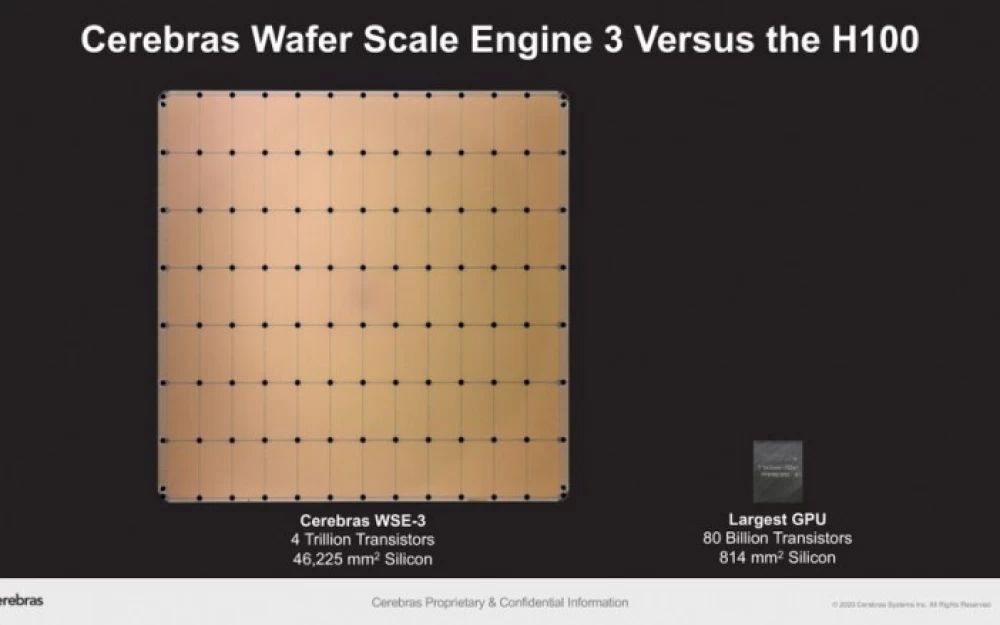
How to store data without cloud services: advantages of QNAP network storage for home and business
Modern technologies and the development of digital services make us increasingly dependent on data preservation, their security, and most importantly, accessibility.…