- Security
- A
Security Week 2606: Malicious Update of eScan Antivirus
On January 20, an attack on the supply chain was recorded, affecting the Indian company MicroWorld Technologies, the developer of the eScan antivirus product. Company representatives later informed BleepingComputer that attackers had hacked one of the regional servers and replaced the antivirus update file delivered to customers. The attack was discovered "externally" by specialists from Morphisec, who informed the manufacturer a day after the attack began.
Experts from Kaspersky Lab published a detailed analysis of the malicious code used in the attack. According to their assessment, this is a rather unusual attack vector—compromising antivirus software. Moreover, the attack was carefully prepared: the attackers not only hacked the update server but also developed the malicious code to work most effectively considering the features of the compromised legitimate software.
The majority of the victims recorded by Kaspersky Lab's telemetry were located in South Asian countries: specifically in India, Bangladesh, Sri Lanka, and the Philippines. When accessing the hacked update server, users of the antivirus software received the malicious file reload.exe. It was saved at the path C:\Program Files (x86)\escan\reload.exe and was executed every time the antivirus components accessed it. The fake update file was signed with an invalid digital signature and heavily obfuscated. Upon first execution, actions were primarily performed to complicate further detection and removal of the malicious modules: several components of the eScan antivirus itself were deleted, and system folders C:\Windows, C:\Program Files, and C:\Program Files (x86) were added to its exclusions. The hosts file was modified to point to update servers with invalid IP addresses, making a relatively simple solution to the problem impossible for affected users by sending a "correct" update.
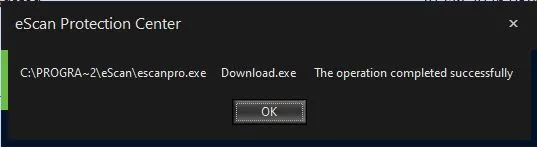
Interestingly, during the analysis of the incident, experts from "Kaspersky Lab" found that eScan had blocked part of the malicious actions, including writing update servers to the hosts file. However, this did not help preserve the functionality of receiving updates: when attempting to do so, a message was displayed, as shown in the screenshot above. And although it says that "the operation was completed successfully," in reality, no updates were installed.
The next stage of the payload was responsible for bypassing the built-in Windows protective functionality called Antimalware Scan Interface (AMSI). To achieve this, one of the AMSI functions called AmsiScanBuffer was patched in such a way that its execution always returned an error. Then the malware identified the list of installed software on the system and terminated its operation if it detected a number of other protective solutions, including, for example, products from "Kaspersky Lab." Regardless of the successful completion of this check, information about the system was sent to the attackers' command servers. The final stage of the malware's execution modified one of the text files of the eScan antivirus so that the program interface created the impression that updates had been downloaded very recently.
Another feature of the attack was the reservation of methods for executing malicious actions at the final stage. This was done both through the hacked antivirus and separately — via the Windows Task Scheduler. What exactly happened after all the preparatory operations is unknown since the malware was separately downloaded from the command server and was not analyzed. The removal of the malware was complicated by the fact that the built-in update functions of eScan were rendered inoperative. On the other hand, detecting the fact of the hack was quite easy, including, for example, through the logs left by the malicious module during its operation and saved in the file C:\ProgramData\euapp.log.
What else happened
Another publication by experts from "Kaspersky Lab" analyzes the latest toolkit of the HoneyMyte group, also known as Mustang Panda and Bronze President.
Google published a review of new protections in Android starting from version 16. In particular, it discusses a set of technologies (including the use of AI) that help identify the common phone theft that occurs in several countries when it is snatched from someone's hands on the street. If such a situation is detected, the phone is instantly locked. In Brazil, this feature will be enabled by default on all newly activated Android devices.
Meanwhile, in the WhatsApp messenger, a set of Strict Account Settings has been implemented, which is compared in BleepingComputer to the Lockdown Mode on Apple smartphones. These two highly secure (and relatively inconvenient for regular users) modes share similar features, such as disabling previews of sent links and blocking any attachments sent by strangers.
An emergency patch from Microsoft closes an exploited vulnerability in Microsoft Office. The issue CVE-2026-21509 can only be exploited locally: to use it, an attacker must send a malicious office document to the user and convince the victim to open it.
In Microsoft server OS, the outdated NTLM authentication method will be disabled by default in future Windows releases.







Write comment