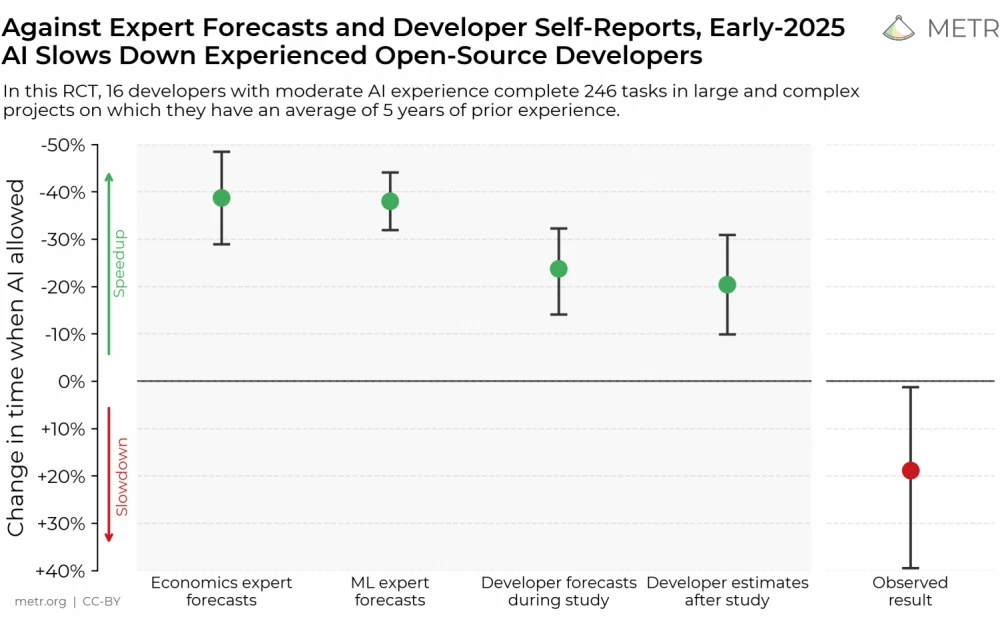
Programming and training of a bipedal mini-robot in the robotics club of Sber's Robotics Center
Through this project, we invite the university community of Moscow — students, master's students, doctoral students, lab assistants, professors, and lecturers — to gain…