- Security
- A
In Windows, an 8-year security flaw has been discovered that Microsoft does not want to fix
Ignoring vulnerabilities in operating systems or other software products is fundamentally an unimaginable situation. On the contrary, developers always strive to find the source of the breach and eliminate it as quickly as possible, even if it concerns some minor utility. After all, whether users are protected from external threats depends on this. Especially when it comes to such a global platform as Windows. But circumstances can vary, and sometimes companies consciously go against the rules, ignoring very real dangers.
Microsoft has refused to fix a vulnerability in Windows identified as ZDI-CAN-25373, which has been actively exploited by hackers since 2017. Despite the obvious danger, the company classified the issue as "non-essential" and decided not to release a patch with a fix. This is what we'll talk about today.
What is ZDI-CAN-25373 and why is it dangerous?
The vulnerability was discovered in the system responsible for displaying the content of shortcut files (.lnk). Thanks to it, attackers can create a specially crafted LNK object that appears safe when viewing its properties but can actually contain hidden commands.
The attack mechanism is quite sophisticated: attackers create .lnk files with a large number of whitespace characters in the COMMAND_LINE_ARGUMENTS structure. However, if a user tries to check the properties of such a file, Windows cannot correctly display the malicious arguments in the designated area of the interface.
To further complicate the detection of malicious code, attackers create giant shortcut files of up to 70 MB. This prevents the file from being analyzed by standard means, and users most often abandon this idea.
But worst of all, for a successful attack, it is not even necessary to exploit additional vulnerabilities or elevate privileges. It is enough for the user to simply run the modified file, and then it’s a matter of technique.
Malicious code can even install a backdoor, providing hackers with persistent remote access to the system. This way, attackers gain access to the victim's confidential data, including passwords, financial information, and personal documents. When it comes to “infecting” corporate devices, the attackers can use it to further spread malware within the organization's network, install ransomware that locks access to data, or even completely destroy information on the hard drive.
What is the danger of the ZDI-CAN-25373 vulnerability?
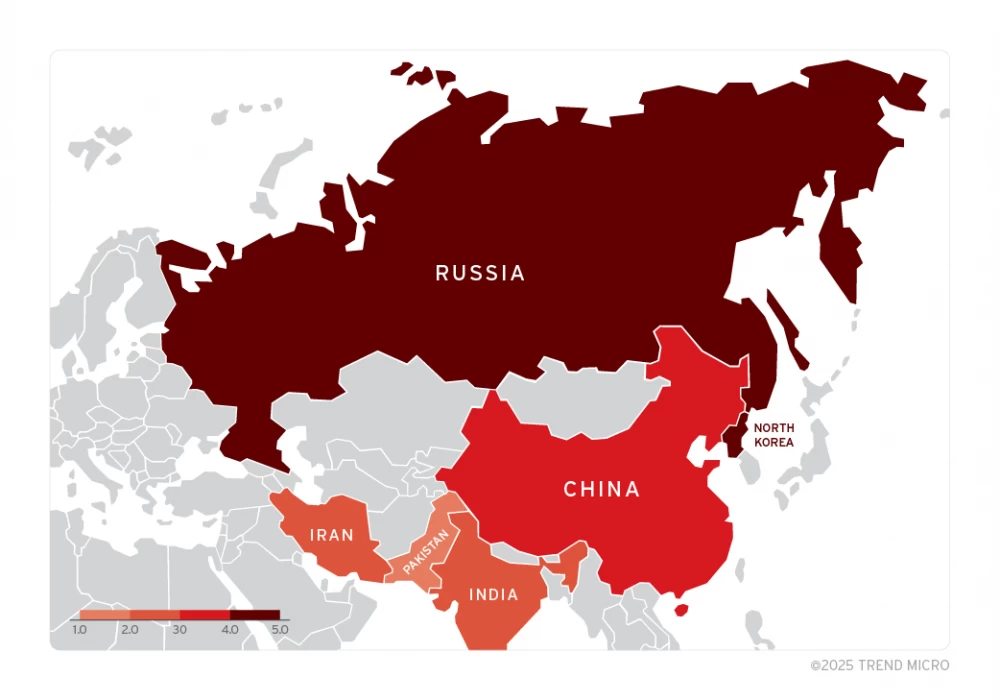
The geography of attacks using ZDI-CAN-25373 covers almost the entire world, but the largest number of victims has been recorded in North America, Europe, East Asia, and Australia. An analysis of targeted sectors shows that the following have been affected:
Government institutions at various levels
The financial sector, including traditional banks and cryptocurrency organizations
Telecommunication companies
Military and defense structures
The energy sector
Analytical centers and non-governmental organizations
This list of targets confirms that the vulnerability is primarily used for targeted attacks on high-value targets, rather than mass campaigns against ordinary users. This means that the list of potential victims includes an unlimited circle of individuals, creating a serious danger.
Why does Microsoft refuse to fix the vulnerability?
The ZDI researchers who discovered the vulnerability acted according to standard procedure: they reported the issue to Microsoft through the official vulnerability reporting program. However, the company stated that they do not plan to release a patch in the near future.
This decision raises questions, considering the scale and seriousness of the problem. After all, we are talking about a vulnerability that could be used for cyber espionage and data theft from critically important sectors of the economy and government administration. Therefore, the responsibility for protection now falls on the shoulders of the users themselves and, in the case of the corporate sector, system administrators.
Here are some recommendations that can help reduce the risk of a successful attack:
Be vigilant when opening .lnk files, especially those received from unverified sources or via email.
Use comprehensive security solutions, such as Trend Vision One, which can detect and block attempts to exploit ZDI-CAN-25373.
Regularly check your systems for suspicious .lnk files, especially those with unusually large sizes.
Train employees to recognize potentially dangerous files and not to open attachments from unverified sources.
The ZDI-CAN-25373 vulnerability poses a serious threat to Windows users, especially considering that Microsoft does not plan to release a patch in the near future. And the active exploitation of this vulnerability by hacker groups worldwide only exacerbates the situation.
In the context of growing geopolitical tensions and conflicts, one can confidently expect an increase in the complexity of attacks and the use of zero-day vulnerabilities, as both states and cybercriminals seek to gain a competitive advantage over their opponents.
Until an official fix is released, users and organizations should take necessary measures to protect their systems. It is especially important to increase vigilance regarding shortcut files and use specialized security tools.
Some antivirus programs already have built-in protection against exploiting the vulnerability. However, a full resolution of the issue requires an official patch from Microsoft, which, unfortunately, is not expected in the near future.





Write comment