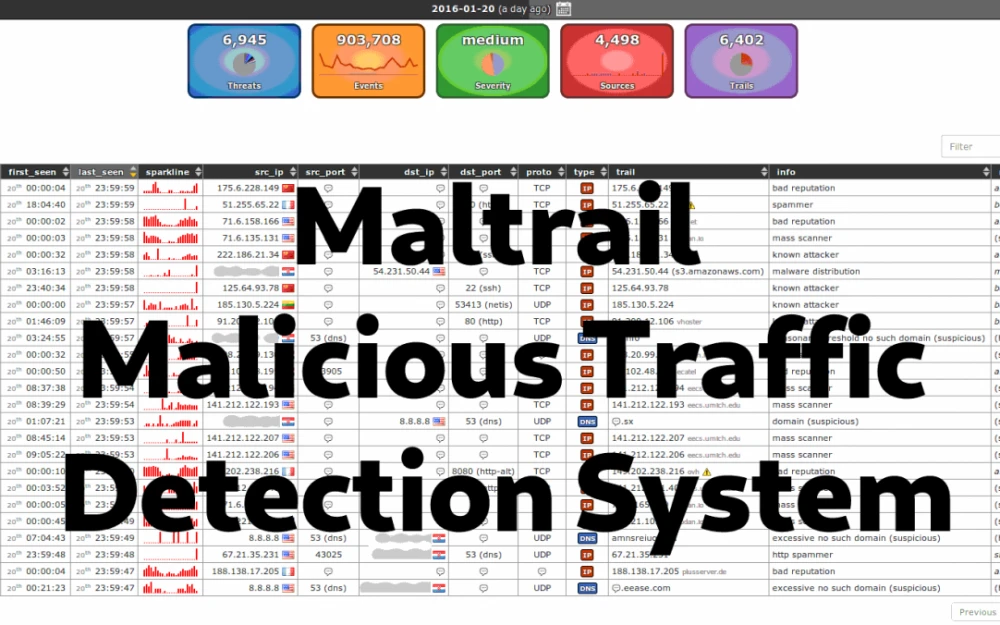
Protection against phishing has been discussed and written about in our industry more than once, but as our experience shows, this topic remains highly relevant. Attackers…