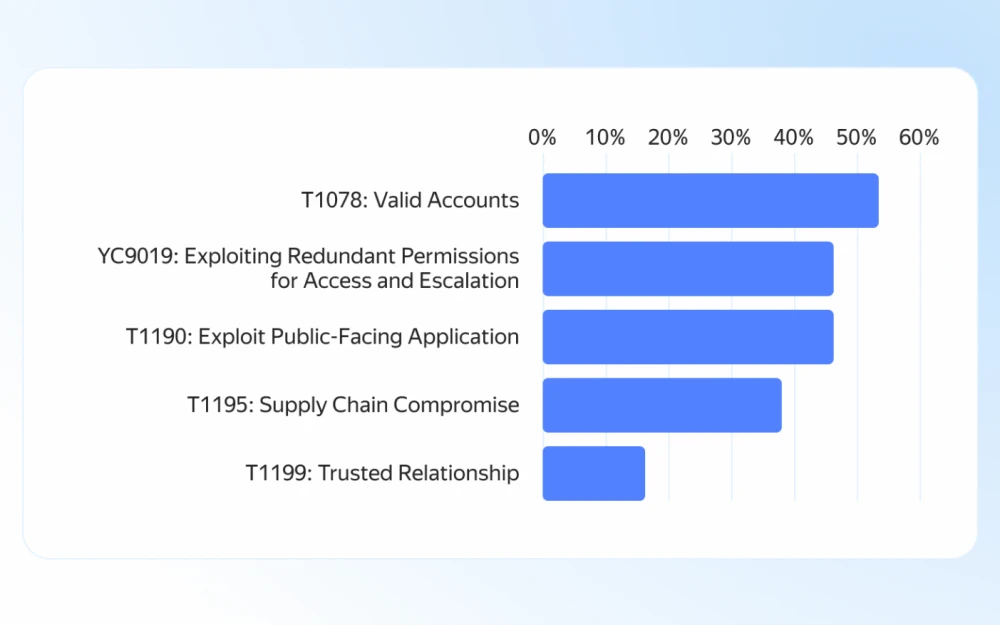
Internet vs CAPTCHA: is there a future for tests like “find all pictures with bicycles”?
CAPTCHAs, which are supposed to “separate” humans from bots, have become a real headache for users. Sometimes you don’t just have to pick a traffic light or a “zebra…