- Security
- A
Analysis of vulnerability CVE-2024-38227 in Microsoft SharePoint
On September 10, Microsoft released another set of updates, fixing 79 vulnerabilities in various products. Our attention was drawn to patches for Microsoft SharePoint — an extensive system with site management features. Of the five vulnerabilities included in the September release, four allowed the execution of external code, one created a DoS threat. We chose CVE-2024-38227 for analysis — an RCE vulnerability of a privileged user. For us, such research is an opportunity to study Microsoft SharePoint itself and understand the current theory of its exploitation.
About the product under study
Microsoft SharePoint is a CMS with a wide range of functionality. It allows you to create sites, from internal corporate services to document management portals. In addition, the architecture of Microsoft SharePoint involves the interaction of several servers within one "farm". All this provides wide opportunities but also significantly increases the attack surface. Microsoft SharePoint is written in C#, uses IIS as a web server, and MS SQL as a data store.
Start of the study
As always, when analyzing closed-source software, the task was to understand what exactly was changed during the update. To do this, we chose the classic comparison method and installed Microsoft SharePoint 2019 twice: versions before and after the patch.
Microsoft SharePoint contains about 700 executable files, of which at least 400 are C# DLLs. Obviously, some automation is needed here. The first reaction in such projects is usually the desire to decompile all DLLs through dnSpy or similar decompilers for C# and then diff the text, but this approach gave a lot of false positives (yes, we still checked it). To make the comparison more correct, it is necessary to analyze it properly - at the IR level. Therefore, we switched to BinDiff with IDA, and here's how:
Recursively ran through the old and new projects and converted all found executable files to IDB.
Converted IDB to BinExport.
Compared BinExport files through BinDiff, recorded the result in a common database.
After the comparison, it turned out that only two files were really changed:
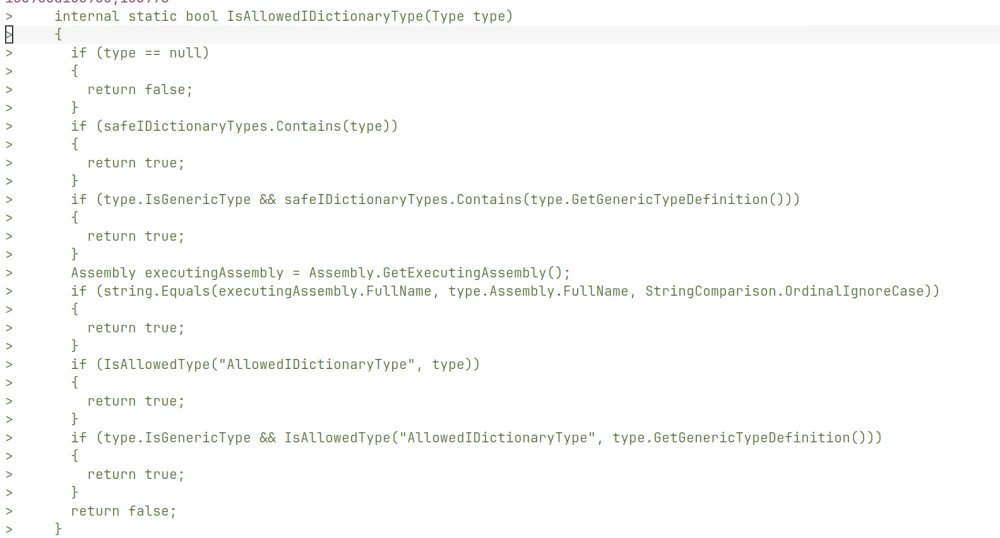
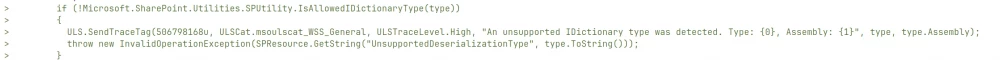
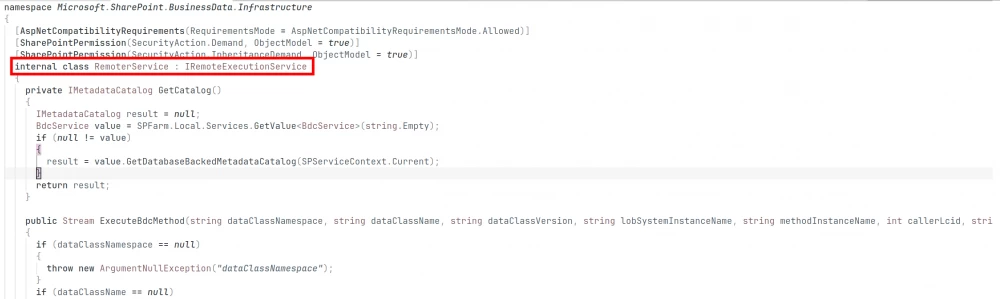
Among the list of changed files, we were, of course, interested in Microsoft.SharePoint.dll. The diff clearly shows patches related to deserialization. The IsAllowedIDictionaryType method was added to the SPUtility class, which checks the type implementing the IDictionary interface for presence in the allowed list of verified types.
This method is used in the SPAutoSerializingObject class, the vulnerability in which, according to ZDI, leads only to DoS.
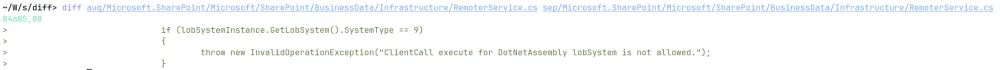
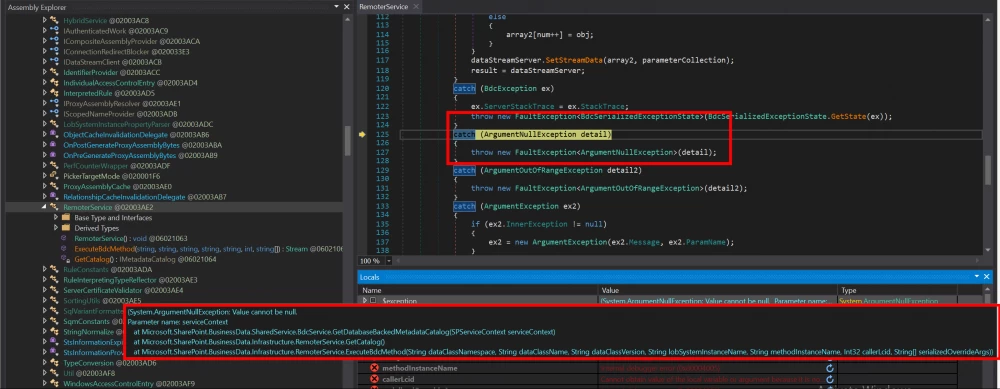
We were much more interested in the following changes in the RemoterService and LobSystemParser classes, which presumably correspond to CVE-2024-38227 and CVE-2024-38228:
Judging by the content of the exceptions, it can be assumed that Microsoft has removed the ability to execute .NET assembly. Looks like RCE, doesn't it?
Vulnerability Research
For further analysis, it is necessary to investigate the changes to the ExecuteBdcMethod method of the RemoterService class: first, we need to understand how to call it. The RemoterService class is an implementation of the IRemoteExecutionService interface. This is a ServiceContract that defines the ExecuteBdcMethod operation.
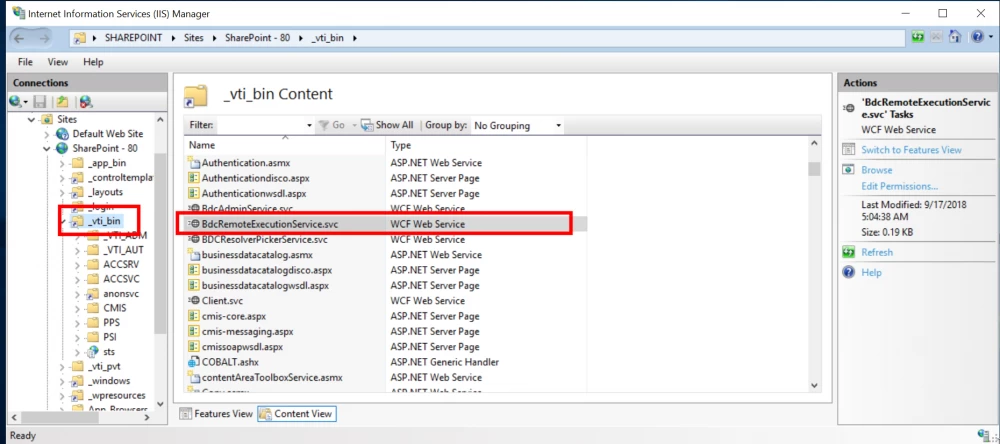
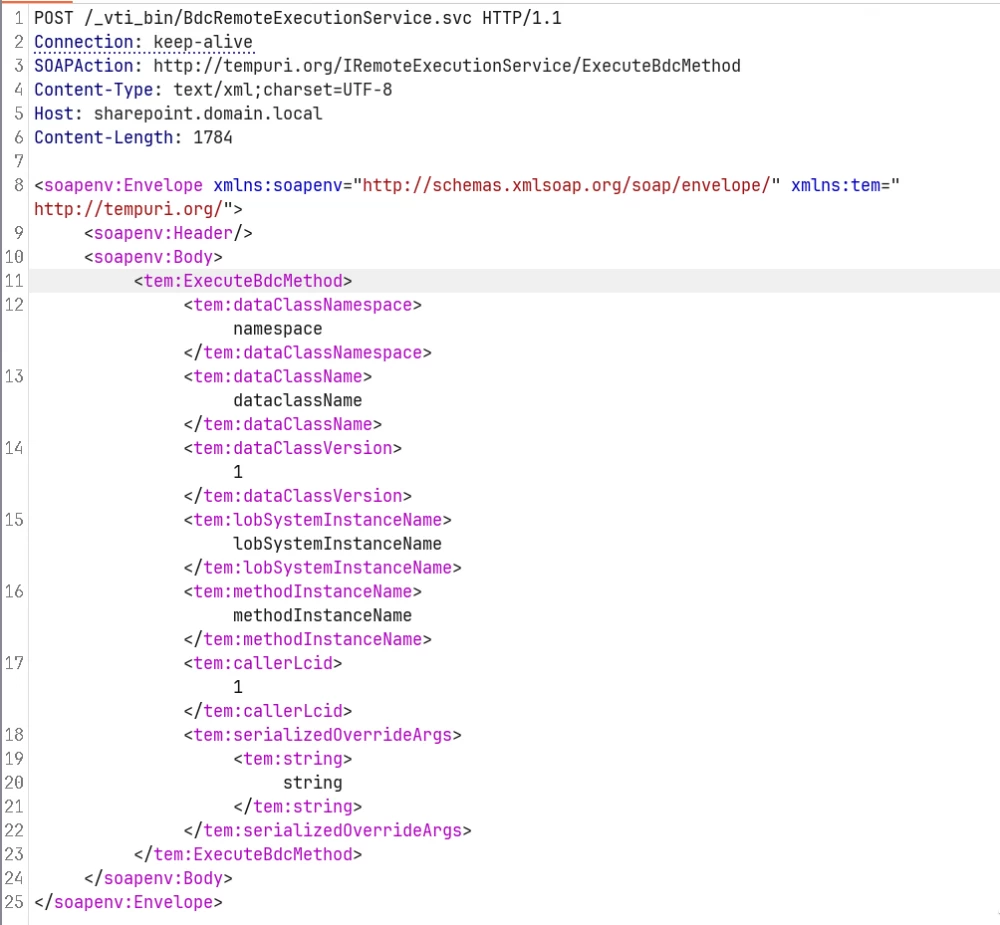
At this point, we reviewed the references to RemoterService and found the BdcRemoteExecutionService.svc file. According to the IIS configuration, this SVC file can be accessed at /_vti_bin/BdcRemoteExecutionService.svc.
The method we are interested in can be called by accessing the service using WCF (Windows Communication Foundation).
Windows Communication Foundation (WCF) — «framework for building service-oriented applications». This framework allows for the implementation of communication between distributed services. Interaction between services is done in the form of interaction with language entities on both the client and server sides.
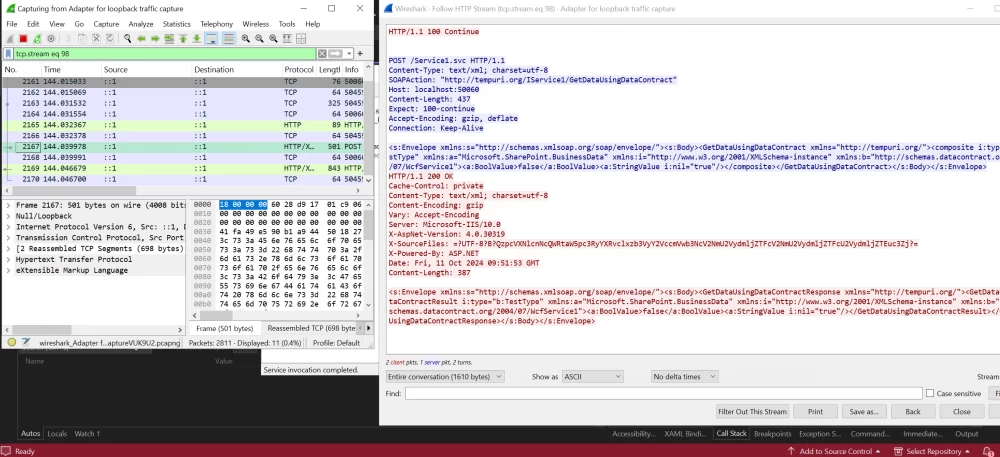
We could not find ready-made information on how WCF works at the network interaction level. WCF itself uses SOAP, but it is not clear what to use as namespace and SOAPAction if this is not explicitly specified in the contract. Therefore, in order to understand what exactly to specify, we created a small stand with a test service in C# that uses WCF and analyzed the traffic.
It turned out that if the namespace is not explicitly specified, then by default http[://]tempuri[.]org is used. In SOAPAction, you need to specify the namespace (in our case http[://]tempuri[.]org), the type of ServiceContract, and the type of OperationContract.
In our case, it turns out that as SOAPAction you need to specify http[://]tempuri[.]org/IRemoteExecutionService/ExecuteBdcMethod.
Based on the information received, a similar request was made to call the method from BdcRemoteExecutionService.svc.
We called the method we were interested in. Now it is worth understanding what this service is and what this method does. Judging by the name of the class, method, and its arguments, we can call the methods of some BDC.
BDC (Business Data Connectivity service) is a service within Microsoft SharePoint that allows you to create integration with data from external sources. BDC provides the ability to perform CRUDQ operations on data from external sources. Data sources can be SQL connection, .NET assembly, WCF service.
Using legitimate functionality available to a privileged user, we import the BDC model from the .NET assembly:
Then it remains only to execute the request to call ExecuteBdcMethod, after filling in the parameters with the necessary values to obtain arbitrary code execution.
Conclusions
When we decided to investigate CVE-2024-38227, we could not imagine how complex and intricate Microsoft SharePoint would be.
The complex design and loaded architecture seriously complicate the analysis of such projects and create a real challenge when it is necessary to track data and code flows. However, during such research, we develop various tools and accumulate knowledge that is needed later for use in services with a similar stack.
We sincerely hope that this research was useful to you. Stay tuned!
Article author:
Elizar Batin, Senior Vulnerability Research Specialist










Write comment