- Security
- A
Hiding VMware from malware
Methods for detecting malicious code are improving, as is the malicious code itself. In the past, antivirus systems used signature analysis to detect viruses, but now this approach is clearly not enough. Now, to check whether a particular file is dangerous, it is necessary to run it and see which OS components it accesses, what it does, whether it tries to register itself in the startup, etc.
For this, there are special solutions called sandboxes. Here everything is quite simple. To check the file, a virtual machine instance is created, for example, under Windows 7, in which the main office applications, Acrobat Reader, mail client, browsers, and others are already installed. Then, special hooks intercept various calls made by the tested file and analyze them. As a result, the sandbox will detect the file's access to the registry, actions with other files, use of libraries, and much more. It would seem that a sandbox is an effective means of detecting malicious code, but it is not so simple. The fact is that the flow of files to be checked even in a medium-sized organization can be quite large, and we cannot check one file for too long. As a rule, the duration of the check lasts from two to five minutes.
This is what malware developers take advantage of. They can artificially delay the start of the payload, that is, the malicious code, so that the analyzer simply does not wait and ends the analysis earlier with the verdict that the file is safe.
Also, enemy software developers can set a counter for application launches, and malicious activity will start, for example, only on the third launch of the file. Naturally, the sandbox will not launch the same file several times and suspicious activity will not be detected here either.
Finally, the behavior of the malware will change if it detects that it is running in a virtual environment.
One way or another, if we have reason to distrust our sandbox, we need to analyze the suspicious file ourselves. The easiest way to do this is to deploy our own virtual machine, in which we can conduct the analysis using various tools. And here arises the first problem, which we will discuss further. We need to assemble our virtual machine in such a way that the malware does not feel that it is being restricted by the virtual environment.
In this article, we will talk about virtualization based on VMware Player.
Complicating the installation
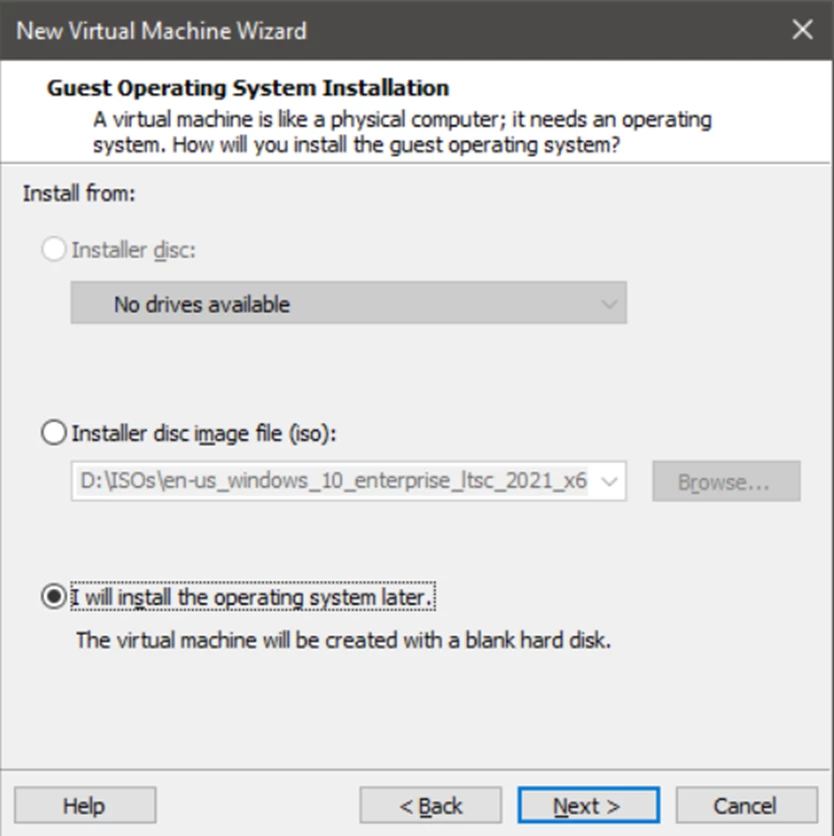
Usually, when creating a virtual machine in VMware Player, we immediately specify the ISO image that we want to use to install the system. However, such a quick installation will result in the installation of VMware Tools, which is exactly what we do not need. Instead, select the option to install the operating system later.
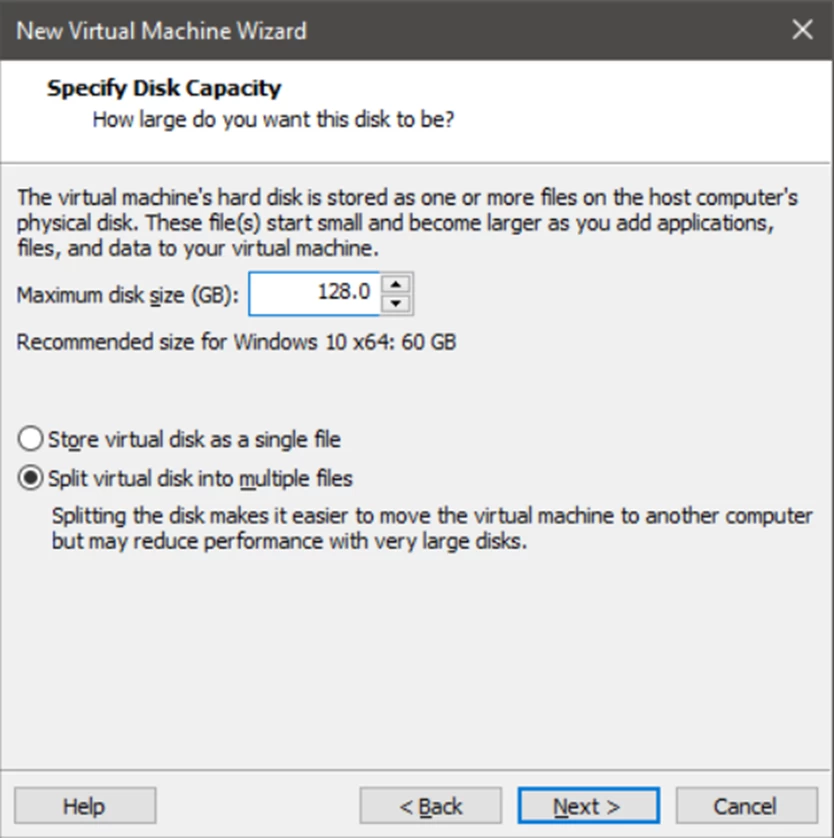
Next, we need to make our test machine as similar as possible to a real computer. To do this, first of all, we need to specify a realistic disk size. Of course, for a regular test machine, we could get by with 20-30 GB, but on a real machine, disks always have a larger volume.
So we will specify at least 128 GB. At the same time, the actual space consumed by the virtual machine files will generally be less than this volume, as not all of this disk space will be used.
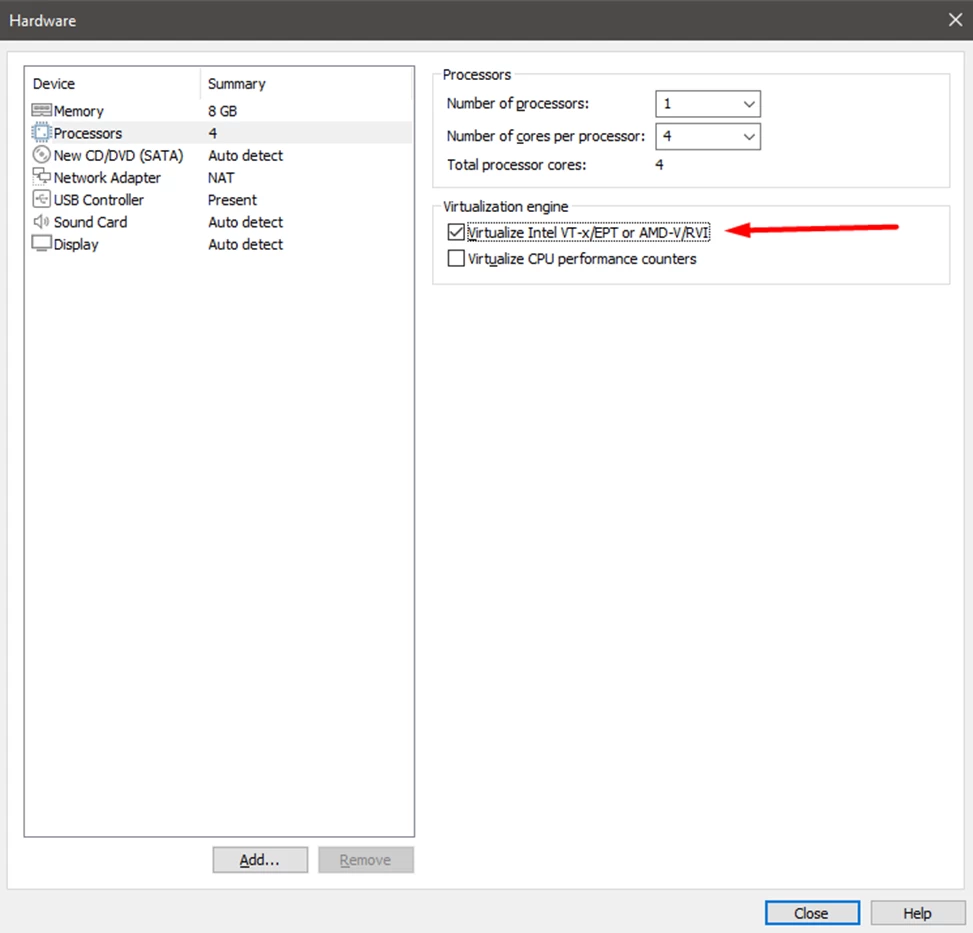
In the next step, we will specify the use of Intel or AMD virtualization.
Next, we can complete the virtual machine creation wizard, and now we will adjust the settings of the created VM.
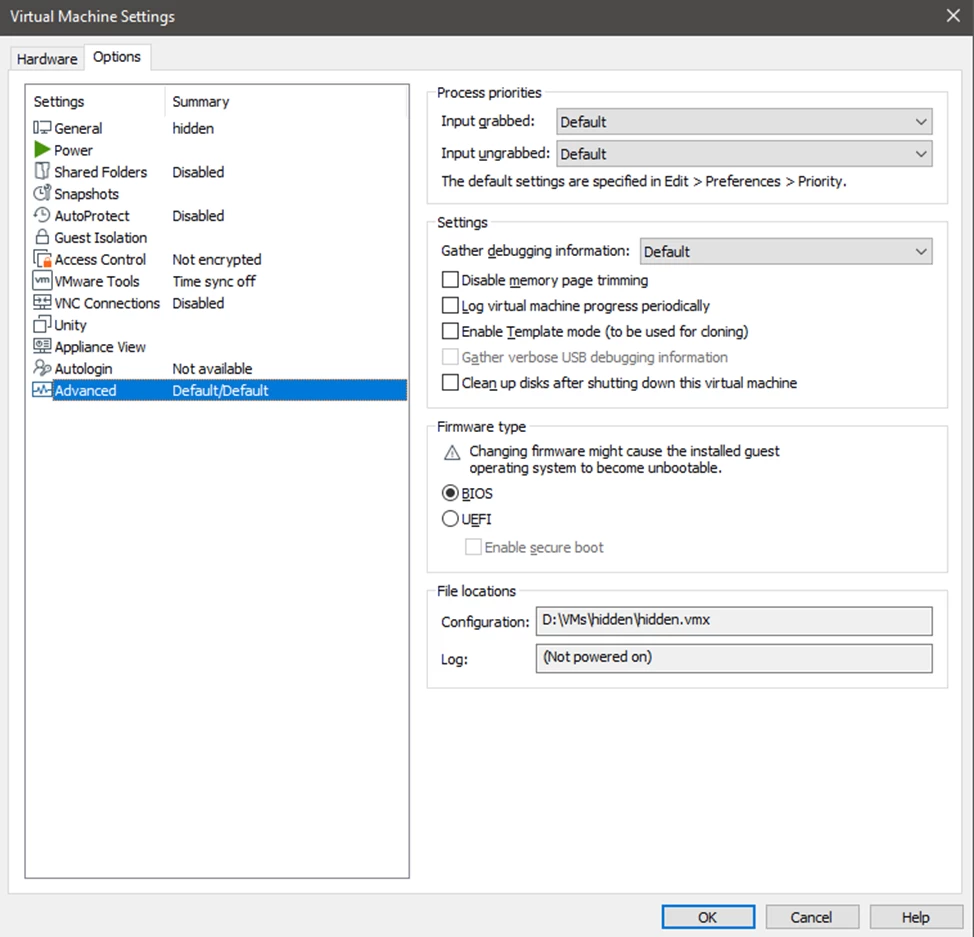
In particular, we will specify the use of BIOS as the Firmware type.
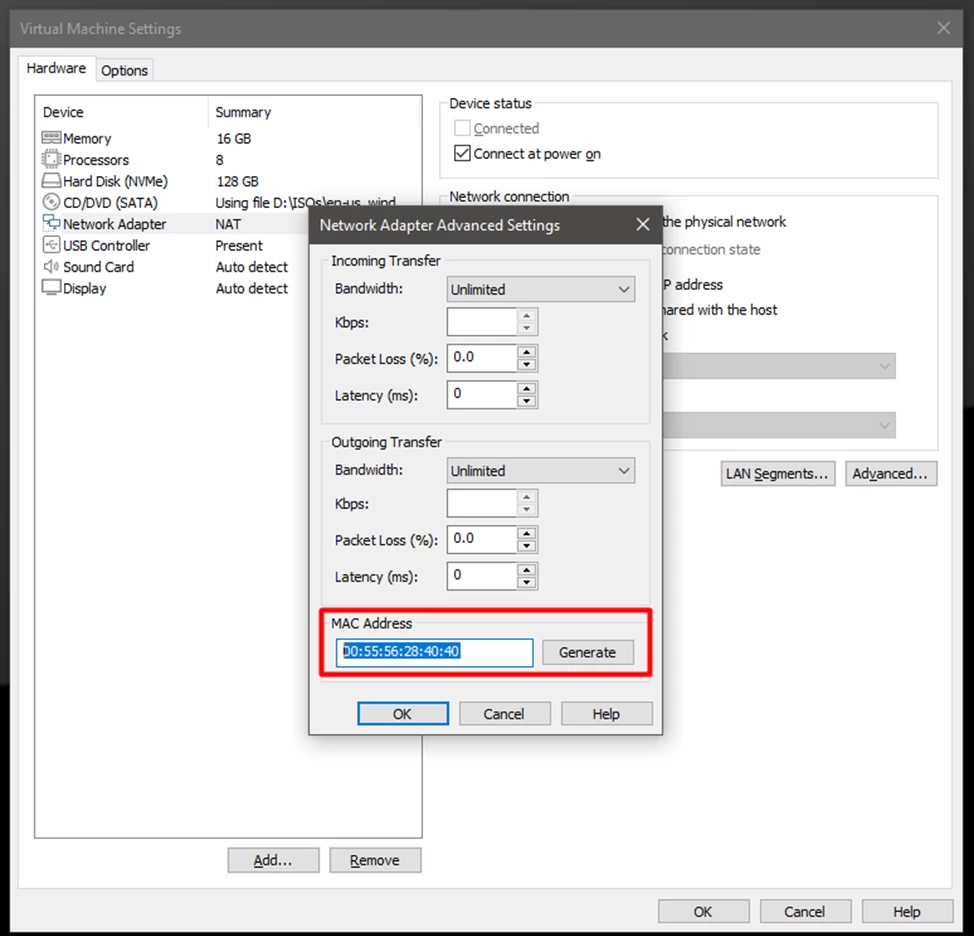
It will not be superfluous to make some changes to the network interface parameters. For example, it is worth changing the MAC address. Recall that the first three bytes in the MAC address are the manufacturer. Accordingly, our MAC should not start with 00:05:69, 00:50:56, 00:1C:14, or 00:0c:29.
Change the address in the network adapter properties.
The following actions require changes to the BIOS image files.
Making Corrections to the BIOS ROM
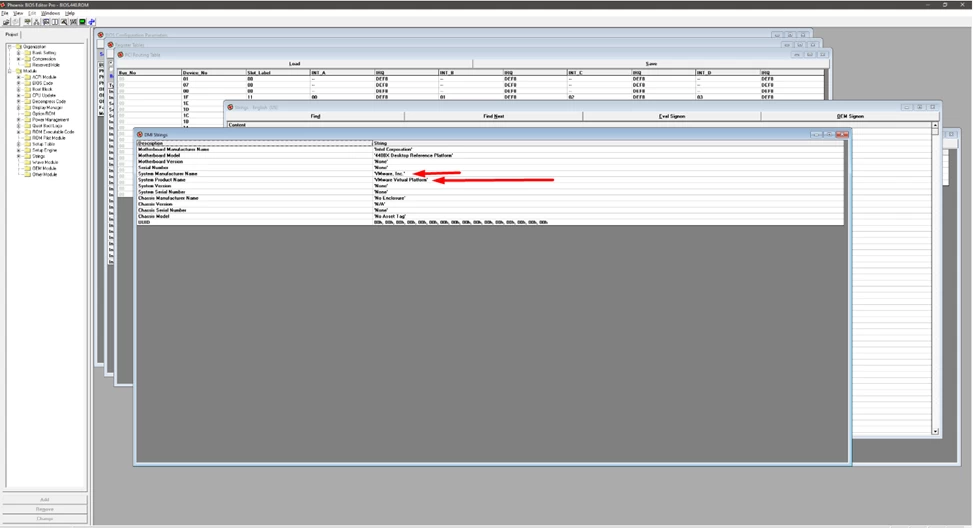
The VMware BIOS ROM contains strings related to VMware and virtualization. Let's fix this. In general, editing the BIOS image is quite simple, although not as simple as hex editing the ROM file, as this can lead to internal checksum corruption in the file and make the image unusable.
It is best to use the Phoenix BIOS editor, which can be easily found on the internet.
The ROM file is located in the VMware Workstation/Player installation directory, specifically in the x64 subdirectory. By default, this is C:\Program Files (x86)\VMware\VMware Workstation\x64. Be sure to make a copy of the file before making any changes.
Accordingly, open the file in the editor, find the "DMI Strings" window, and change the values so that they do not contain "VMware" or "Virtual Platform".
Editing the VMX File
Go to the directory where your virtual machine is stored. There should also be a file named
Next, add the following line to the end of this file:
bios440.filename = "C:\
To complete our setup process, let's adjust a few more parameters. First, disable the hypervisor presence message when executing the CPUID instruction used to obtain processor information.
hypervisor.cpuid.v0 = "FALSE"
Disable a few more instructions that may later help malware understand that it is in virtual reality.
monitor_control.restrict_backdoor = "TRUE"
monitor_control.disable_directexec = "TRUE"
monitor_control.disable_chksimd = "TRUE"
monitor_control.disable_selfmod = "TRUE"
monitor_control.disable_ntreloc = "TRUE"
monitor_control.disable_reloc = "TRUE"
monitor_control.disable_btmemspace = "TRUE"
monitor_control.disable_btpriv = "TRUE"
monitor_control.disable_btinout = "TRUE"
monitor_control.disable_btseg = "TRUE"
isolation.tools.getVersion.disable = "TRUE"
isolation.tools.setVersion.disable = "TRUE"
isolation.tools.getPtrLocation.disable = "TRUE"
isolation.tools.setPtrLocation.disable = "TRUE"
Under certain conditions, there is a possibility that the hypervisor will attempt to use the unpatched, original version of the BIOS at startup. To prevent this from happening, we will enable SMBIOS copying from the host.
smbios.reflectHost = "TRUE"
Now you can proceed with the operating system installation. After installation, it would be useful to check the system settings, drivers, and registry to ensure that VMware or anything related to virtualization is not mentioned anywhere.
Conclusion
Malware research is quite a laborious task, and proper configuration of the tools used can significantly assist in the study and reduce time costs.
You can gain more up-to-date skills in information security through practical online courses from industry experts: in the catalog you can see the list of all programs, and in the calendar — sign up for open lessons.









Write comment