- Security
- A
Top news in information security for January 2026
Hello everyone! We summarize the first month of the year with a news digest. January opened with a series of vulnerabilities in the n8n automation platform, which continue to be disclosed. NotePad++ revealed a compromise of its update infrastructure by state hackers; eScan's infrastructure was also compromised.
The integration of LLMs in 2026 is losing ground among users: media is promoting scripts for removing AI features from Win11, and Microsoft is rejecting their widespread implementation. In China, they are radically addressing the issue of scam centers, executing 11 people from a criminal clan in Myanmar, a Bitfinex hacker has been released literally and is targeting cybersecurity, while ClickFix is still with us with new variations. Read about this and other interesting news from January below!
The Infinite Loop from n8n
In the first days of the year, n8n, the workflow automation platform, disclosed yet another vulnerability rated 10 out of 10, leading to RCE and arbitrary file writes. This was already the fourth critical CVE disclosed in n8n within a couple of weeks.
The freshest one is called Ni8mare, revealed the day before — N8scape, along with another unnamed ten. As usual, if a vulnerability is not given a memorable name, the chances of it gaining hype and patches being rolled out decrease sharply. Ni8mare, unlike the others without authentication, predictably leads to the compromise of an instance with admin rights. N8scape allows for bypassing the sandbox and executing arbitrary commands.
On the plus side, these are all responsible disclosures fixed in last year's versions of n8n CVE — we endured as best we could until the end of the holidays. On the downside, not everyone took care of the patches, there was a PoC available, and approximately 100,000 vulnerable versions were counted online. So, for those particularly unlucky, the workweek began with a bang.
Over the last holiday weekend in January, the number of vulnerable instances decreased — but from 100,000 to 60,000. And these were just the first of the disclosed and subsequently fixed vulnerabilities in January.
Next in n8n, a couple more vulnerabilities were closed, critical and high, both under RCE. Did you think Ni8mare was over for the service? That's what makes it a nightmare. On the plus side, both require auth.
CVE-2026-1470 has authentication but from any user and is serious enough to score 9.9 on CVSS; the second CVE-2026-0863 scores 8.5. Both vulnerabilities allow for code injection and sandbox escape, with the first permitting full compromise of the instance on internal configs.
Essentially, familiar Python problems in the sandbox: due to a minor change in the interpreter in Python 3.10, sanitization has slightly broken. So, if Ni8mare didn't impress some users, there's a great reason to belatedly update based on January's results.
And finally, recently another critical CVE was disclosed. CVE-2026-25049, with a score of 9.4 on CVSS, circumvents the fix for CVE-2025-68613 released at the end of December. Closed in the patch from January 12 — those who updated did well.
Like the original vulnerability, this one involves authentication but has low privileges and a sandbox escape with instance compromise. There is a user — there is full access. The patch did not account for all the ways JavaScript allows access to object properties — accordingly, after a couple of days of poking at it with a stick, the patch was circumvented.
Are the developers grateful for the flood of reports over the past few months or just happy that the hot January is over — history remains silent. And users of n8n continue to receive cryptic messages. What could they mean? Username, if you are reading this, we have already had our tenth CVE for January. We are trying a new method. We do not know where this message will reach you, but we hope it works. Please apply the patches.
LLM News
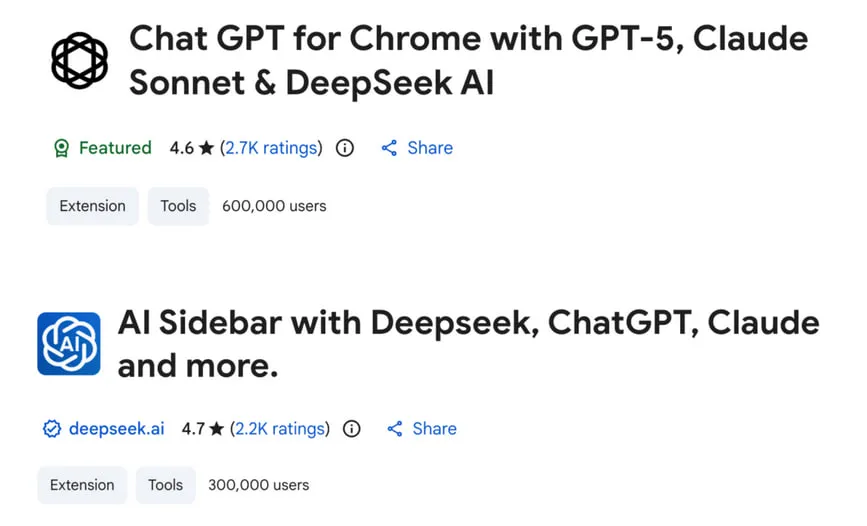
News setting the tone for 2026: in January, a couple more extensions in Chrome were caught stealing chats with LLMs. They mimic legitimate ones that add a sidebar for AI chats, and they are comparable in downloads — nearly a million users.
The names on the screenshot — check your subscriptions, lovers of chatting with copy-pasting. Besides chats, the extensions steal links from tabs — all of this goes to C2 every 30 minutes. Formally, this is described as "anonymous analytics data." In practice, the collected data can be sold not only to data brokers but also monetized for corporate espionage: how many of the million users installed malware on work machines with corporate URLs and fed internal documentation to LLMs — try to guess.
A separate term has already been designated for chat theft in this format — prompt poaching, and such functionality is quietly being adopted by more and more browser extensions. Those who do not want to fill someone else's pocket at the expense of their chats should not forget about digital hygiene.
And more signs of 2026: in a specialized publication, scripts were promoted for debloating Win11 from AI features. They are called Remove Windows AI. 10k stars — people are voting against Copilot and the company with the script.
The support from the president of Signal adds some fire, appreciate the wording: “Infrastructure for harm reduction and countering the alarming deployment of AI agents, the most reckless deployment among the current ones.” The developers themselves are not shy about their expressions: "removing ALL AI features to improve UX, privacy, and security."
In other words, the resistance against the deployment of LLMs in every nook and cranny is going mainstream: earlier, de-bloating was the concern of a few decent gentlemen forced to use Win products, but now it is attracting a wide audience. By the end of 2026, the word of the year might be recognized as AI-fatigue, which is the exhaustion from AI. But here, the main thing is that it should not be an AI bubble — this is a possible spoiler for what’s to come. And there may not be little for anyone.
The users' resistance to the imposition of AI has become so widespread that interesting news emerged by the end of January: insider rumors went around the network that Microsoft has surrendered on the AI front. The approach to integrating an LLM product, identical to the natural one, will become more restrained.
This should affect key AI products of Microsoft — Copilot and Recall. User dissatisfaction has become so widespread that it reached the jackets in high offices: graphs showed downward arrows, important palms began to sweat nervously, and a directive was sent down to the teams to tone down their love for AI.
Details are still lacking, but they claim that AI features will stop being shoved into all sorts of software, integrations will be reduced, and they will become less invasive where their presence makes sense. Overall, it’s not surprising: scripts for their removal are being publicized not only in specialized but also in mainstream publications. So we have won, chat! But hardly for long — Copilot will strike back.
And closing the topic of LLMs, the maintainers of cURL had a long-awaited event last month: they are shutting down the BB program to stop the flow of AI sludge disguised as reports. The poor souls endured until January 2026 — one can only envy their endurance.
For context, in a week in January, the URL received seven reports on H1 over 16 hours; as a result, it was determined that there were no valid vulnerabilities in them. Meanwhile, in the incomplete month of January, they have already received 20 reports. So in 2026, Stenberg firmly says “No” to AI-generated fluff in bug hunting: according to the plan, all mentions of BB and H1 were supposed to be removed from the documentation, and the program was to be shut down by the end of the month. The team hopes that they will be informed about real vulnerabilities even without payouts, as they simply cannot handle the flow of nonsense from rising stars of bug hunting from distant countries.
Stenberg began complaining about fluff back in 2024, and not without reason: examples of reports fueled by LLM and pure enthusiasm here. Few can endure years of glitchy copy-paste from ChatGPT.
ClickFix is still with us
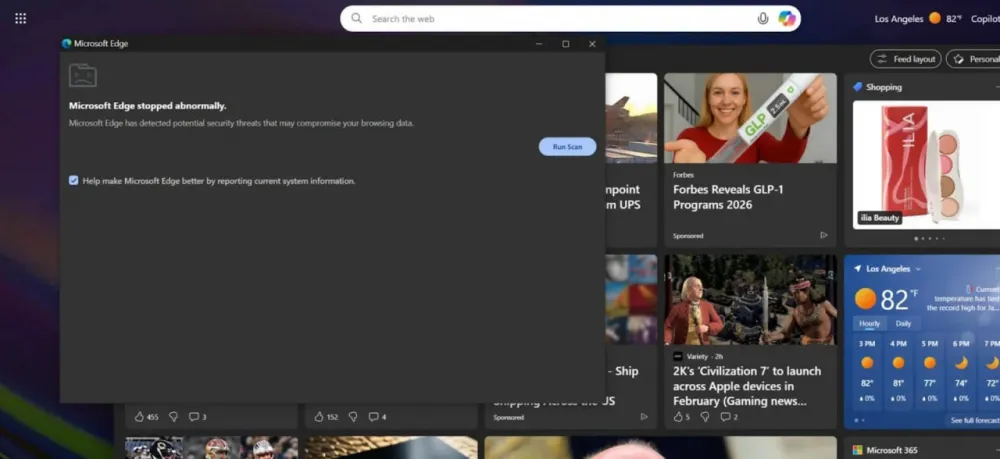
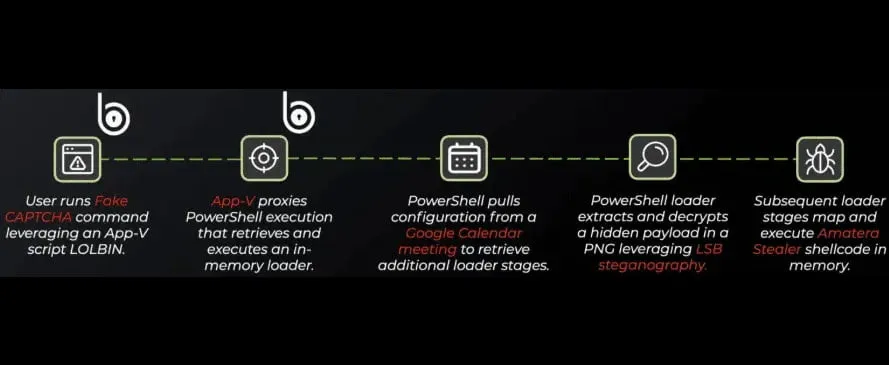
In the New Year, with new variations on the ClickFix theme. Fake extension -> browser crash -> warning window like a browser -> ClickFix. What do you think of this creative chain?
The application is disguised as an ad blocker, with code looping through 'chrome.runtime', leading to the browser crash. The problem window also appears legitimate and urges the user to fix security issues and help make the browser better. How can one refuse such a thing? Then there's copy-paste with a malicious script. The extension has a delay of 60 minutes, so that the perceptive user doesn't start to suspect anything, but overall it looks convincing for an advanced PC user — hard to pick apart.
Judging by the trends, 2026 will also proceed in the format “>Original attack >Looked inside >This is ClickFix”. So as a thought experiment, one could come up with a couple of new vectors — whoever gets mentioned in the news later wins.
ClickFix is so good that it can be used to study malware delivery methods and evasion of detection — soon variations will gather them all. In the latest version, there was a launch through a script of Microsoft Application Virtualization in Win Enterprise — a rare novelty.
App-V scripts are often not encountered in such contexts: enterprise solutions are hard to find, and a normal SOC would still catch any noise from it. The abuse of App-V was highlighted by Chinese hackers – they love everything obscure in Windows. But ClickFix is now instead of a textbook: there’s cool social engineering and niche things for every taste.
As a bonus, this version includes steganography and pulling configuration from Google Calendar – why not? In the dry residue, there's another signed script that needs to be cut. And a reminder that if Microsoft releases something, someone will definitely abuse it.
Compromise of the update infrastructure at Notepad++ and eScan
In January, the developer of Notepad++ revealed details of a recent mysterious compromise of their update system. The mystery was solved easily: it was compromised by state hackers. Guess whose – it's all obvious here.
The attackers had access to the hosting infrastructure where the update servers were located, and redirected the traffic to the attackers' infrastructure for delivering malware. The scale and timeline of the compromise are consistent: the hack occurred in June 2025 – six months before it became known.
The hosting was open until September 2, but due to credentials to internal services, access was maintained until December 2. By that time, the provider decided to take control of its own fate and infrastructure, took measures, and shut it down. An investigation is ongoing, so perhaps the revelations are not over yet. But already, the picture is quite telling – the dark genius of the cyber underworld is stronger than ever.
But APTs do not live by Notepad++ alone: the supply chain attack through the update infrastructure also affected the eScan antivirus. The incident occurred a couple of weeks ago, and the source is not named.
Activity was noticed at Morphisec, which reported the compromise of eScan's infrastructure for delivering malware to the endpoints of companies and users worldwide. Here, the alarmism of researchers sharply diverges from the official statements of eScan: nothing serious happened to them; they detected everything themselves promptly and prevented it before any sensationalist characters came to inform them about it.
The situation began to get a bit out of control: eScan demanded that Morphisec delete posts on social media that tarnished its reputation (but not the blog post with the disclosure) and stop exaggerating the scale, with the legal department approaching. This had never happened before, and here it was again: a researcher clashed with a vendor over an incident, and after that, a real nightmare began on infosec Twitter.
Spy Drama Over Fast Pair
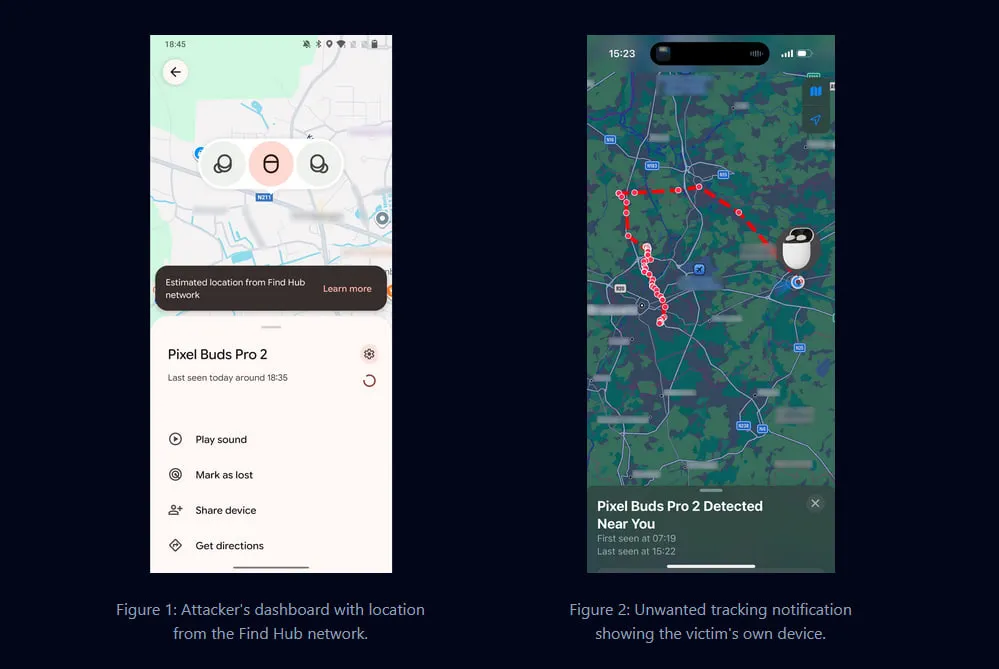
Read more about the most interesting vulnerabilities of January in our blog, but here we will mention one. In a dozen wireless headphones with Google Fast Pair, a vulnerability was discovered that allows forced connections to them. The standard has a bug in the pairing mode check, and many models connect even if it is not enabled.
The vulnerability was named WhisperPair and besides antics like launching audio and disabling sound, it allows for more interesting things. For example, access to the microphone and device tracking through FindHub. Overall, the problem is trivial, but it’s peripheral. So you won’t see patches, and rare users will apply them; plus, Fast Pair cannot be disabled — it's necessary today without workarounds.
Google acknowledged the problem and paid $15k for the bug bounty, a patch for their Pixel Buds Pro 2 is available, and the rest will be handled as it comes. As a bonus, researchers made a mini-video about the vulnerability, an amateur game with suspense and dramatic music can be appreciated here. It was 2026, and we drew attention to security holes as best we could.
Radical Solution to the Scam Centers Problem from China
In China, they are radically addressing the issue of scam centers: 11 members of a criminal family responsible for an online fraud hub have been executed. A scammer won’t press the button if you take away his hand! And not just his hand.
The Ming criminal clan hails from Myanmar, and they have a history of those very scam centers that have spread horror stories online: involving fraud, slavery, and even murders of those trying to escape. Chinese media claims that at their peak, the centers held 10,000 people. The Mings were captured back in 2023 and handed over to China, where they were sentenced to death last September. It is reported that this has been carried out.
At the same time, this is far from the only group awaiting execution — business colleagues from the town of Laukkaing face the same fate. A representative of the Ministry of Foreign Affairs confirmed that Beijing is ramping up efforts to combat fraud — the specifics of the region mean that both the scam centers and the measures taken are appropriate.
Liechtenstein tries on the white hat
The New Year has truly become festive for Liechtenstein. Ilya Liechtenstein: convicted for hacking Bitfinex in 2016, has been released early from prison. One of the largest crypto thefts in history, amounting to ~120,000 bitcoins, with Bonnie and Clyde from the crypto world according to Netflix.
Information about his release began spreading through social networks after a joyful post on eX-Twitter, but in reality, Ilya is serving the remainder of his sentence under house arrest. So he’s being a bit misleading. As, in fact, he is promoting a new persona: “Hacker on the path to redemption.” It’s a classic, especially considering his wife, who has already converted her bad reputation into a stylish media image. As usual, if you want to live [after having everything taken away], you need to be resourceful. Nevertheless, Liechtenstein continues to persuasively play out the arc of redemption and stated that he is looking for a promising crypto startup. Are you interested?
This comrade revealed this in a post on LinkedIn, where crypto enthusiasts are celebrating in the comments. The text reads briskly, and it's clear that a smart person wrote it — he marked all the key points to burst into the world of cybersecurity with a bang. He made wrong decisions and understood everything — checked. Money didn’t interest me; I wanted challenging technical tasks — checked. Standing alone in a black hat is a bit dreary for such a handsome guy, but helping the FBI with crypto cases was great — checked.
Gold, not a person — either he did it himself, or a PR manager worked hard on the text. Whether there’s something real behind the thought-out image — time will tell. But at conferences, under the applause of the audience, the satisfied Lichtenstein clearly still fits in.
Hack an InfoSec honeypot in 60 seconds
And finally, in the spirit of the past month, a festive story about the hack of an InfoSec firm with a happy ending. In early January, young talents from SLH announced full access to Resecurity’s systems; they grabbed everything: chats, logs, employee and client data, and more. But there’s a catch. It was a honeypot.
The post appeared in the channel of Scattered Lapsus$ Hunters on the first Saturday of this year. They hacked security professionals who dig under the young gods of hacking — how could they not brag? Only Resecurity calmly threw a link to a report from a week ago about the honeypot, which describes the adventures of the unfortunate hackers, including exposed IPs due to malfunctioning proxies. Of course, they were handed over to the relevant authorities.
In SLH, they hesitated, denied the obvious, and deleted the post. As a bonus, ShinyHunters got in touch with journalists and sheepishly reported that they had no part in this — blame their less savvy colleagues in hacker chats. So if you, username, ever feel awkward about mistakes in cybersecurity, you can take comfort in the fact that your year isn’t starting off like this, followed by breakdowns on YouTube with titles like “This noob got caught hacking a honeypot and went away for 5 years.”



















Write comment