- Security
- A
How to find both the goblin and the rat. Interview with researchers from the Solar Group who discovered the GoblinRAT malware
The tekkix news service visited the SOC Forum 2024. This is another event dedicated to cybersecurity, organized by the Solar Group of companies. Due to a busy work schedule, I managed to get there only on the third day and only for a few hours. However, I was able to talk with Solar Group specialists about a rather interesting study. It was dedicated to the unique GoblinRAT malware, capable of remaining unnoticed in the infrastructure of attacked organizations thanks to advanced masking and bypassing security systems. The malware was found in the networks of several Russian government organizations and companies providing services to the public sector, with signs of presence since 2020. In each of the affected organizations, the attackers gained full access to the network.
The tekkix information service visited the SOC Forum 2024. This is another event dedicated to cybersecurity, organized by the Solar group of companies. Due to a busy work schedule, I managed to get there only on the third day and only for a few hours. However, I was able to talk with specialists from the Solar group of companies about a rather interesting study. It was dedicated to the unique malware GoblinRAT, capable of remaining unnoticed in the infrastructure of attacked organizations thanks to advanced methods of masking and bypassing security systems. The malware was found in the networks of several Russian government organizations and companies providing services to the public sector, with signs of presence since 2020. In each of the affected organizations, the attackers gained full access to the network.
GoblinRAT has a number of sophisticated stealth features: it disguises itself as legitimate processes and, if necessary, self-destructs by overwriting files to complicate the investigation. The attackers placed control servers on hacked legitimate sites, hiding malicious traffic.
I decided to ask Vladimir Nestor, head of the malware analysis group at the Solar 4RAYS center of the Solar group of companies, and Konstantin Zhigalov, an engineer of the incident investigation group at the Solar 4RAYS center of the Solar group of companies, about this malware and the study itself. Enjoy reading!
How were the first traces of GoblinRAT found? Is it an existing malware or a completely new one? Tell us more.
Konstantin Zhigalov:
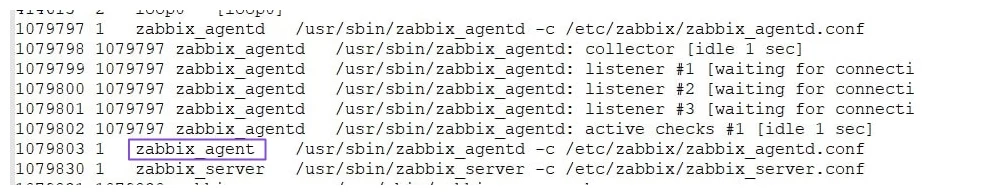
Detection occurred as follows. An IT company providing services to the public sector noticed suspicious activity: user password hashes were dumped from the domain controller and system logs were cleared. Initially, the in-house IT security specialists tried to investigate the incident on their own but could not gather more information. Then they turned to us. We came to the customer's infrastructure and started analyzing the servers. For a long time, we could not find any signs of the attacker's persistence in the infrastructure, as he used only the pre-installed software in the system. For example, Python, SCP, SSH tunnels, and netsh portproxy on Windows to proxy traffic. We gradually expanded the search area, collecting more and more data. Finally, in one of the memory dumps, we found suspicious strings that were not tied to any process but were simply in the memory. This confirmed the presence of malware in the infrastructure. We continued to search and, after analyzing several more servers, found a suspicious process of a modified Zabbix agent, which differed from the legitimate one in that it did not have the letter "D" at the end of the binary file and service. We collected the binary file and handed it over to our colleagues from the Solar 4RAYS malware analysis department.
The question is: is this a standard attack through a contractor?
Zhigalov Konstantin:
Yes. By hacking the contractor organization, the attackers were able to penetrate the infrastructure of client companies.
Was it possible to attribute the attack to any group, or is this a new group?
Nestor Vladimir:
No, it was not possible to attribute this attack to a known group. The reason is the lack of artifacts for attribution. We studied GoblinRAT, but did not find any mentions of it in reports from other vendors or in open sources. We tried to use Yara rules for searching, but found nothing. We reached out to colleagues in the cybersecurity market who have a global sensor infrastructure around the world, but they also did not find GoblinRAT or anything similar in their collections. We only found individual components, such as a Python script, but the programs mentioned in the reports were no longer there.
So, was the attack only on one company serving several departments, or was this GoblinRAT found in other contractors?
Zhigalov Konstantin:
In the first case, it was a company providing services to the public sector. Later, we found two more infected objects not related to the first ones. These were also government organizations. It can be said for sure that the attackers are interested in public sector data.
So potentially there could be more?
Zhigalov Konstantin:
Of course, there could be more. That is why we published a detailed description of GoblinRAT with Yara rules and indicators of compromise on the Solar 4RAYS blog. This allows organizations to check their infrastructures.
If we speculate, could this be hacktivism? Or, given the described features, are we talking about a high-class attack with financial or possibly political goals?
Nestor Vladimir:
We do not have the data to accurately name the responsible group. But the motivation of the attackers is clearly espionage. The stolen data did not surface in the public domain, and the infrastructure was not destroyed. The attackers managed to maintain full control over the victim's network for three years without causing visible damage.
Zhigalov Konstantin:
We know that the attackers were in the infected infrastructures from 6 months to 3 years. They minimized the use of third-party software, creating as little noise as possible. For example, they could have installed 7-Zip or WinRAR for archiving, but instead, to hide their presence, they used only pre-installed software. In general, their goal was to remain unnoticed for as long as possible.
Did the attackers manage to obtain any critical information? Were they mostly on the perimeter, or did they penetrate the network?
Zhigalov Konstantin:
In the infrastructures we observed, the attackers had full access. They could do whatever they wanted and had the rights of domain administrators and Linux system administrators. As for the criticality of the data, only the owner can know about it.
Were there any difficulties in eliminating the attack, given the full access of the attackers and their ability to monitor your actions?
Nestor Vladimir:
Yes, there were difficulties. The attackers did not settle on one host but built proxy chains within the organization using GoblinRAT, moving through nodes, for example, dumping password hashes.
Were there situations where you had to act extremely carefully so that the attacker would not notice that they had been discovered?
Nestor Vladimir:
Yes. All the attackers' activity was concentrated on one host, but they settled on another. To find all traces, we had to scan the entire infrastructure. This process is complicated by the fact that administrators do not always remember all the nodes in their infrastructure.
And the departments you discovered, do they belong to one industry or not?
Zhigalov Konstantin:
This is the public sector. We cannot comment in more detail.
Is there a possibility that a backdoor may remain in some of the scanned and cleaned departments?
Zhigalov Konstantin:
We thoroughly scanned the infrastructure and removed everything found. Then we monitored network and host activity. However, everyone understands that highly skilled attackers can penetrate the network again with new code samples. Therefore, the level of security in the organization must be constantly increased.
So, they will be heard from again, as several agencies have already been affected. They could have gone into hiding after your publication and then reappear?
Nestor Vladimir:
That's a good question. We last observed GoblinRAT activity at the end of 2023. Since then, we have not recorded any attacks using this malware. Perhaps the attackers have gone into hiding or changed their command servers.
And did Dark Web monitoring show any activity?
Zhigalov Konstantin:
It would be interesting if one of the groups admitted that this was their work. But an attacker of this level is unlikely to talk about their activities on forums or channels. We publish this story, post Yara rules and indicators of compromise so that other organizations can scan their infrastructures. If someone finds something similar, we will be happy to continue working together to study this malware.
Nestor Vladimir:
We last saw GoblinRAT activity in 2023, but we are publishing the report only now, as we have been monitoring activity for almost a year, expecting the attackers to return. But so far, everything is quiet.
Have you come up with a name for the new group?
Nestor Vladimir:
We cannot attribute the attackers to any specific region, at most something like NGC, as astronomers do. In our taxonomy, this is some group about which we can say little so far.
How is the attribution of an attack to a specific region determined?
Zhigalov Konstantin:
The simplest way is to detect some traces in the code or on the servers that are characteristic of a particular language. In addition, each group has its own tactics and techniques. For example, specific folders for anchoring, vulnerabilities they prefer to exploit, phishing emails. Taken together, this often allows you to establish the regional affiliation of the attack.
Could the group that released "GoblinRAT" have been arrested at the end of 2023, and for this reason the activity stopped?
Nestor Vladimir:
Interesting question. In the event of an arrest, we would have learned about the malicious code of this group. However, no similar code has been found anywhere, so it is difficult to say "yes" or "no".
As Vladimir and Konstantin told me, based on the analysis of the malware, indicators of compromise and detection logic were developed so that other companies could detect GoblinRAT in their systems. In general, with these malware, trojan viruses, phishing, and other tricks, I have become cautious about everything. I install antivirus on different devices, on phones, and do not store critical files in the cloud. However, some of my passwords are still found to be compromised by antivirus. After that, I change the security system and update the passwords. I will continue to release such materials to spread information about such problems and how to solve them. After all, information security, digital hygiene, and safety techniques require regular repetition. Thank you for reading!









Write comment